The Multi-factor-authentication struggle? AND the solution!
The struggle for a Multi-factor authentication implementation is REAL and most of the time, really frustrating? Some frequently asked questions and answers below! Let’s change problem into a solution.
We don’t want to use Multi-factor authentication – it’s too complex!
- Ask the people in your organization if they use the same password as their corporate account for: Dropbox, Yahoo, Gmail, Facebook. Do they?
- I know, it’s really bad advice. But type your ‘old’ password in Haveibeenpwned.com Is it still ‘safe’?
- Do you have MFA on your Facebook account? Your iCloud account, You’re private mail? Is it that bad?
How to tackle the resistance!
- END-USER AWARENESS: There are a lot of organizations helping with a great case which can help your organization (including Microsoft) to communicate well. Communicate – make people understand WHY – support them – give them more!
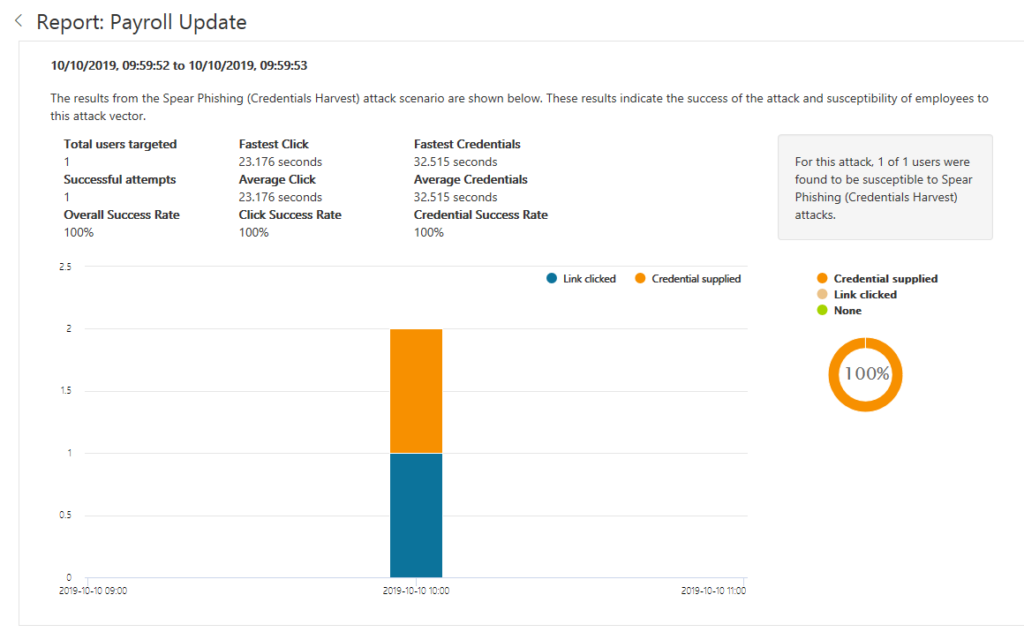
- MEASURE THE NEED FOR MFA: Measure the impact in your organization. And make people understand WHY. You could send out a ‘false Payroll update’ and measure how many people are entering their credentials. Make them aware that they did very good not entering their corporate credentials. Don’t punish people because they did. Help them to identify and understand phishing mails. https://protection.office.com/attacksimulator
- SELF-SERVICE: Give people in the organization the ability to get some pro’s because they ‘need’ to do MFA. For example: self service reset password possibilities. It could also mean that the workload of IT-teams will decrease because of self-service mechanisms. It’s nearly impossible (insecure) to deliver self-service without a trusted-second factor.
- MODERN MANAGEMENT: Bring all your devices in a Azure AD in a state where they are at least Azure AD Joined so users will have pro’s like Single-Sign-On in Microsoft Edge. Other browsers are possible, but requires a little bit more time.
- CONDITIONAL ACCESS: It’s simple to define a basic set of conditions where there shouldn’t be an second factor required. For example your work-environment. It creates a huge way of possibilities to have a better roll-out. Better have MFA with one condition then having no MFA at all.
