Microsoft is delivering automated Security Operations (SecOps) for any organization
Hi There! I’m happy that you find your way to one of the series of blogs about Microsoft 365 Security.
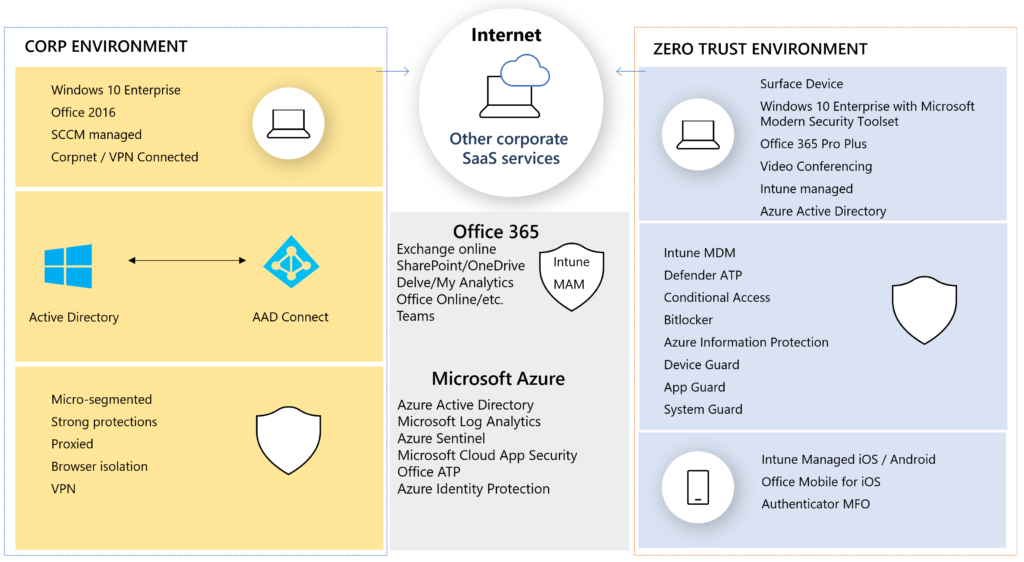
You may find earlier articles that will help to understand the scenario where I wanted to position this solution in. First Article: How to build your Zero Trust modern workplace with Microsoft 365. This articles is focusing on relevant security discussion that can help segment and isolate your broader IT landscape. Important to keep on track is the foundation of security maturity in Microsofts technological landscape. I mean, you need a baseline for doing sec-ops. You need to get things finetuned, get modern technology to be sure you’ve done all you can to decrease the respond actions. In the next article I’ve answered the technical high-level blocks to actual shift workloads to Microsoft 365 and Azure. Yes, I’m focusing cloud technology. And the reason why is written in this Zero Trust article.
At first it will be useful to get some context of the type of customers where I wanted to touch-base this Security Operation strategy.
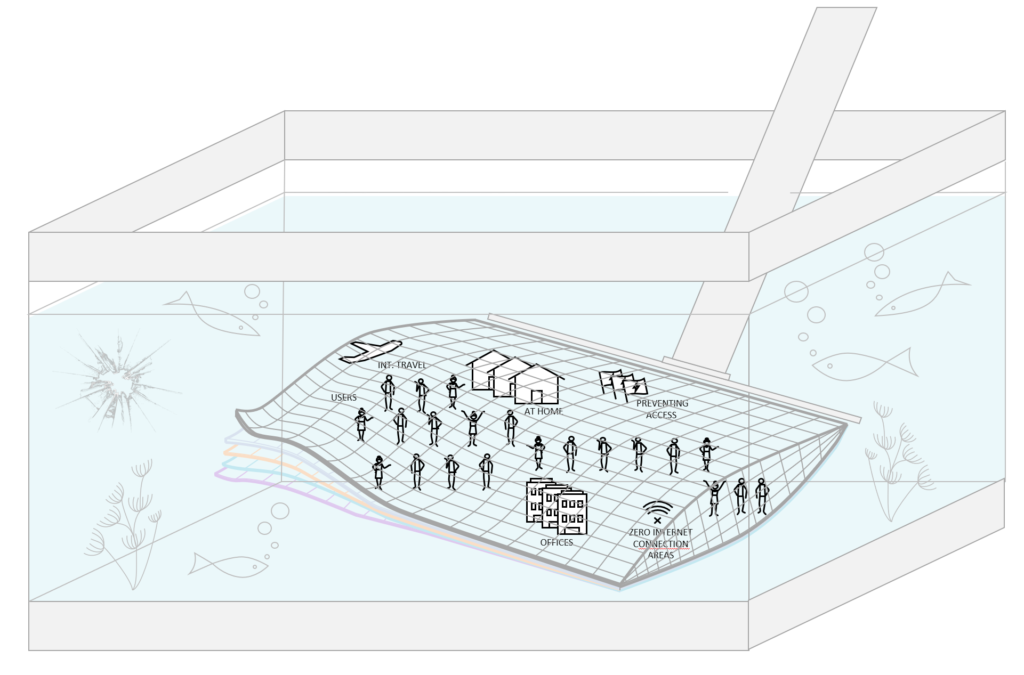
It’s time for change. “I’m not a Security specialist. Not totally aware of the technological part of it and my question is: ARE YOU?”
What I mean by this statement is that there is a lot cyber risks. The understanding is poor. The implementations are very basic. For example a SIEM solutions, companies are buying SIEM solutions and are doing nothing with it. But they have a SIEM. — Why do we think we need 10 people in a SecOps organizations if we don’t have a team now? — Why not make standards, fully automated. And run a SecOps operation different than hard-core teams (early adoptors)
In this article I’m providing answers on these topics. Feel free to give a reaction in the comment! Thank you for reading.
Customer focus
The customer focus of this article are small and midsize companies. Microsoft Cloud focused. Because their security maturity is relative low. Companies struggling with the fact that they cannot get their SecOps in order because: it’s too complex, too expensive, the maturity is low.. read on, below.
Framework for security operation
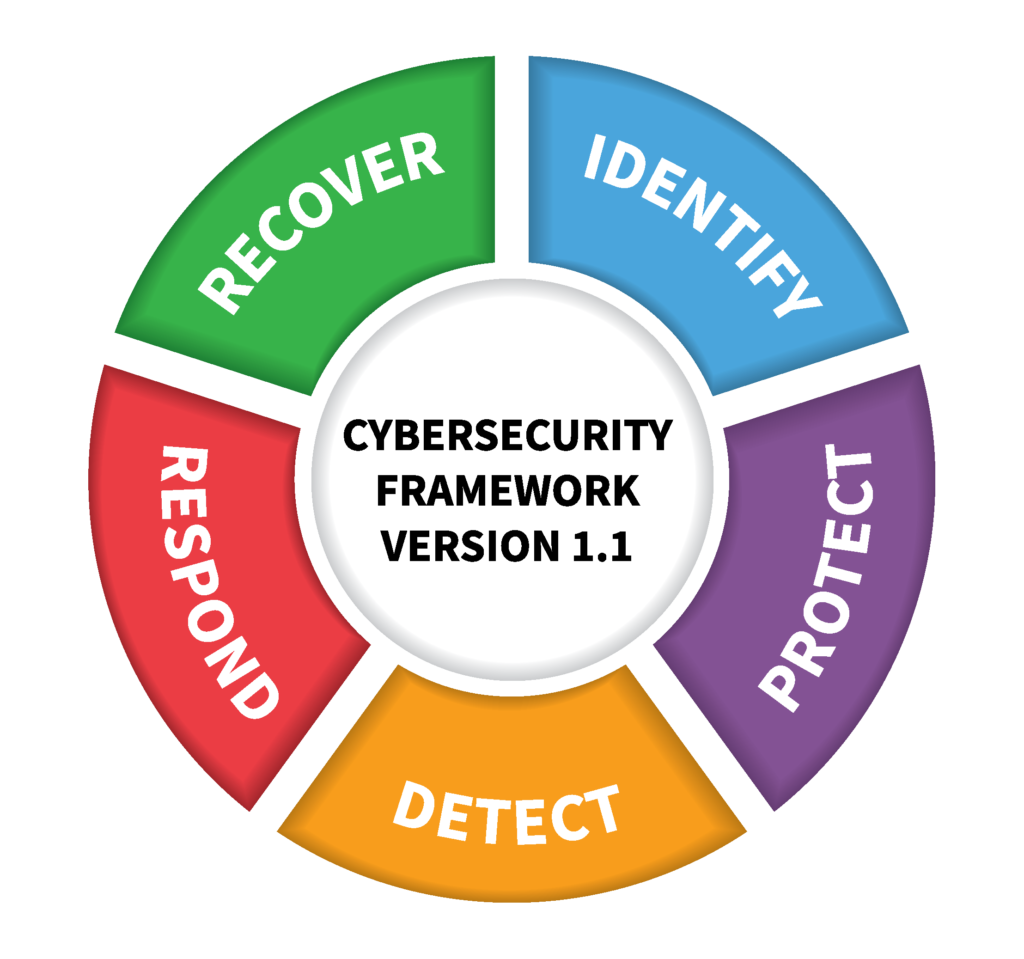
Every security operation need a plan and strategy when it comes to running the operation. Let’s make this simple. A Security Operation is using mythology which include:
- Identify: Who has access to information or privileged controls. Is it really you?
- Protect: Limit access, patch, upgrade, update, keep everything in order.
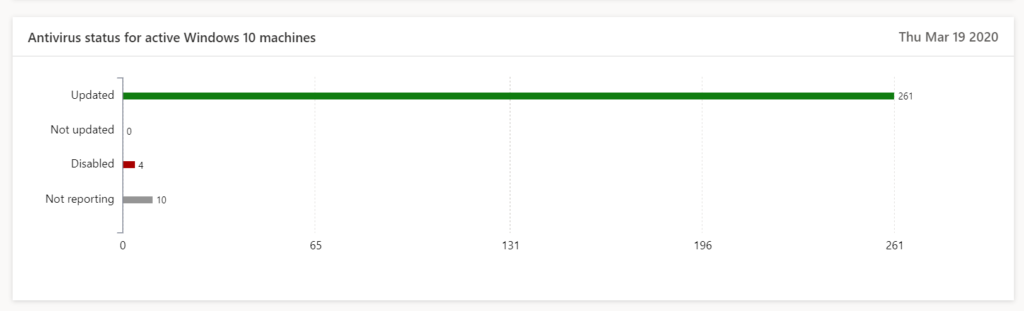
- Detect: Detect malware (Antivirus), monitor for anomalies for sign-in and device behavior
- Respond: Fast response for mitigation of the issue, or limit the impact. Clear Incident process
- Recover: Have a plan for disaster when security incidents are appeared. Backups, cyber insurance, and more technical important be able to recover from difficult damages done.
What is a Security Operation?
SecOps (Security + Operation) is the organization to facilitate and elaborate with focus on security in a organization. It has procedures, standards, process which describes the actions and effort it will put in running this Security operation.
SecOps is ‘always running’, with service-level agreements (SLA), possibly 24/7. SecOps is a team of people continuous working on Identify -> Protect -> Detect -> Respond..
Is a Security Operation overvalued?
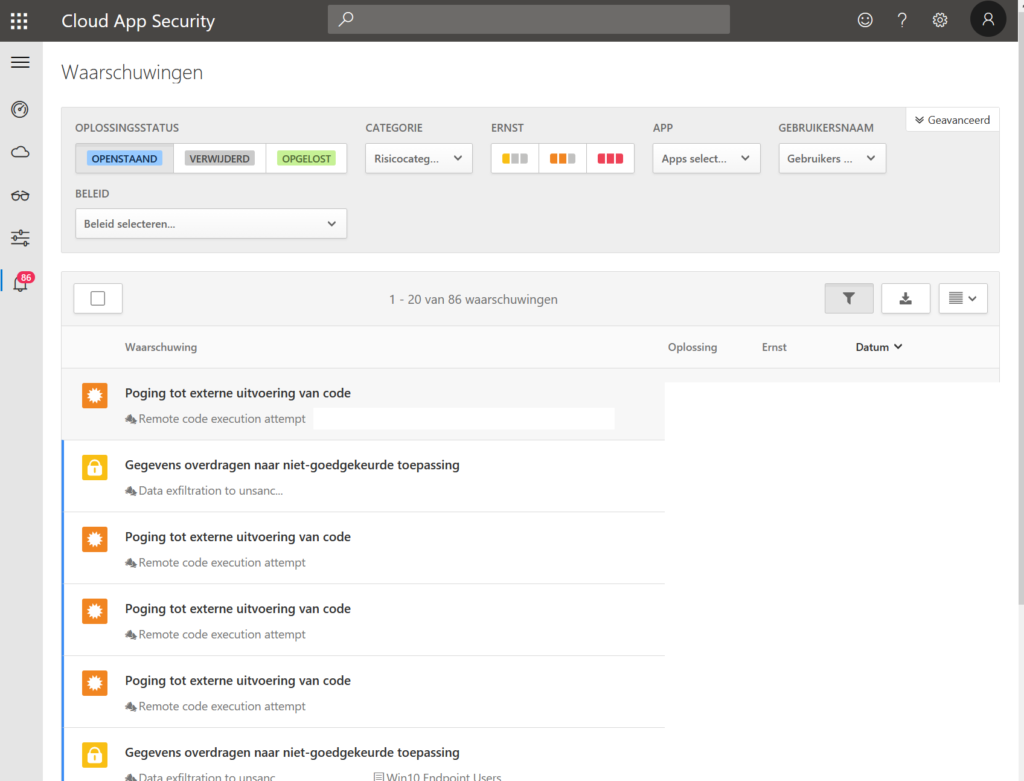
‘Security operation” is a container concept. Which doesn’t always make the same understanding. It has no real meaning like ‘digital transformation’. When people talk about SecOps they talk about their analyst running trough their SIEM. Others are talking about endpoint security, and most of the time (because of the relative impact) we talk about patching and updating of systems or incident response. — reactive.
