Actionable steps to decrease the risk of a Cyberattack
I’ve written some advice that almost every organization can follow to reduce the risk of being attacked by malicious actors. Awareness is increasing because multiple organizations are currently being breached.
In this article, I’m focusing on Cloud Security technology, which can be quickly deployed and provide instant insights and metrics to make security decisions. I always advocate for quick enrollment and activation because the threat is real. If you don’t believe it, don’t activate anything and just watch the insights. This will help you gain confidence and control to make effective security decisions.
A. How to decrease the risk of an attack on your users
In this chapter, I’ve discussed how infrastructure can affect user risk. One major risk is accounts with passwords, which can be mitigated by following the steps below. These steps can be implemented in just four hours.
1. Extend Active Directory to Azure AD for better insights in user risk!
“To sync your users to Azure AD, install Azure AD Connect and use directory and password synchronization to migrate all identities from your current environment to Azure AD. If you are a Microsoft 365 customer, your identities are already synced to Azure AD, so you can proceed to step 2 below.”
2. Prevent all Azure AD (Microsoft 365) Accounts for having the risk of being phished by activation Multi-Factor Authentication
First of all accept the fact that every password in your organization has been leaked. Read: Your Pa$$word doesn’t matter – Microsoft Tech Community
Security defaults will push MFA for every account and will disable legacy authentication that does not use MFA.
Also don’t forget to activate MFA of EVERY company service.
To enable security defaults in your directory:
- Sign in to the Azure portal as a security administrator, Conditional Access administrator, or global administrator.
- Browse to Azure Active Directory > Properties.
- Select Manage security defaults.
- Set the Enable security defaults toggle to Yes.
- Select Save.

3. Understand the user and credential risks in your ‘local’ domain
To understand the identity risk it’s best to consolidate the risks from multiple fronts. Applications are using AD or Azure AD authentication which creates insights in a attack attempt. If you create a Defender for Identity instance, all user sign-ins are brought to the Cloud for analyses. Create your Microsoft Defender for Identity instance quickstart

4. Activate a trial of Office 365 E5 to see the identity risk consolidated from multiple fronts
When you have the capabilities to understand the identity risks and see what is going on in your organization you are more capable of acting and make decision on additional levels as for example: Create a additional conditional access policy.
Activate a free 30 days E5 license first: Set up your Microsoft 365 Defender trial lab or pilot environment
Than activate Cloud App Security (Defender for Cloud Apps)
Navigate to: https://portal.cloudappsecurity.com and see the open alerts.

B. How to protect your organization from software exploits
Software could contain malware packages which could take over computers. Bad patched computers are increasing the risk of being attacked from within.
If you have activated an demo E5 license you could understand the risk of bad patching of software from one portal. This activation is more complex and requires more attention and reaction but it’s doable in some hours. Working on risks is another thing but start doing and choose pragmatic.
- First of all onboard all your devices in Endpoint manager. Hybrid or Cloud join doesn’t matter for the sake of security. (It matters for the future — I know)
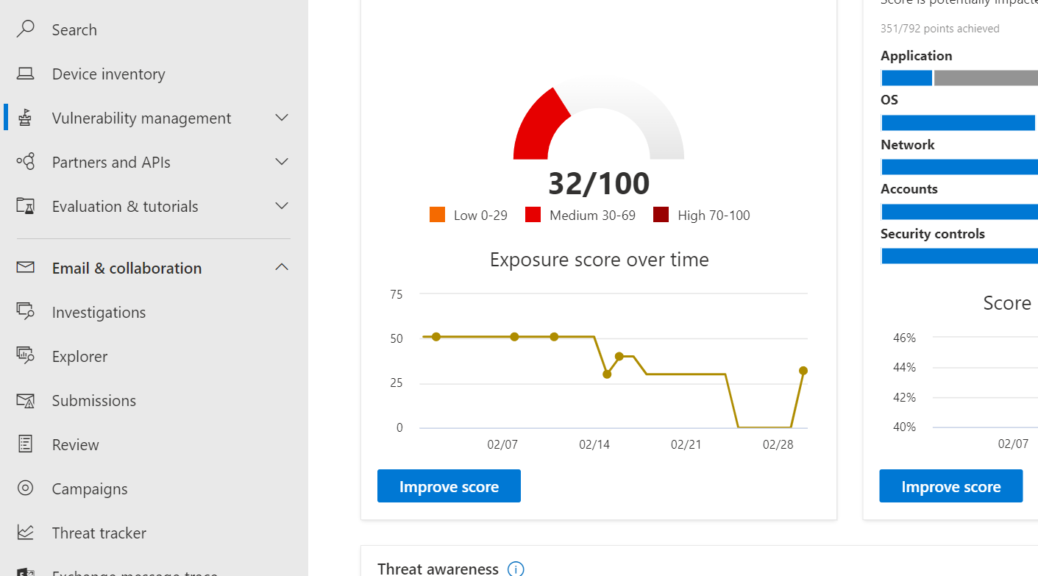
- Afterwards activate Defender for Endpoint to have insights in the pane as shown below.
- Work on the vulnerability management tab go to recommendation and start working on the most critical advices. Patch Windows, patch third-party apps.

C. Protect your organization from targeted phishing attacks
Phishing attacks are the number one attempt to get control of your organizational infrastructure. Don’t let actors go in from a stupid e-mail.
- Activate DKIM in your organization to keep your domain save from being used by malicious actors. DKIM for Office 365 activation tutorial.
- Enable SPF for your domains. Read: How to Build Your SPF Record in 5 Simple Steps
- Activate Defender of Office 365 to have more control and better phishing avoidance. Office 365 Security including Microsoft Defender for Office 365 and Exchange Online Protection

D. Don’t make exceptions and take insights seriously
If you have activated some Microsoft 365 E5 capabilities you can now work on 2 portals to understand what is going on in your environment. https://security.microsoft.com and https://Portal.cloudappsecurity.com.
Take care and stay save.