- PASSWORDLESS AUTHENTICATION: Deliver passwordless authentication. It will help your users to not struggle with their password. Implementation guide here.
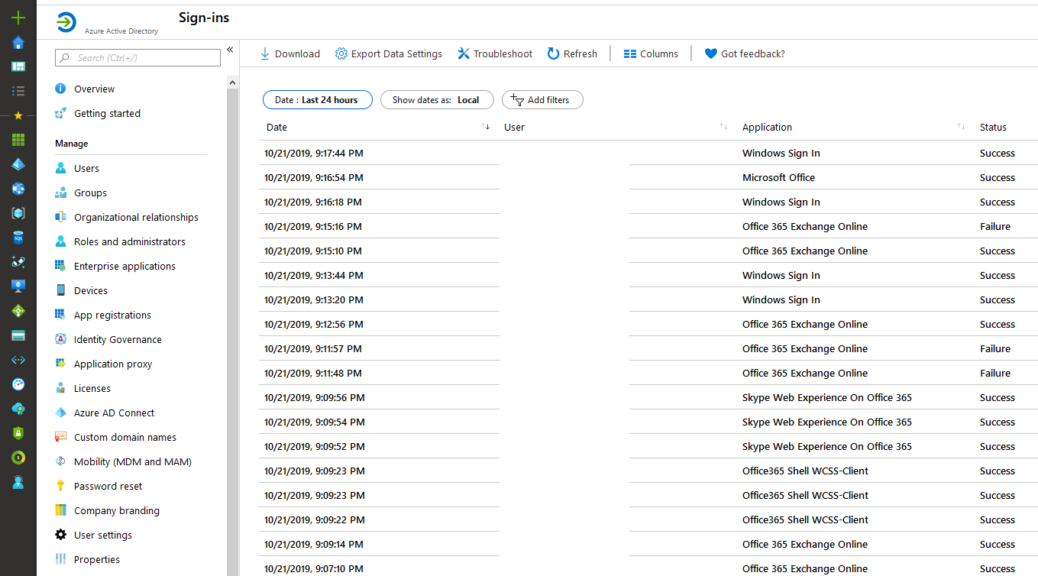
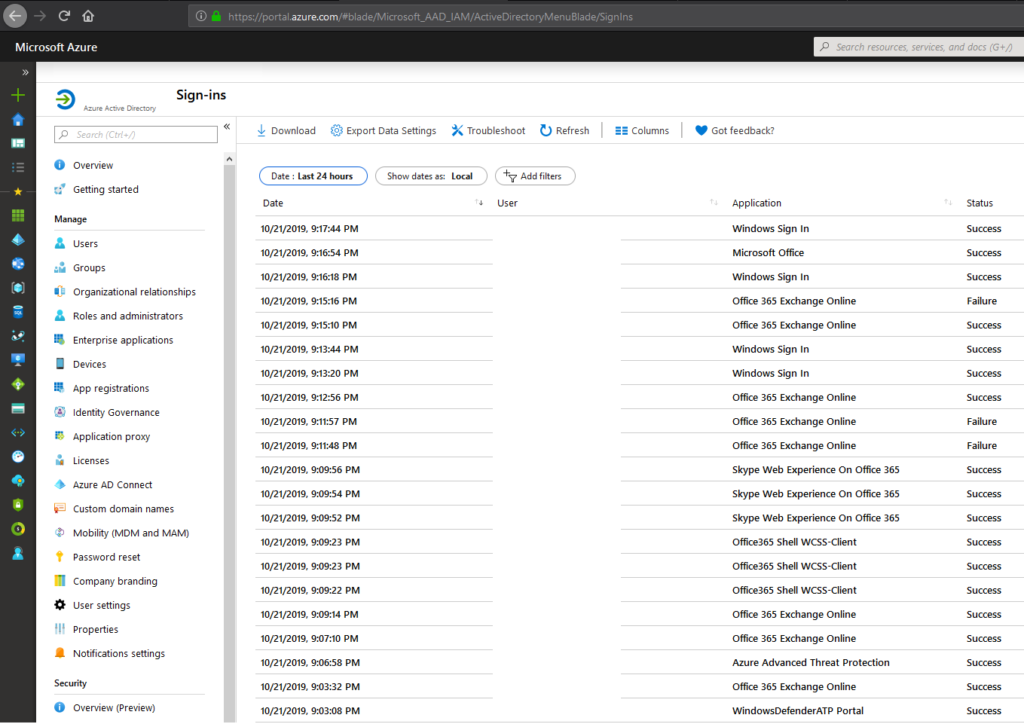
- MEASURE THE RISK(S): Login to your Azure AD portal and export all sign-in logs of the last 3 month. Filter on SUCCESS and filter on a country which your company is not in. (or filter out all locations you are in and work with the left-overs) You have leaked credentials. Mostly it’s clear after this simple exercise.