SecOps is overvalued because there is a double understanding here. We have the top 5 giant companies as Microsoft doing SecOps for their customers. And you have your own SecOps team doing the already ‘segmented’ of ‘made ready for you’ actions. Our Security Operation teams needs to be in charge of the incidents when appearing. And all other tasks reactive on the somewhat predefined roadmap of Microsoft. It’s the only way – embrace the change.
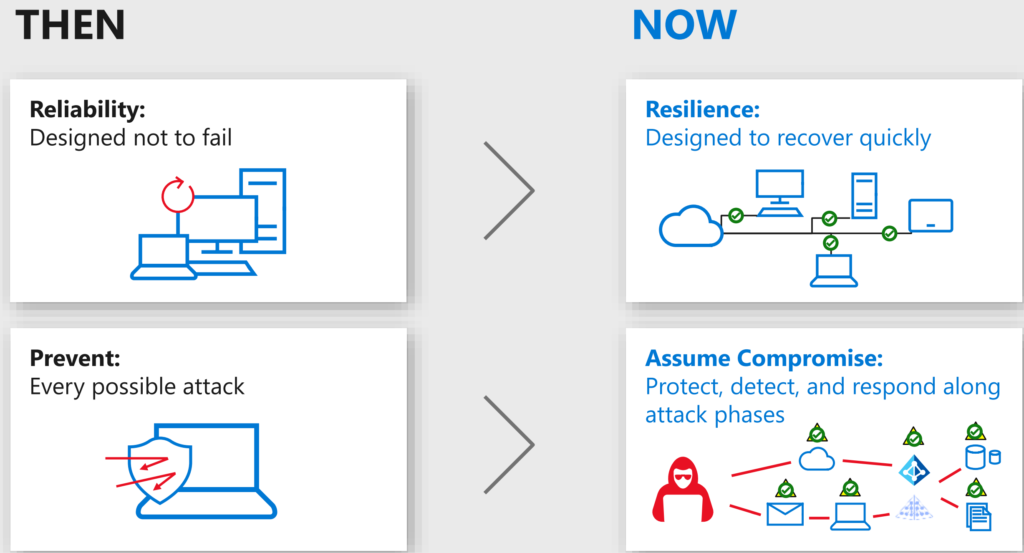
This shocking title is an invitation for you — to think about security operations in a different way. The world has changed since companies are shifting their workplace and workloads towards Microsoft 365. It became super relevant to think about the strategy and the usage in your organization of this service and infrastructure. How important is O365, CRM, M365, Networking, Applications in your datacenter.
“Focus has never been so important then today, also on security efforts“
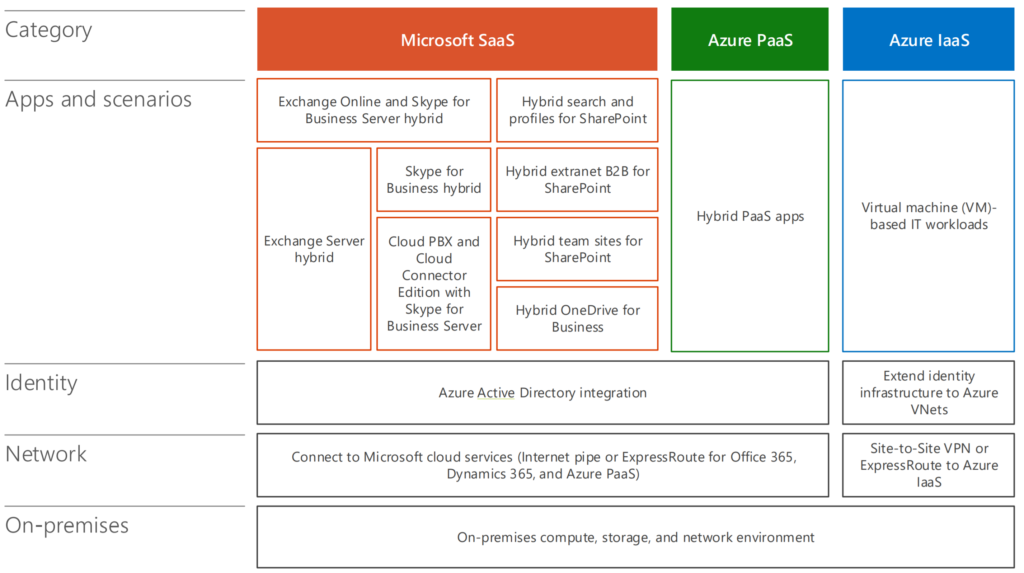
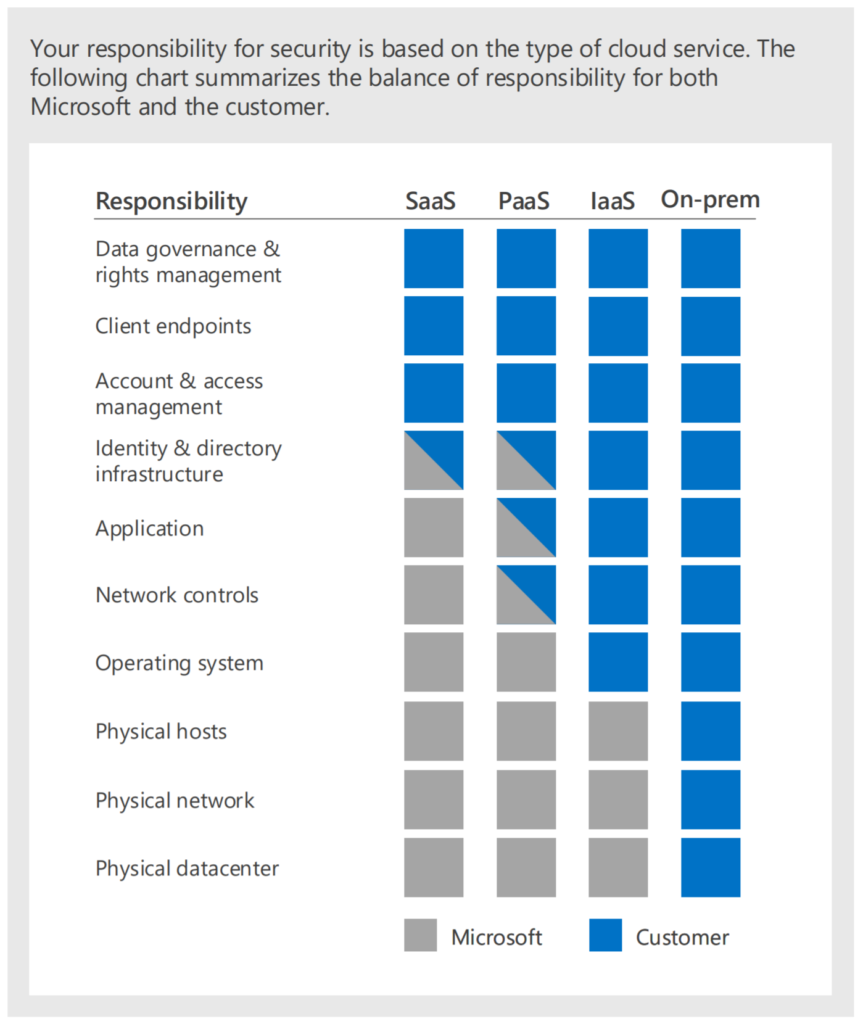
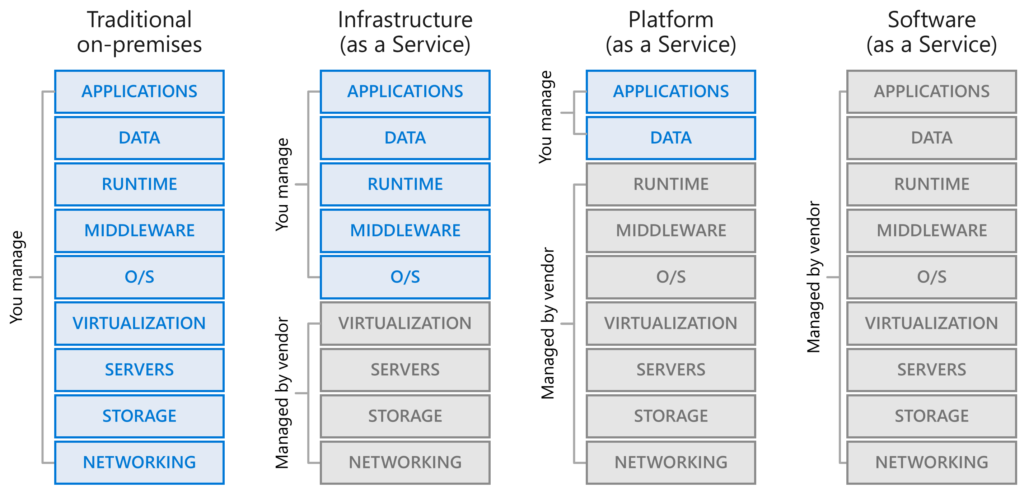
If you, as an organisation work with future proof collaboration tools and migrate your server infrastructure to Azure or AWS or private datacenters the focus stays at protection Microsoft technology. It’s a fact.
How does a security operations work?
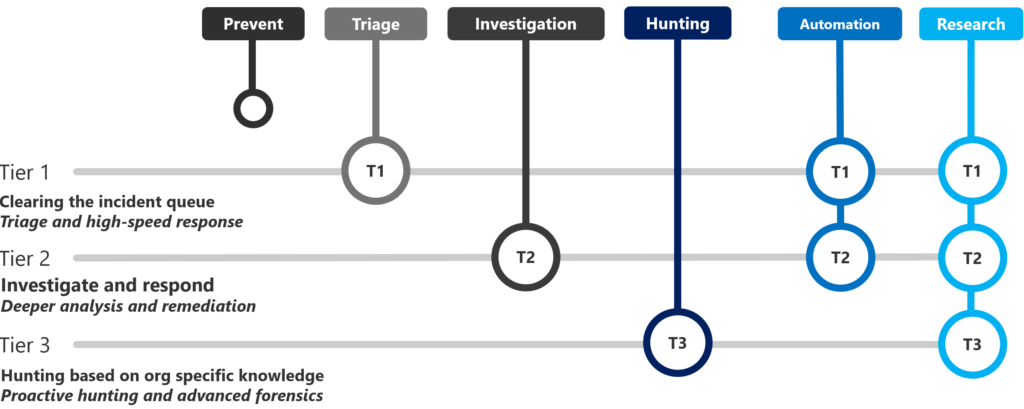
High-level overview of how your security operation is running:
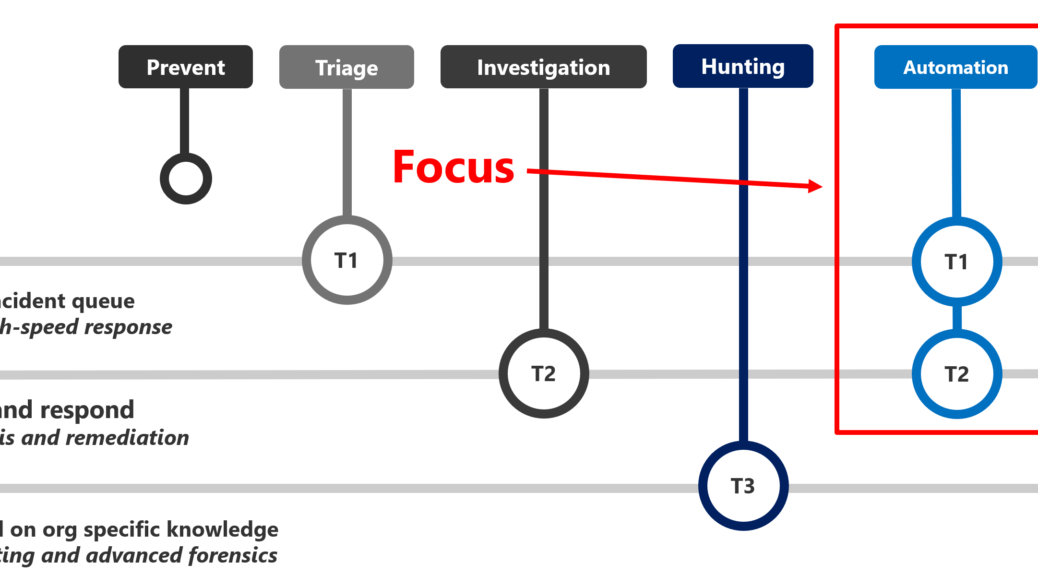
Tier 1: Clearing the incident queue – Triage and high-speed response
Tier 2: Investigate and respond – Deeper analysis and remediation
Tier 3: Hunting based on org specific knowledge – Proactive hunting and advanced forensics
Why choose Microsoft?
Choose Microsoft for simplifying your IT Landscape. It’s already difficult enough. Next to that: Microsoft is leading and heavily investing in Cybersecurity. And buying companies that fit in the future needs.
If you’re building your workplace with 90% Microsoft Technology It’s super strange not to take Microsoft Technology to protect this environment. Think about the foundation infrastructure. Technology and workloads are never the goal of transformation but they are just facts when shifting. Choose wisely if you’re not willing to go the Microsoft way. And if you choose different, integrate with Microsoft.
Why Microsoft? Because it’s leading in the Security era. Let me put this very clear. I do believe there are a lot of security vendors creating great great technology for keeping organizations save. Most of the time the missing part is integration in one ecosystem. That is were the fragmentation and segmentation and integration fails. If it’s not integrated well enough:
- Alerts are coming from everywhere
- The focus is lost
- Security standards are lowered
- The automation is poor
- The security vision is troubled
- The Impact on changes are difficult
Licensing for Security Operation
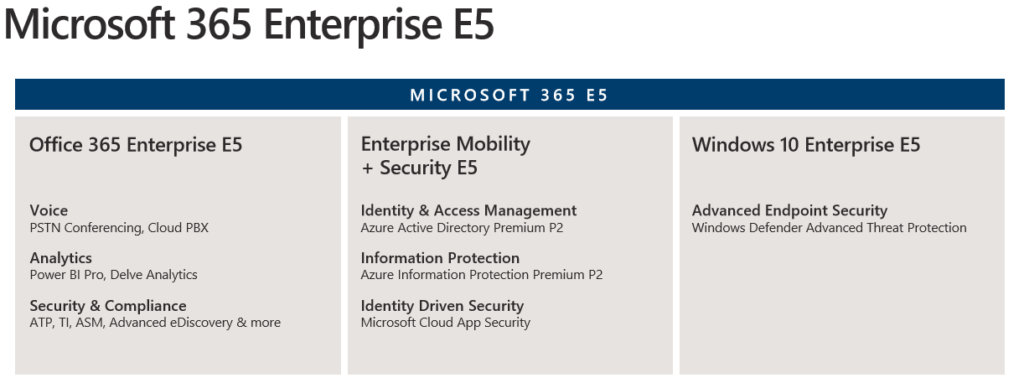
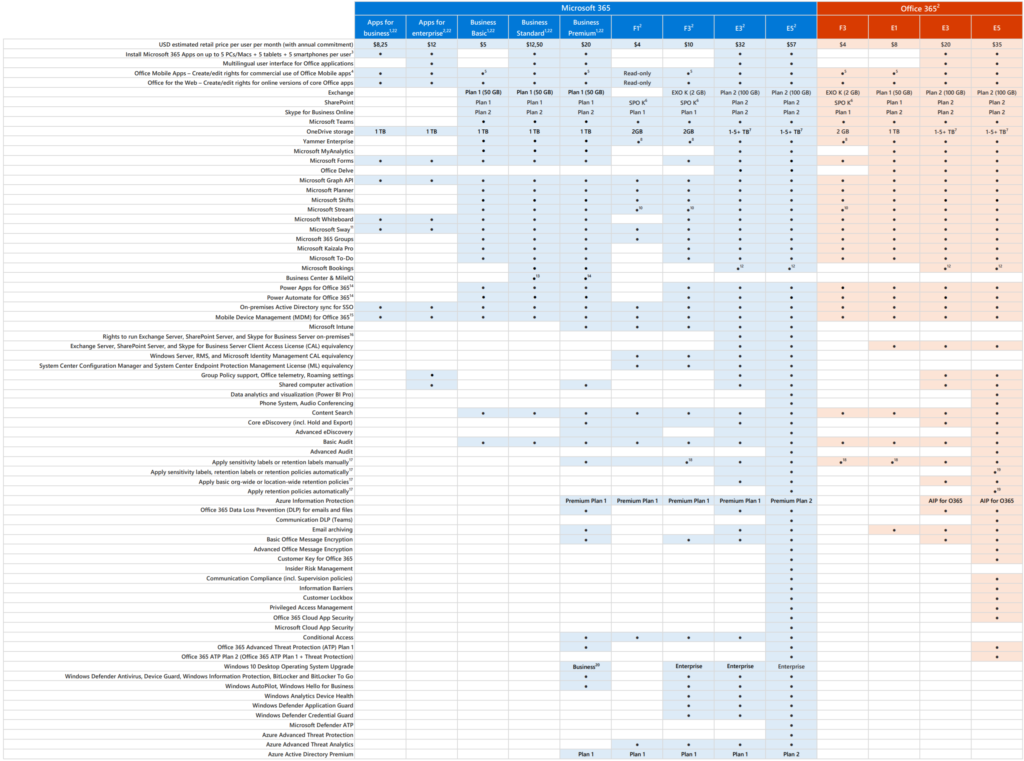
I’ve written a popular article about why should each company invest in Microsoft 365 E3 and E5. As you can see in the licensing part in Microsoft 365 E5 Windows 10 Enterprise E5 + Advanced EndPoint Security is included.

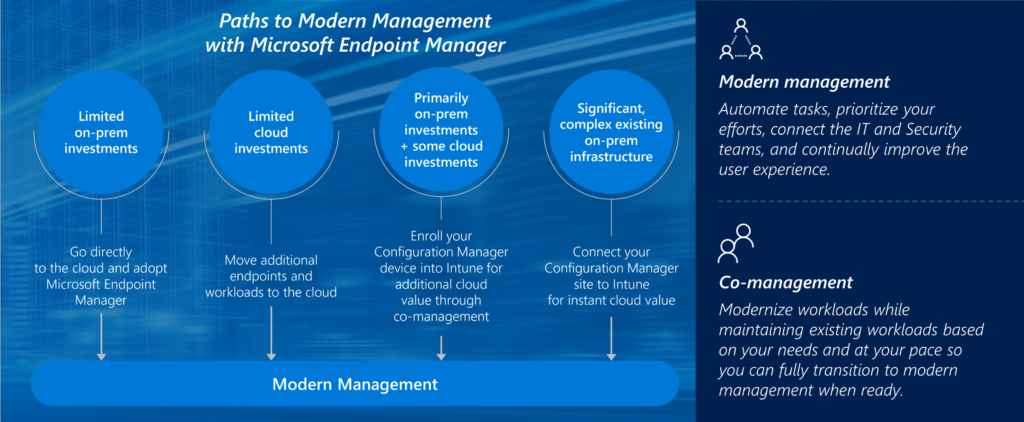
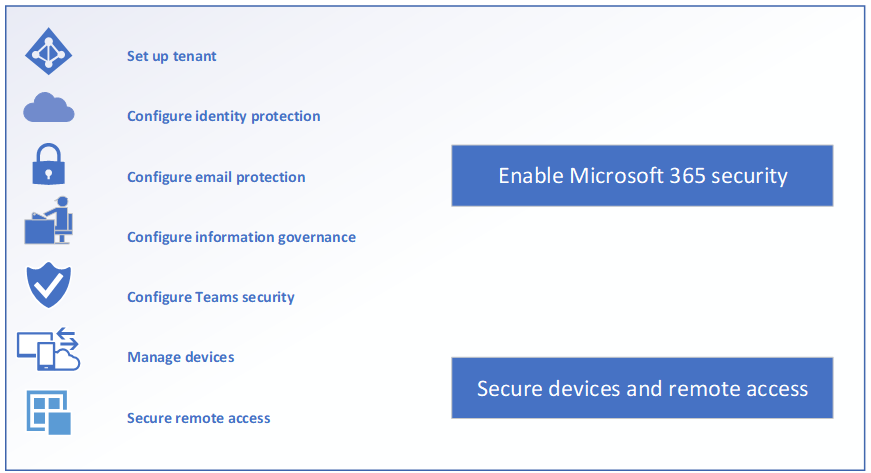
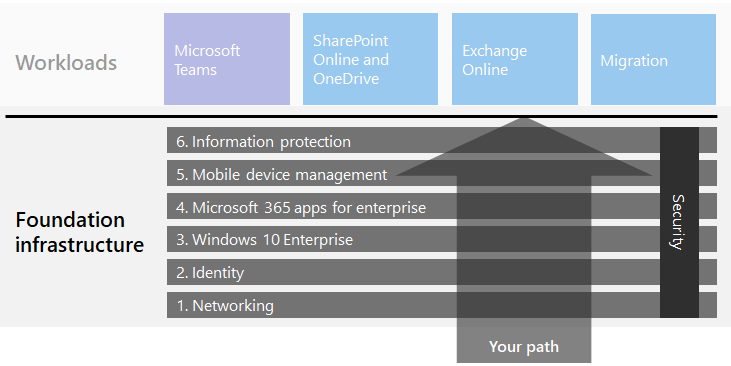
Building blocks of organizations core infrastructure
The fundamental infrastructure – Build your workplace based on a layered approach. The high-level is written below the details in this highlighted article.
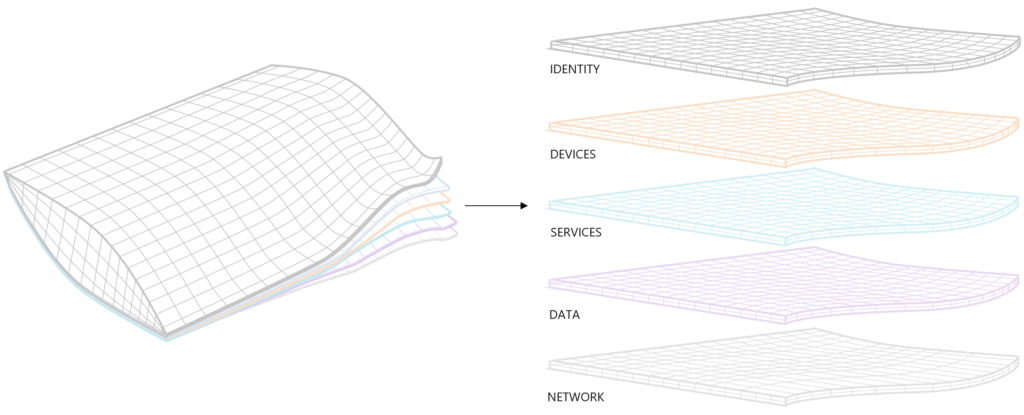
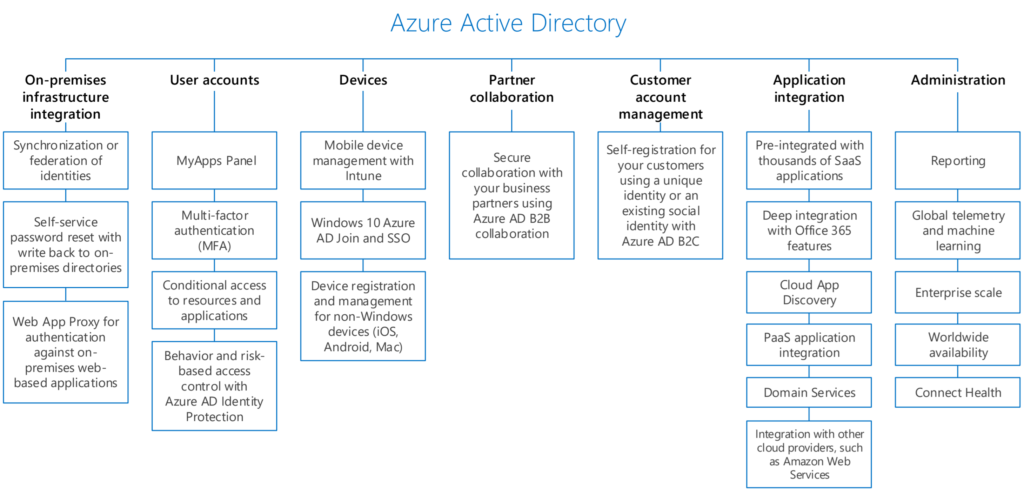
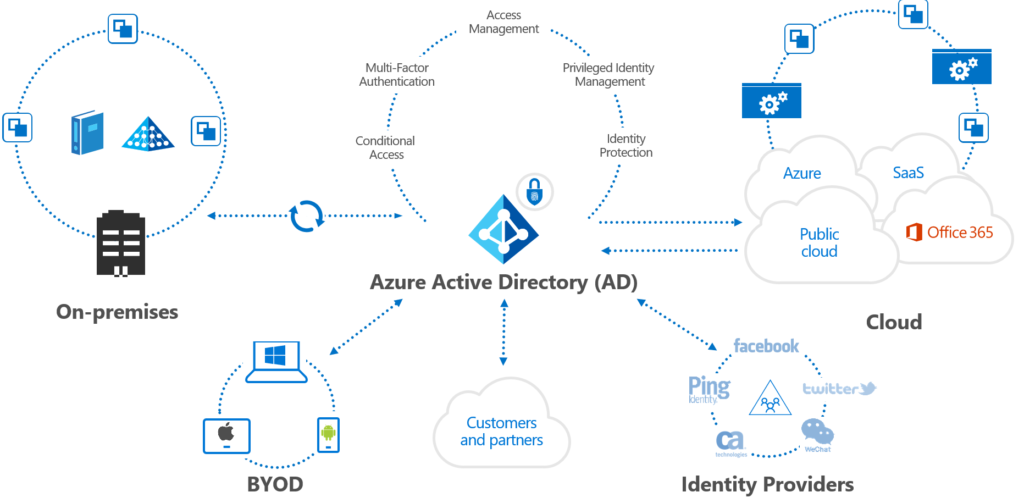
Identity: Building your foundation identity management solution as described in this article. Cloud first. Azure AD primary. More options -> more automation.