- MICROSOFT AUTHENTICATOR APP: You could just use SMS as a factor but don’t bother and use the Authenticator App
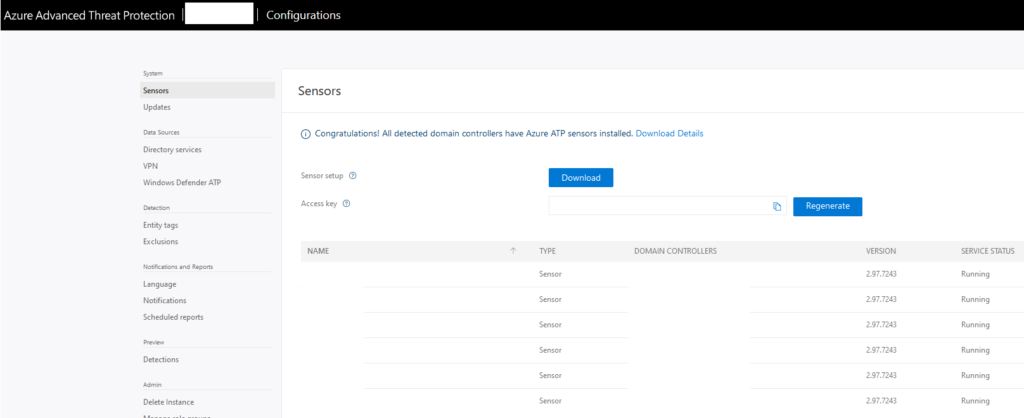
- AZURE ADVANCED THREAT PROTECTION: Work with Azure Advanced Threat Protection in a ‘Pilot’. This setup will cost you 60 minutes. Order a trial license of Microsoft 365 E5, go through the wizard of Azure ATP and add your domain controllers as a sensor.
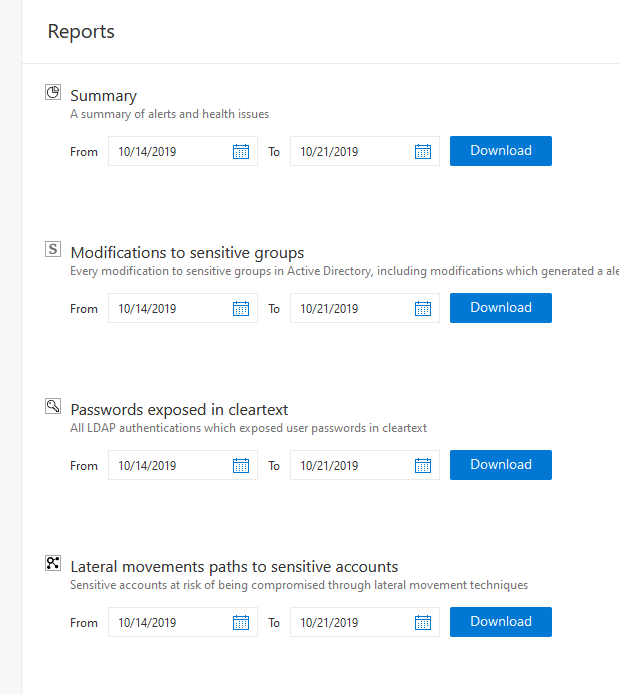
After 30 days go to the console and export: Passwords exposed in clear text, lateral movement paths to sensitive accounts. I’m sure you can find something happening without knowing! This will bring insights where you had none before.