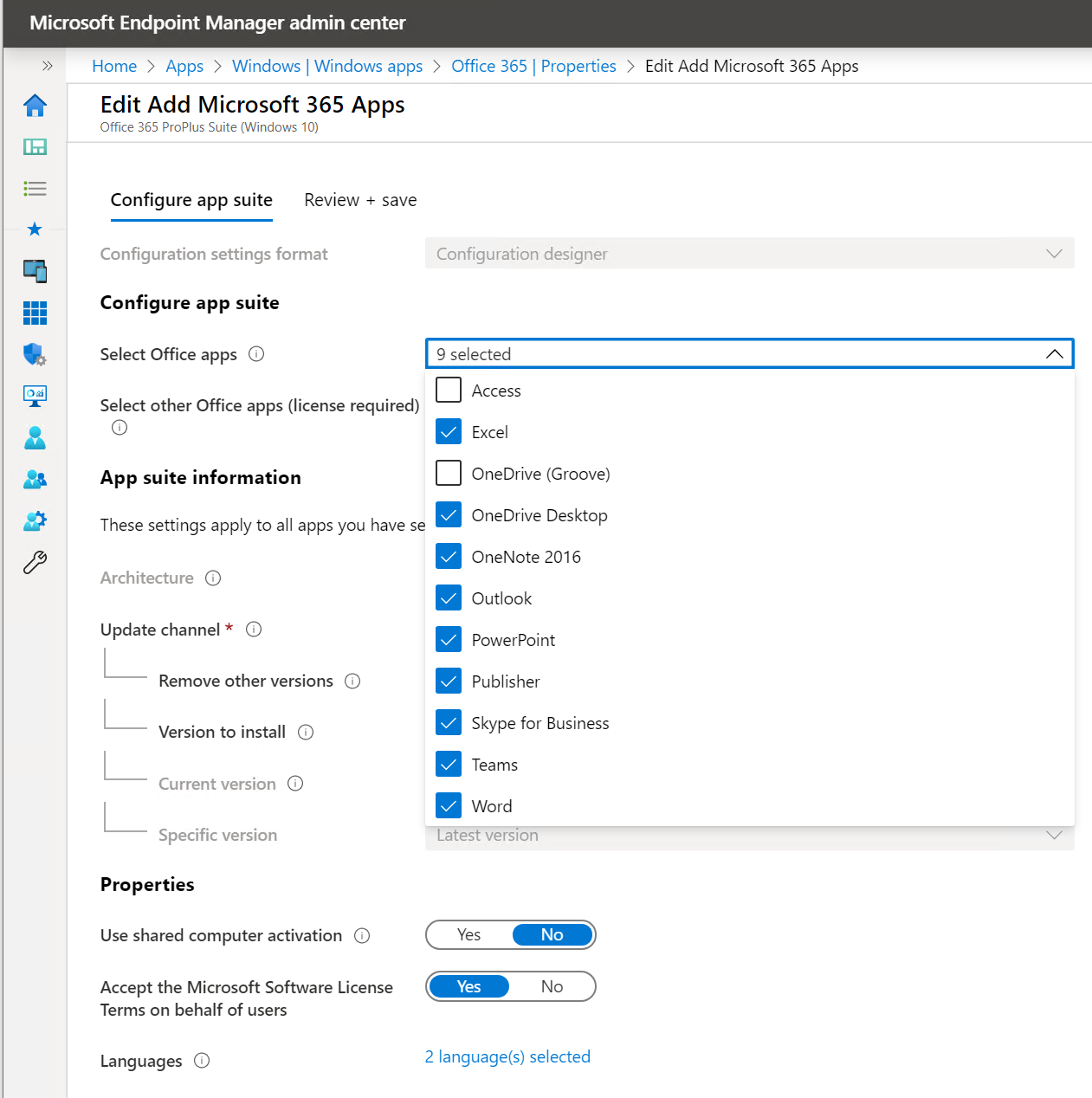
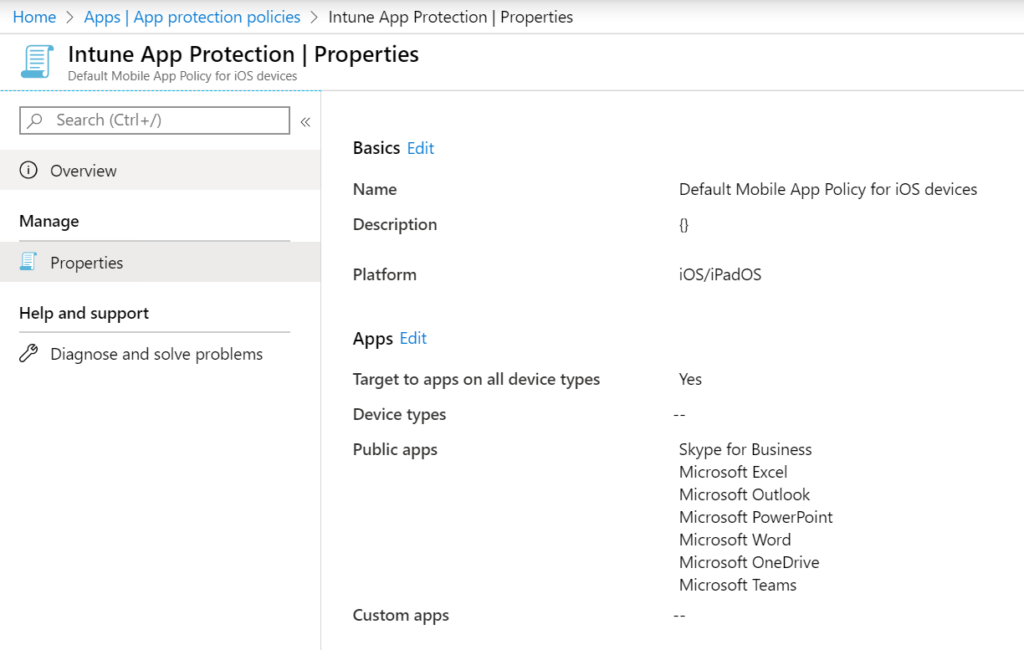
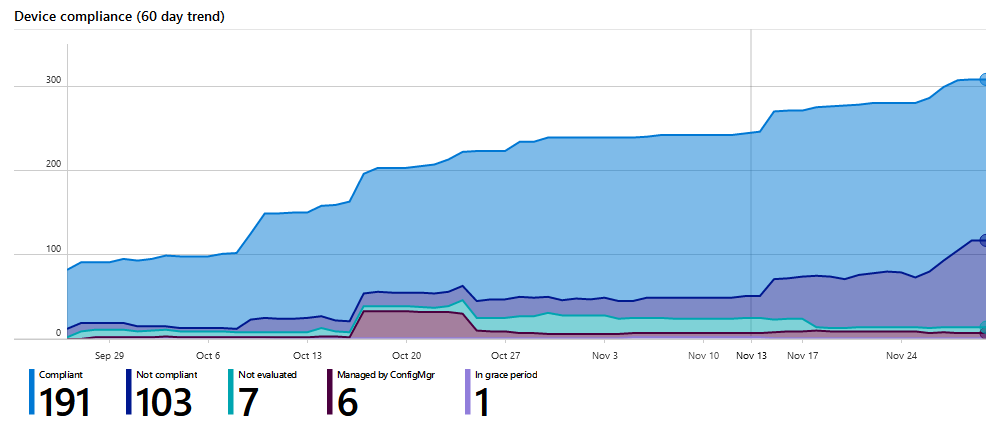
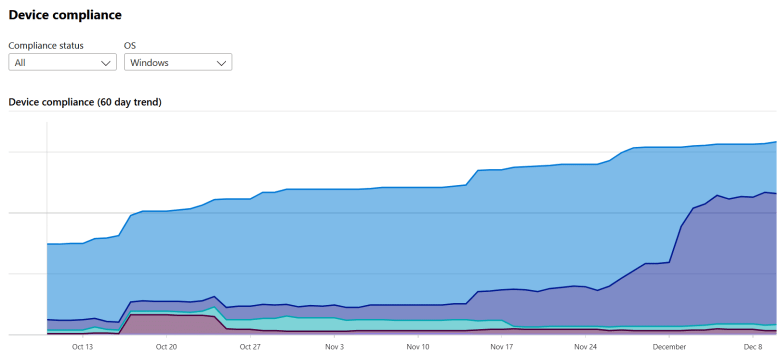
Protect Devices: Windows 10, Mobiles, iOS, Android. Exclude non supported devices so it’s super clear what is supported. On paper + technical. Compliance.
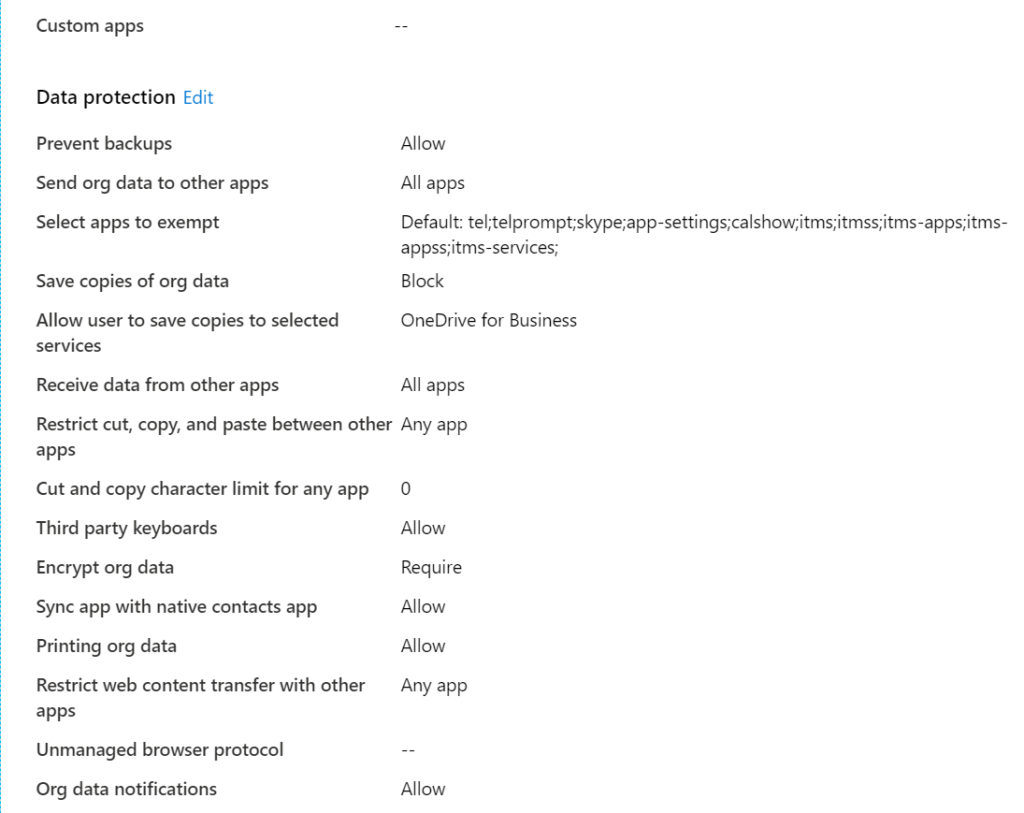
Services: Understand the services used by your business or customer. 5% of all companies do know what software they are using and running. Ask the DPO to deliver a list of current used applications and services..
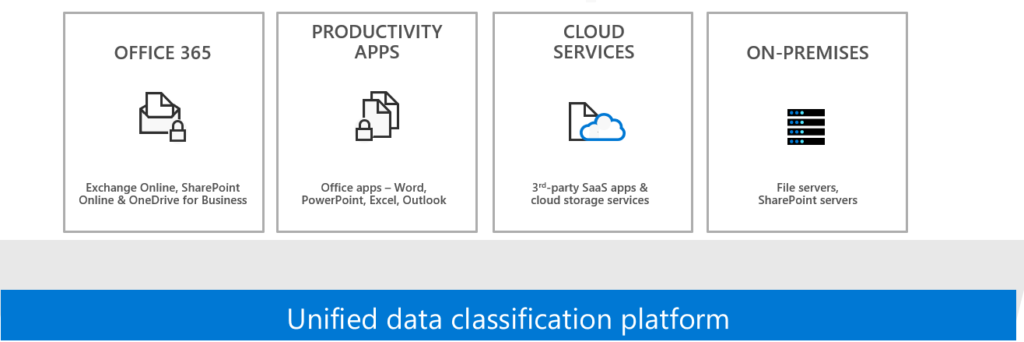
Data: Data can be in Microsoft 365. Third-party can be strategic defined that it lands in SharePoint, Teams or OneDrive. Most of the time that’s your 90%.
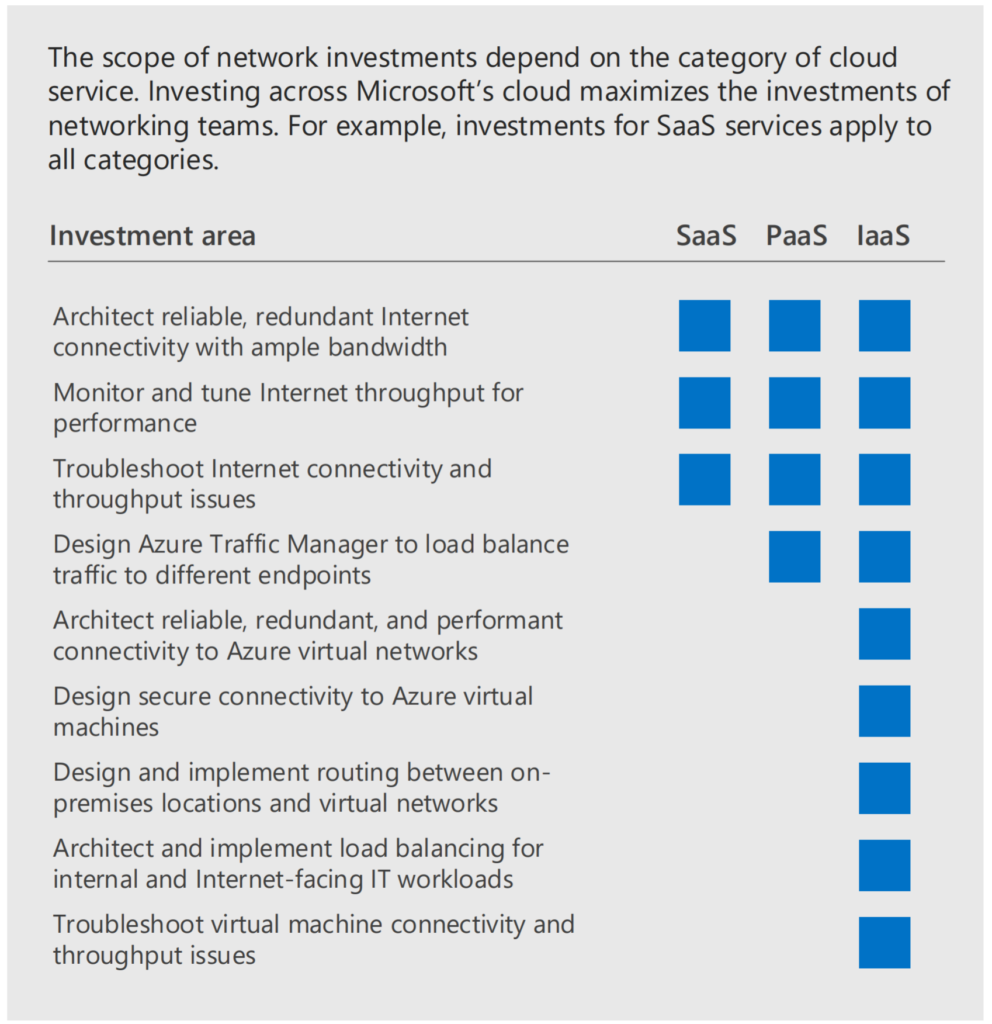
Network: Just treat it as an public connection. Depending on the migration path to M365 and Azure. When all infrastructure is still running on-premises. It could be that it’s not (yet) possible.