- THIRD PARTY ASSESSMENT: Work with third-party tools to measure the security or cyber-security maturity of your organization.
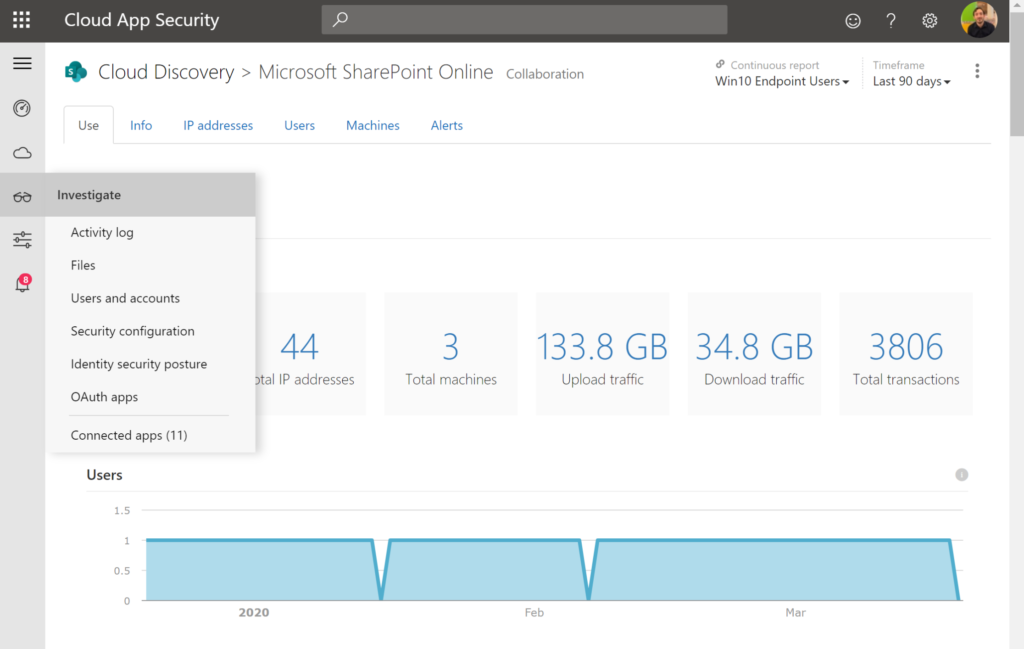
- CLOUD APP SECURITY: Measure that data is extracted to machines to understand the needs in your environment. This will prioritize the need of identity-protection (later data-control)
Advice to IT Administrators
- Maintain an 8-character minimum length requirement (and longer is not necessarily better)
- Eliminate character-composition requirements.
- Eliminate mandatory periodic password resets for user accounts.
- Ban common passwords, to keep the most vulnerable passwords out of your system.
- Educate your users not to re-use their password for non-work-related purposes.
- Enforce registration for multi-factor authentication.
- Enable risk based multi-factor authentication challenges.
Microsoft Password guidance didn’t changed in years. It’s still great!
It isn’t only commercial talk..
Microsoft sees over 10 million username/password pair attacks every day. This gives them a unique vantage point to understand the role of passwords in account takeover. 99.9 percent of attacks on your accounts can be prevented. (and it is not)
Side nodes
- MFA isn’t new: It’s there for almost 6 years.. https://www.microsoft.com/en-us/microsoft-365/blog/2014/02/10/multi-factor-authentication-for-office-365/
- It’s not an IT project: The people need to understand the change. And need help.
- Passwords Are Making You Weak: We need to act! Bye Bye Passwords: New Ways to Authenticate
- Your Pa$$word doesn’t matter: Facts and Figures
- One simple action you can take to prevent 99.9 percent of attacks on your accounts. – Microsoft Blog, they say. I’m sure it will make sence.