There are always exceptions needed for some applications – but this doesn’t mean you cannot do the 90% right!
Why you (don’t) need a 24×7 team
Focus on the prevention of important fundamental things as for example: Identity & Devices. Automate all actions in Tier 1 + Tier 2 even if you don’t to research and analyses right away. Because you don’t have people working in the night. Make smart decisions. Isolate risks as compromised identities, devices etc.. Automate.
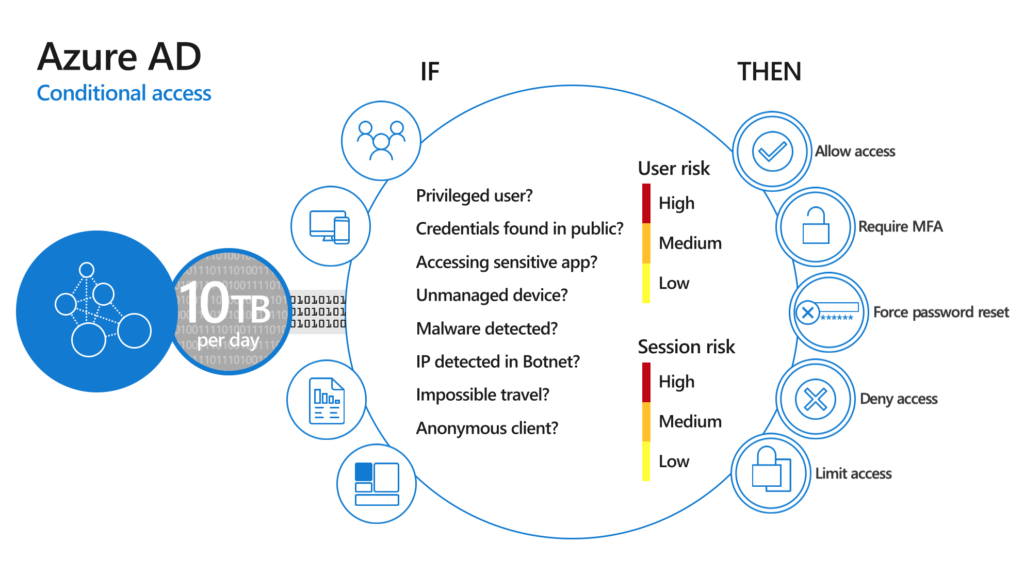
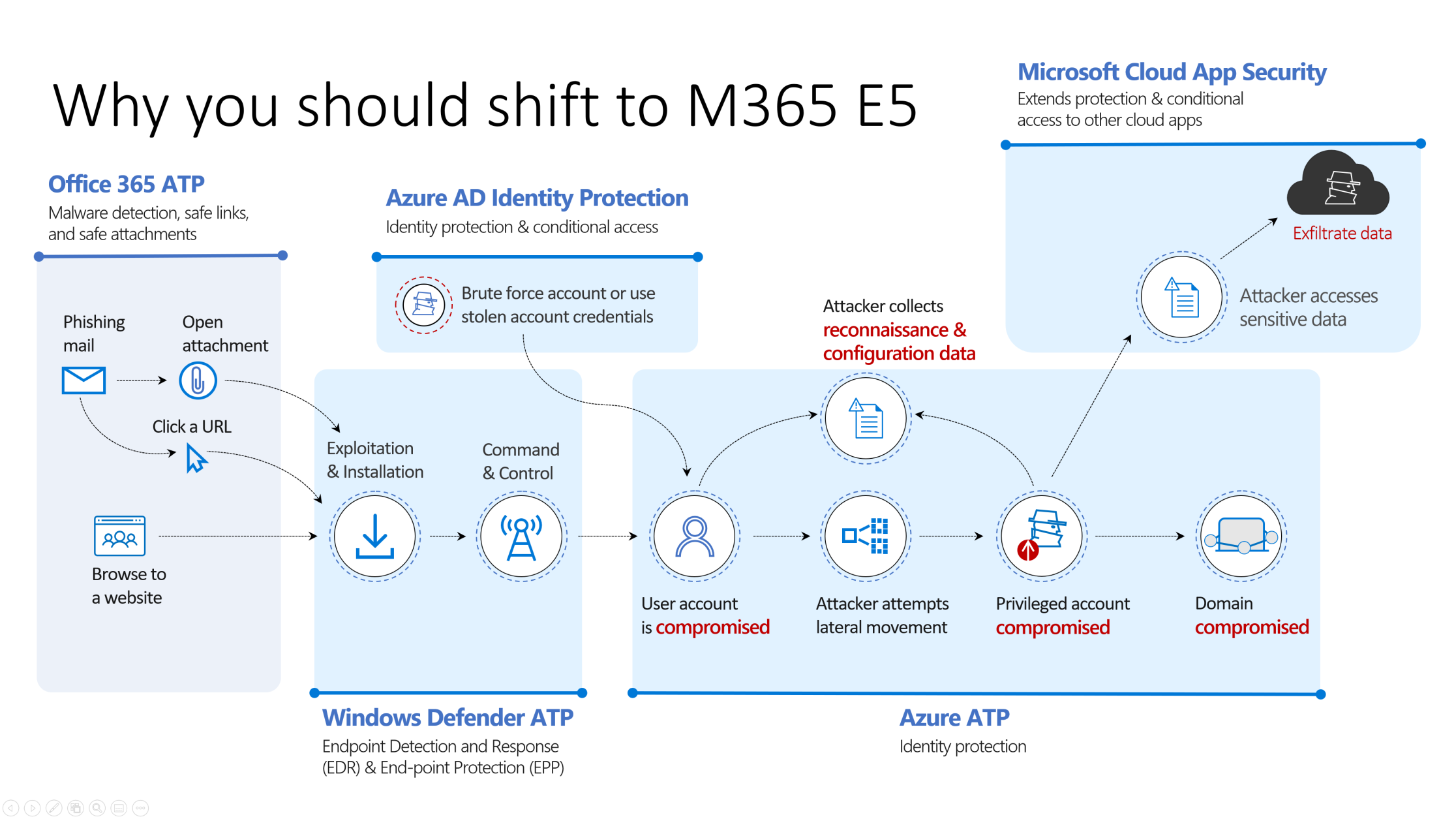
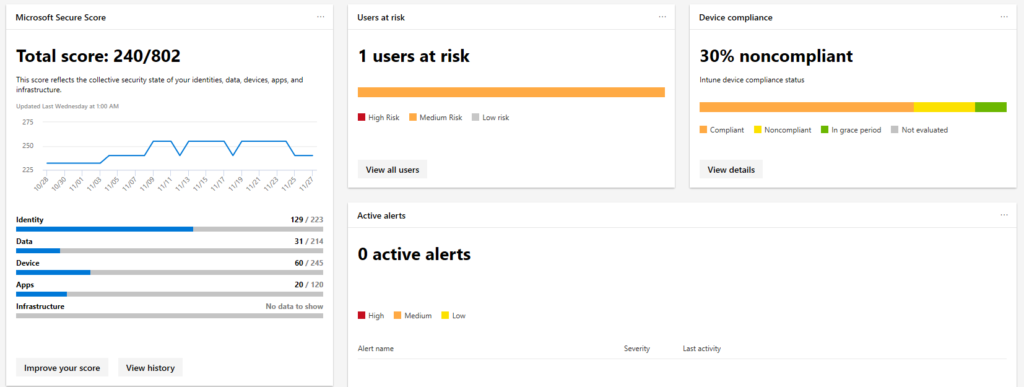
This is the most important figure of the whole article.
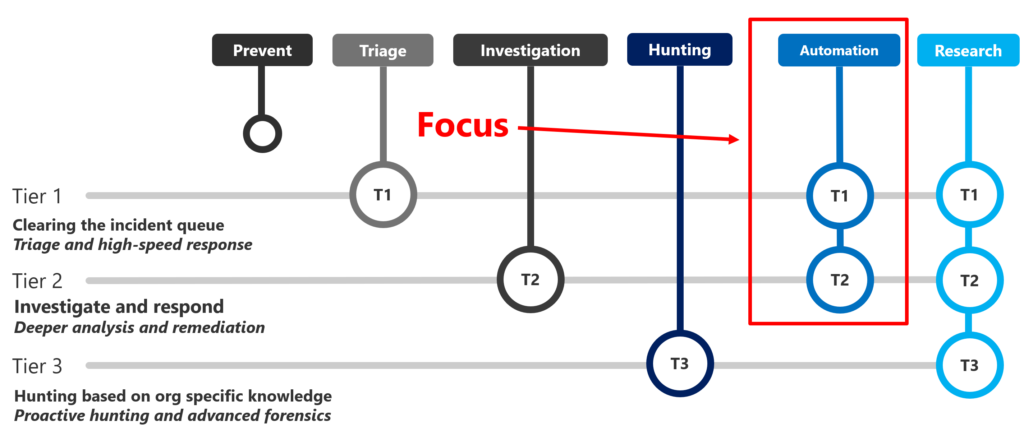
Practical examples of T1 and T2 response and remediate
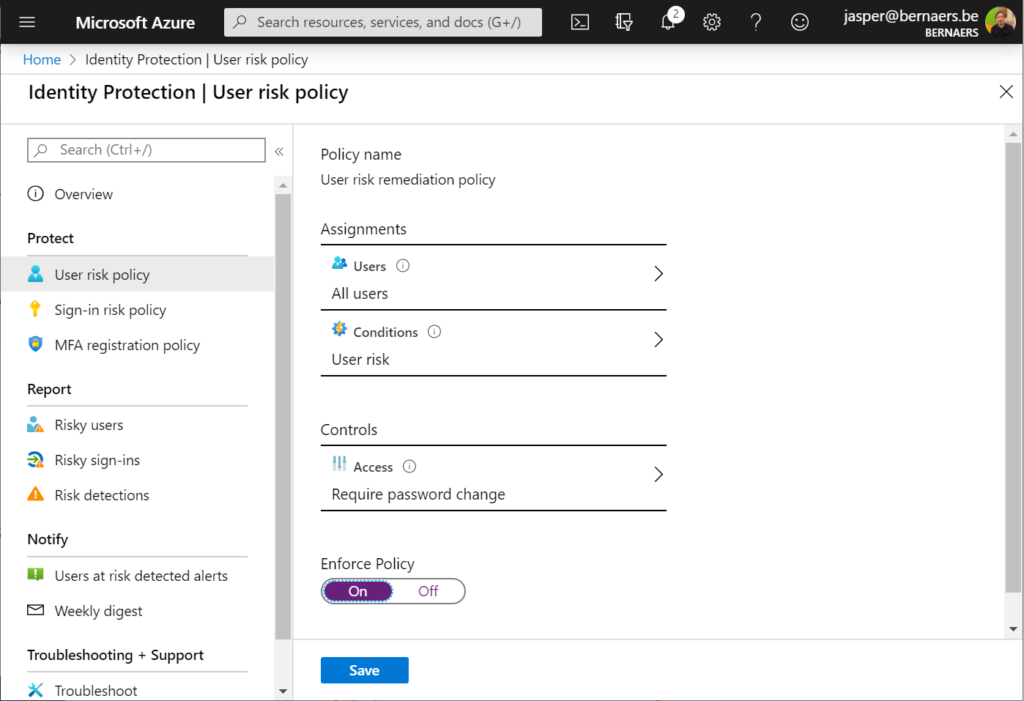
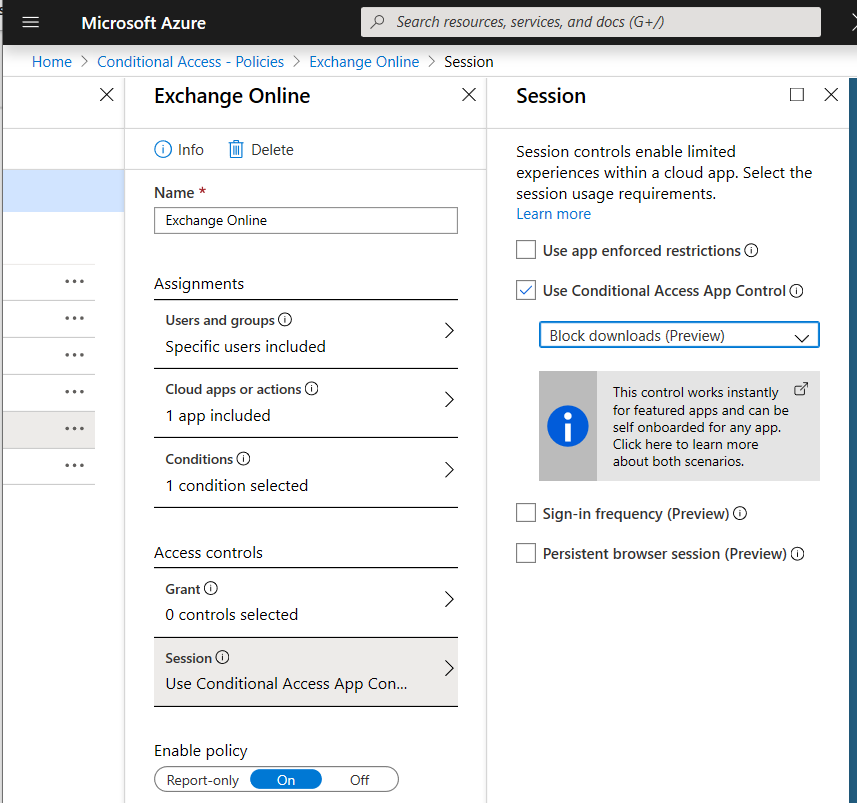
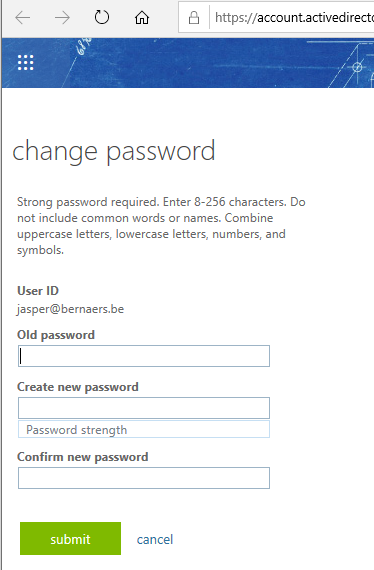
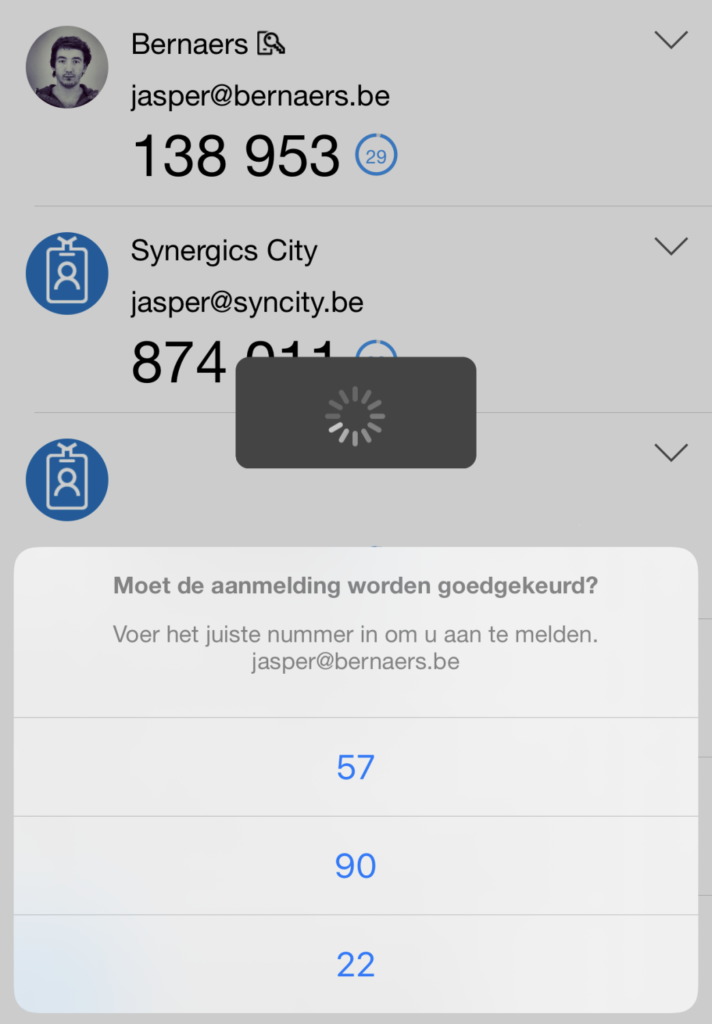
Example 1: Identity protection: Require Password Change when the risk is high. Create process that describes the action required as: Call user – validate risk – validate credentials (real person) ..
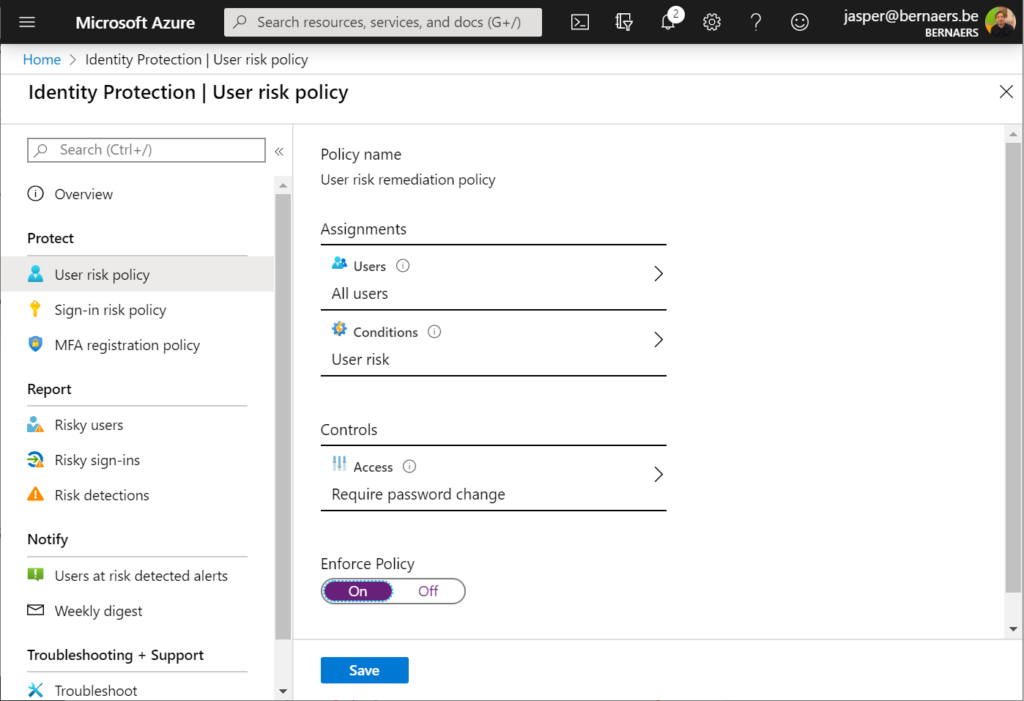
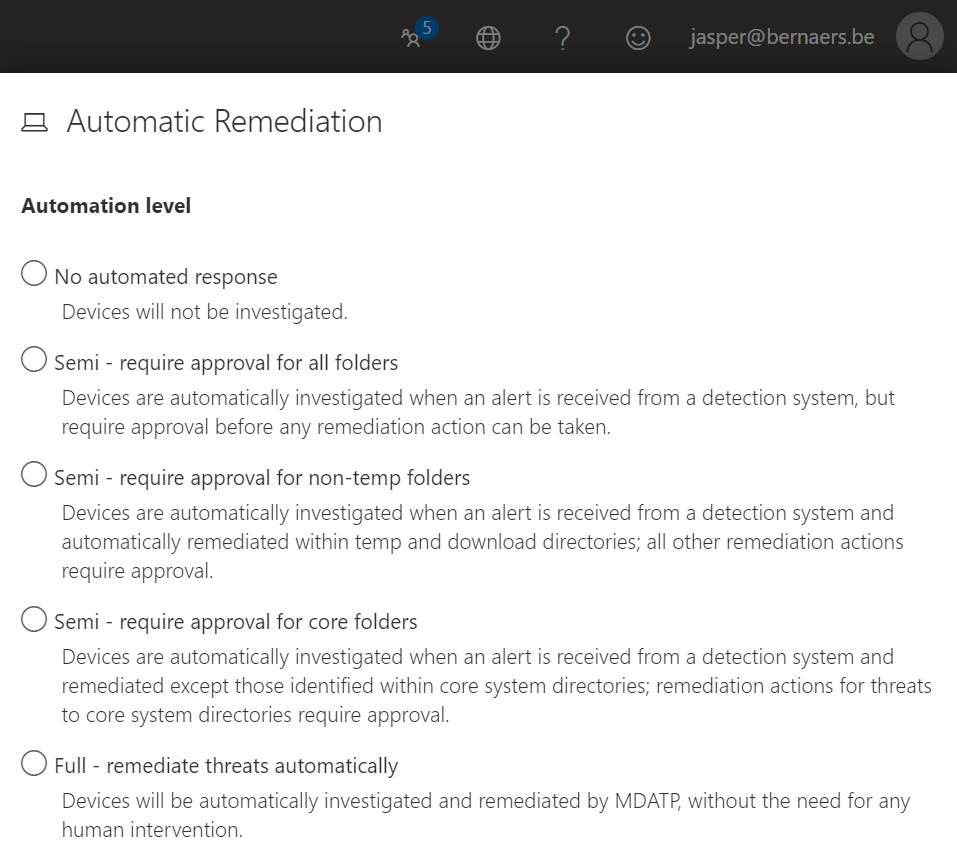
Example 2: Automatic Remediation when suspicious events are happening.
If you don’t want to do anything set remediation to automatically and build a partnership with Microsoft Engineers to consult when threats are around the corner. This is a holistic position. You need Security specialists to start from scratch.
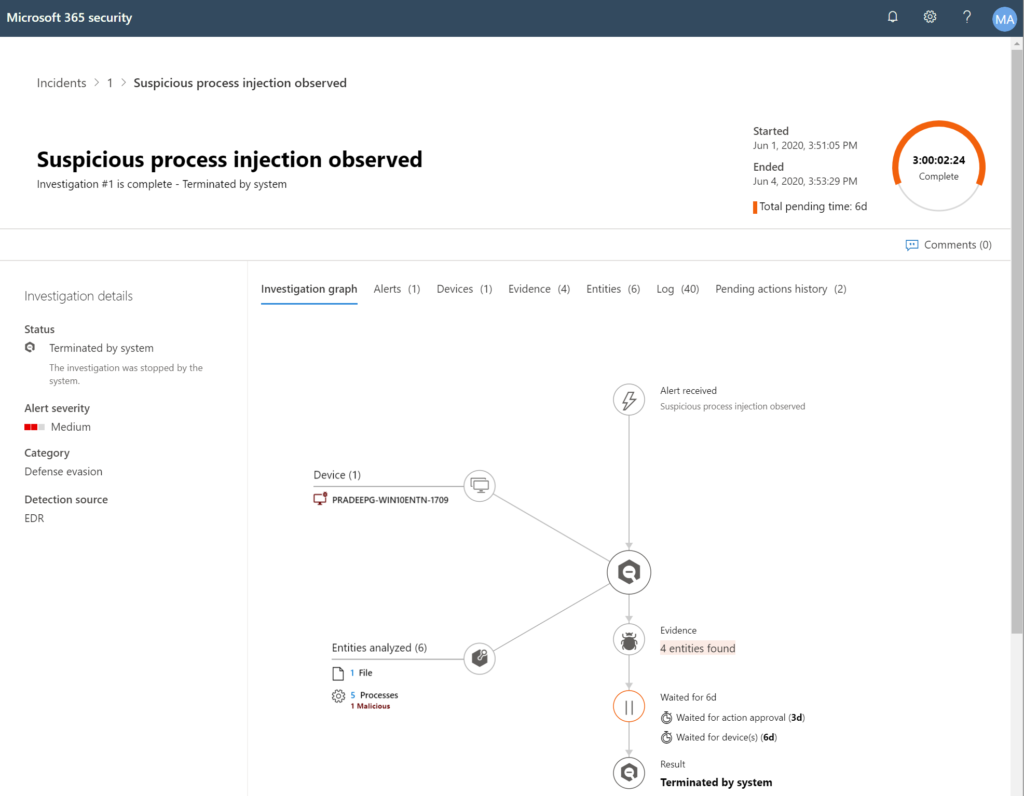
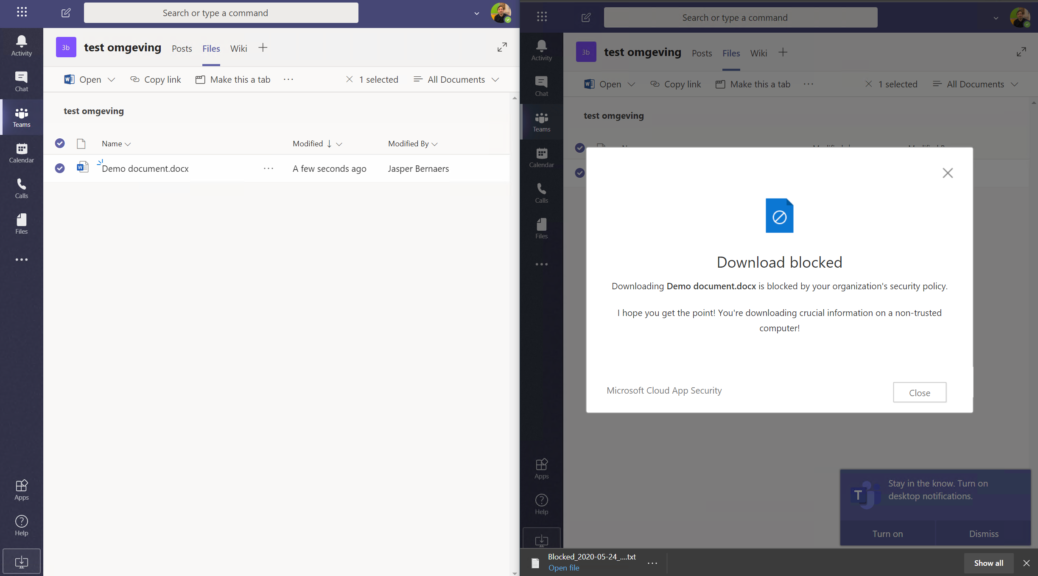
Example 3: Isolate a machine when risk is detected. You can use Microsoft PowerAutomate to do automated response when events appear. The possibilities built-in without any code and development are huge. The impact and value is undervalued 🙂
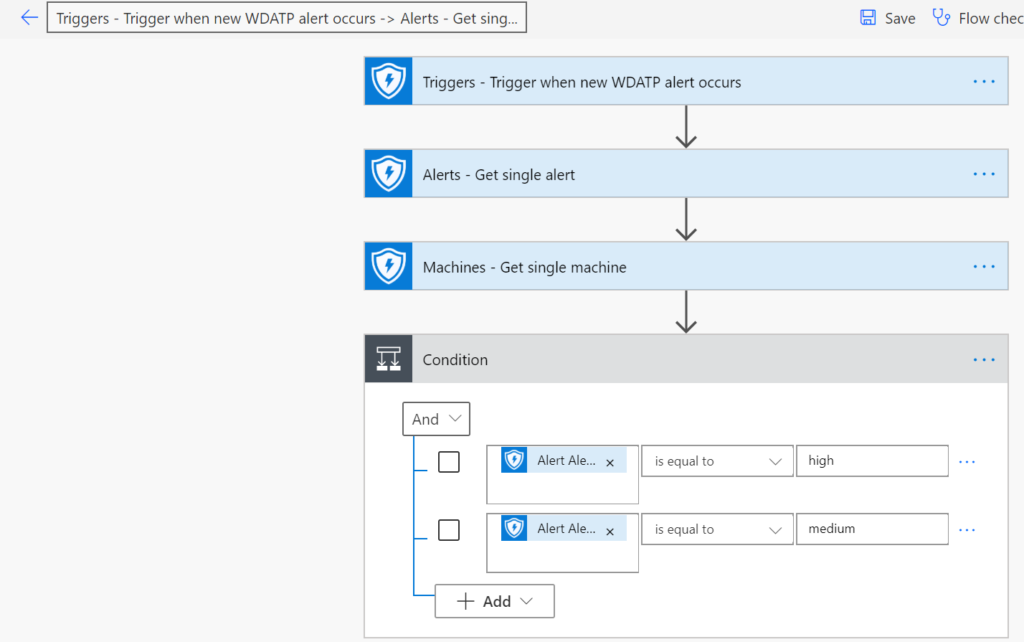
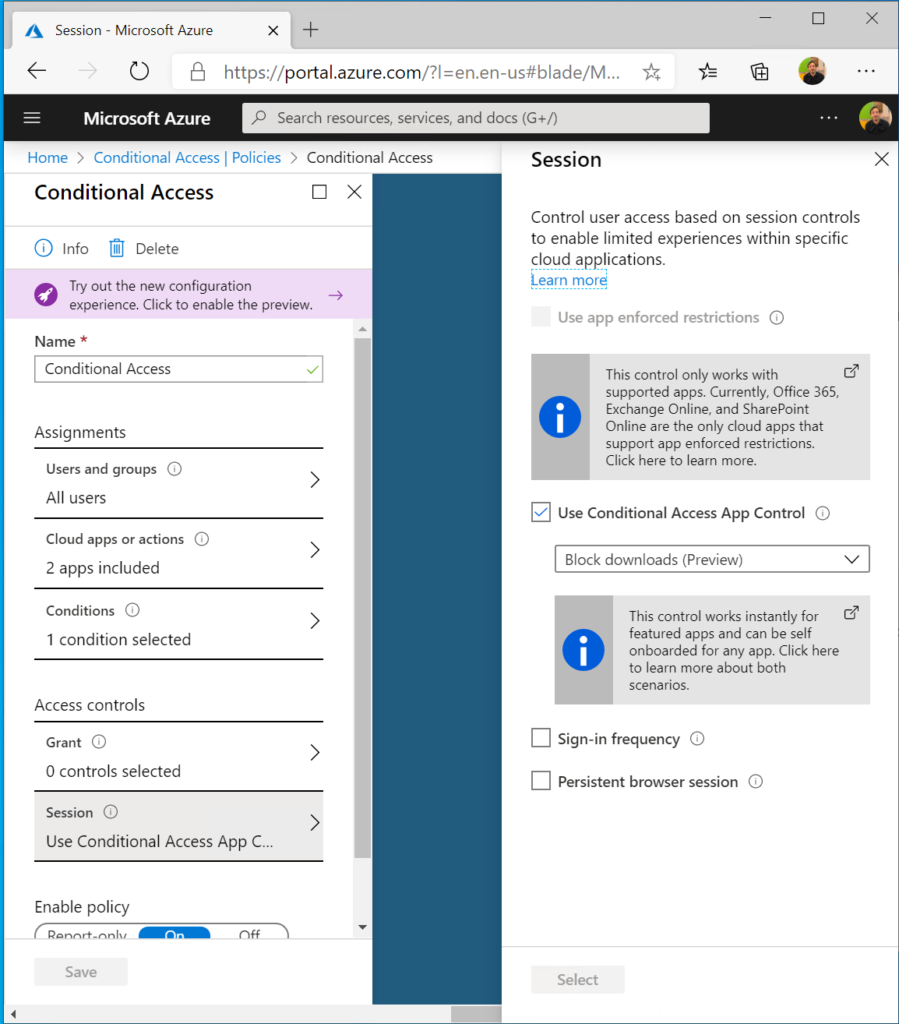
Identify(1) and Protect(2)
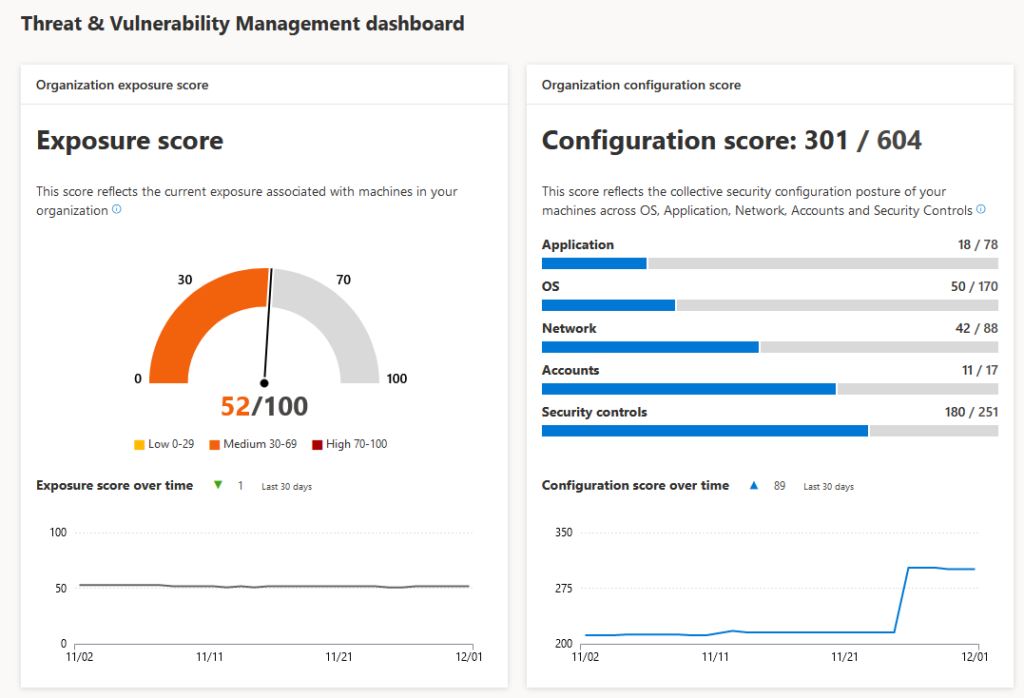
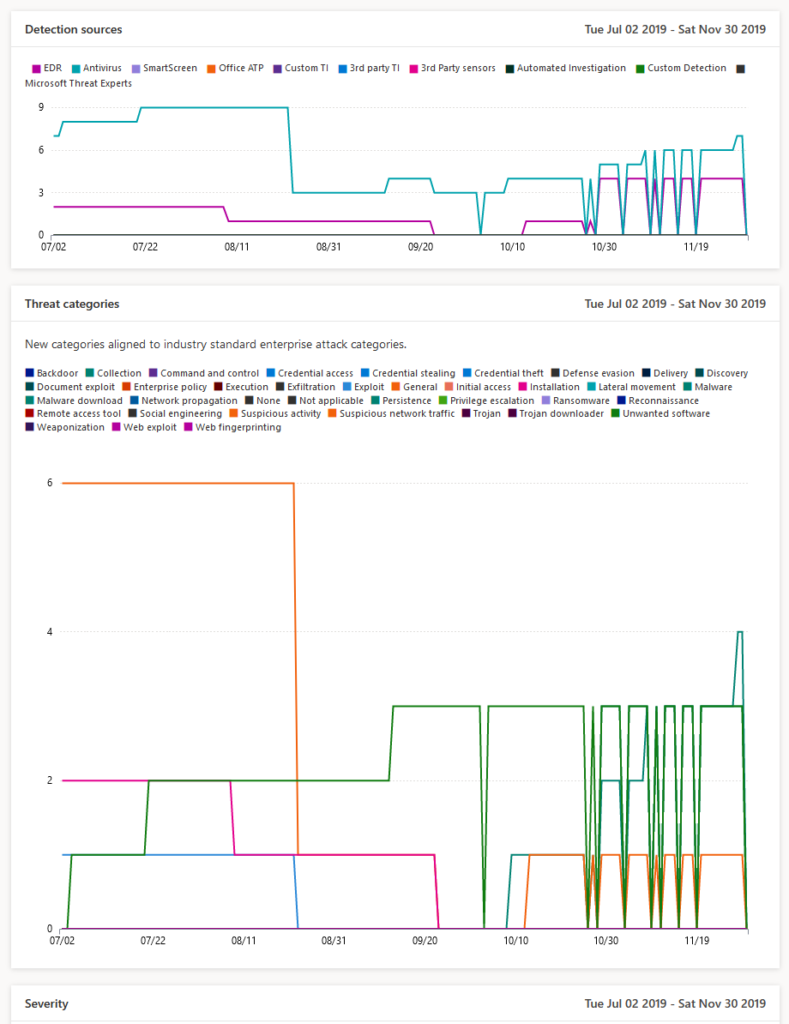
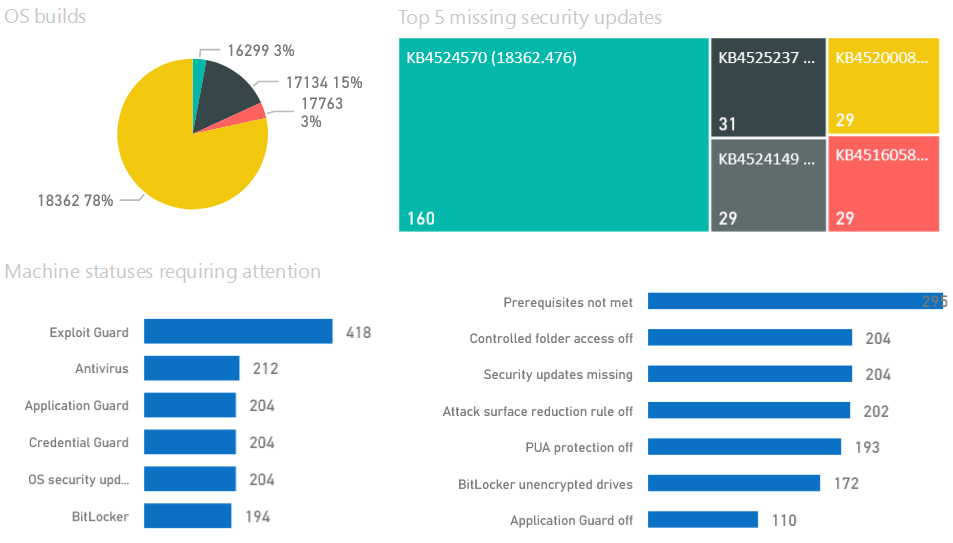
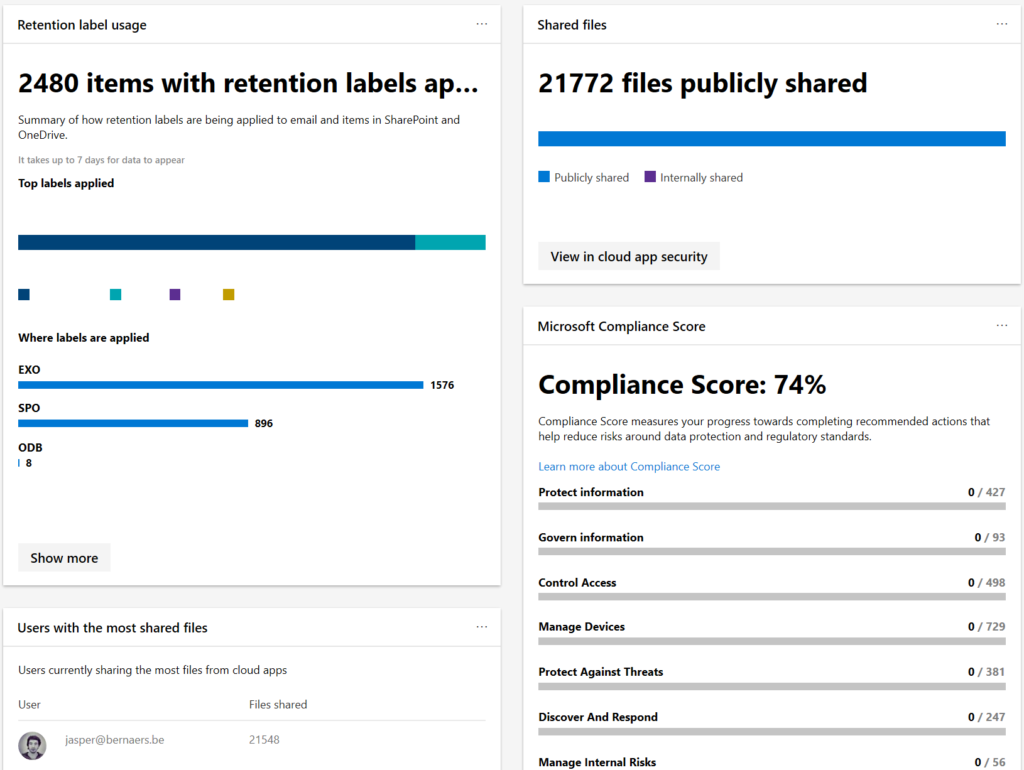
What you could do to Identify and protect your organization is work with the: Threat & Vulnerability Management dashboard to map actions on your roadmap to implement. 5 top Security recommendations are brought by Microsoft, as example.
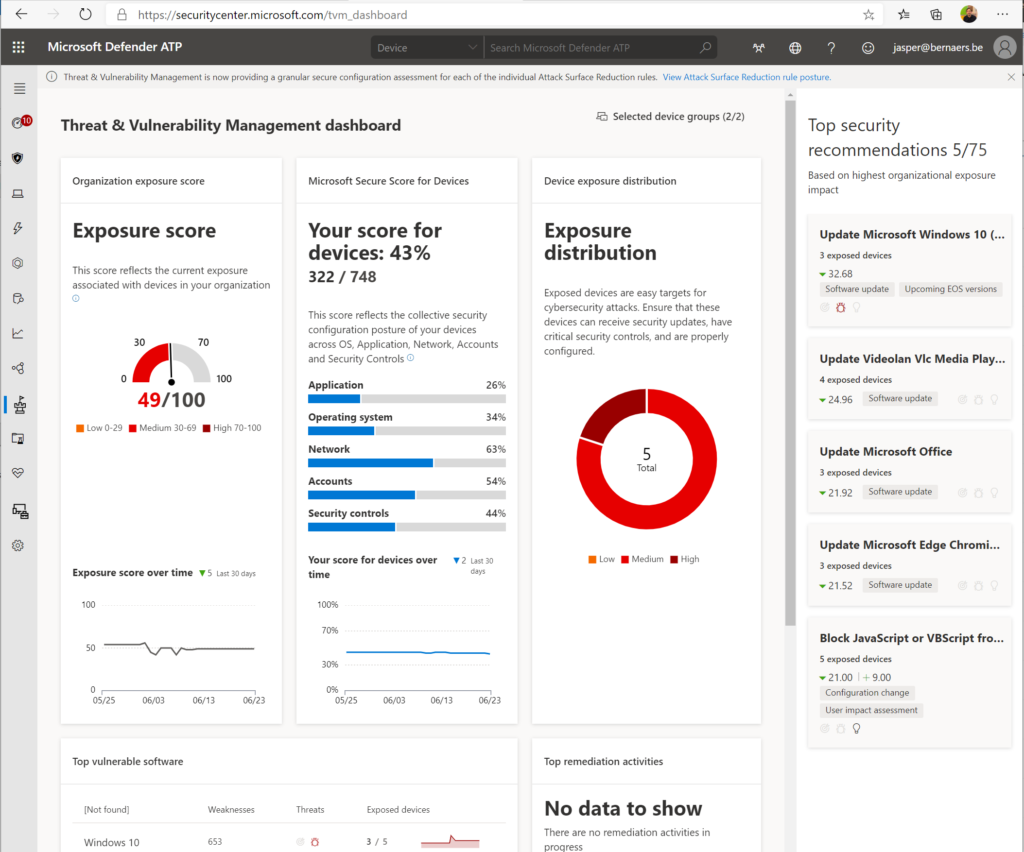
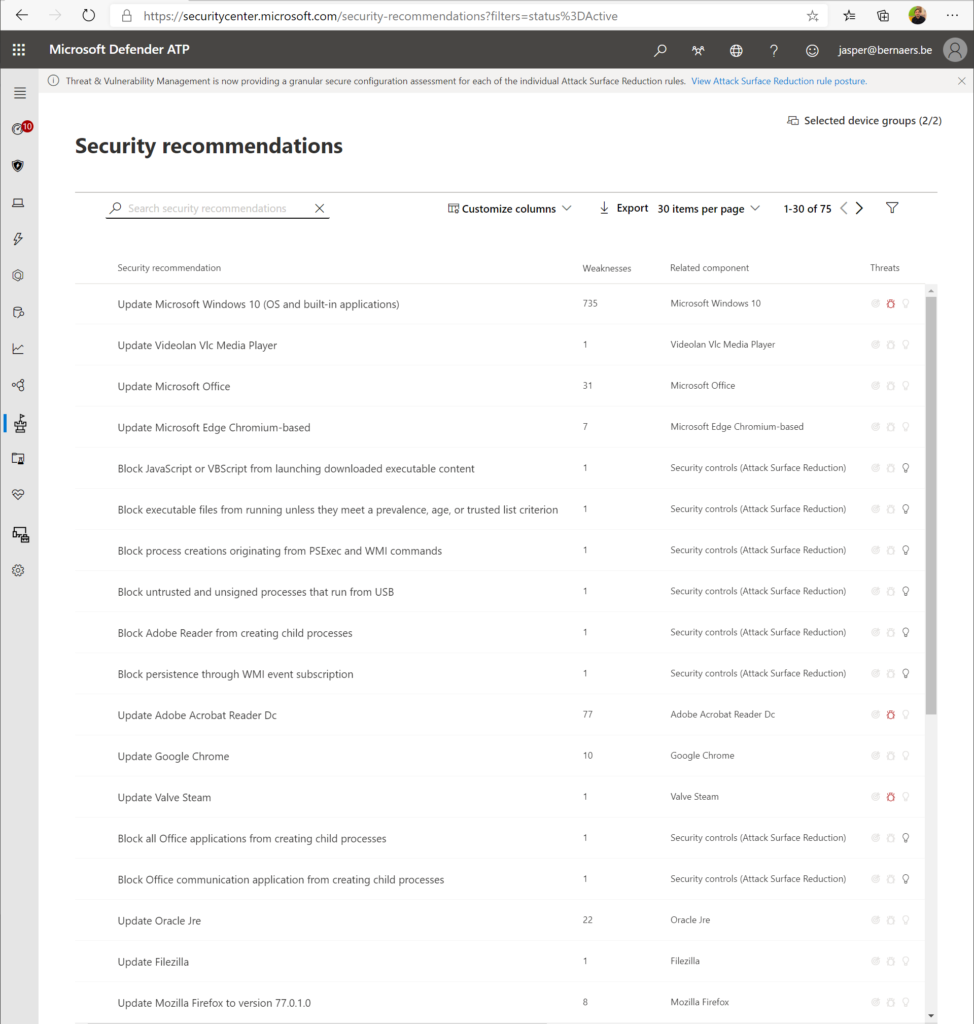
Security Recommendations: Find the critical gaps. Put them towards the operational team. Process needs to be defined.
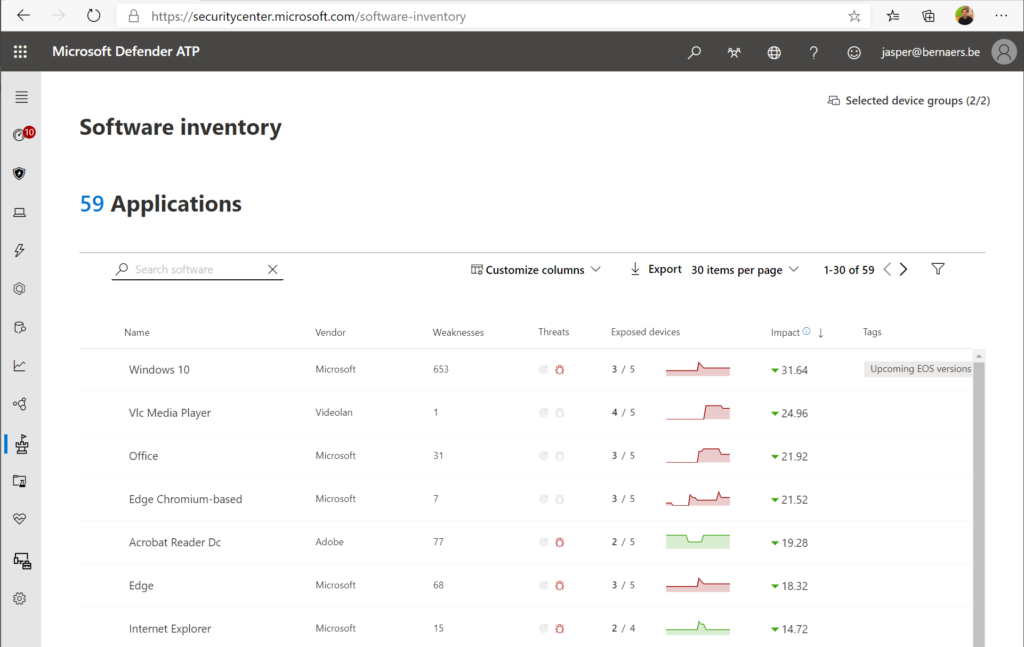
Software inventory: Easiness of understanding the temperature and the required actions to make these risks go away. Again process..
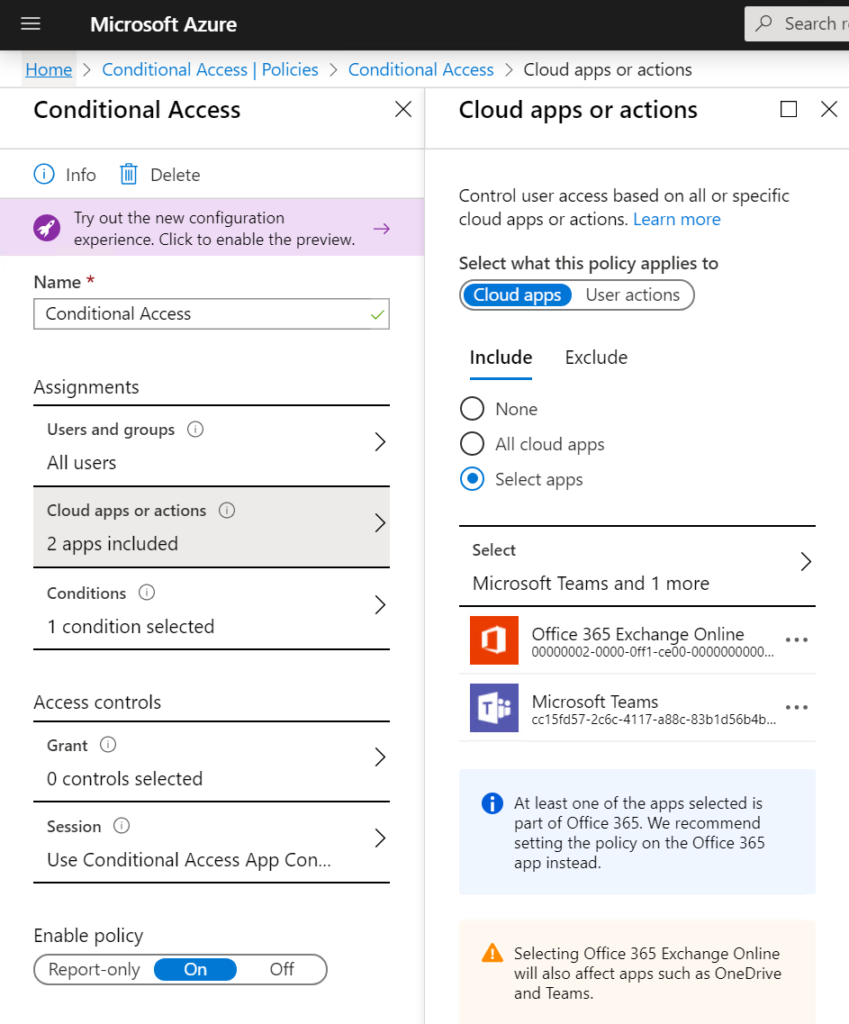
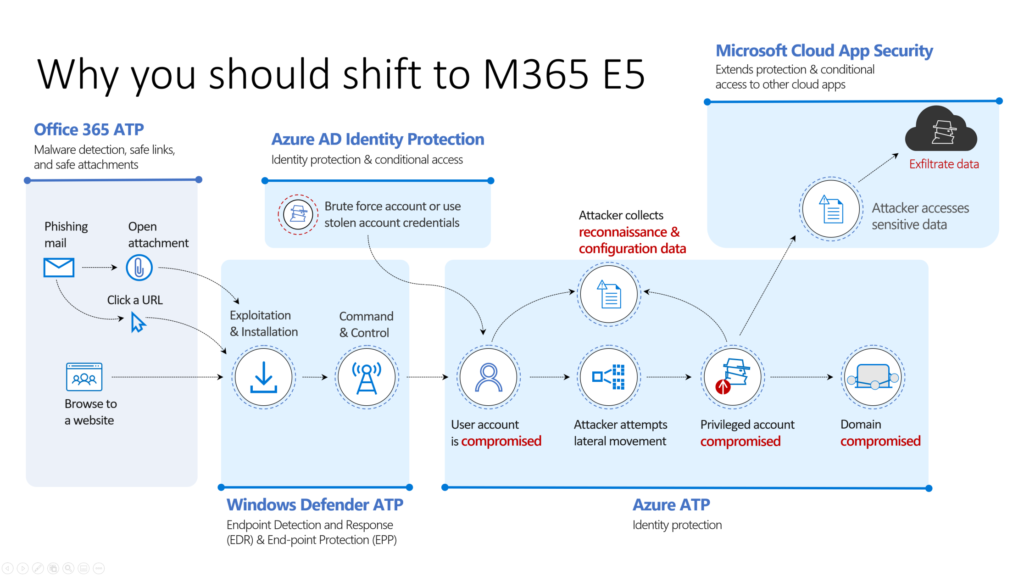
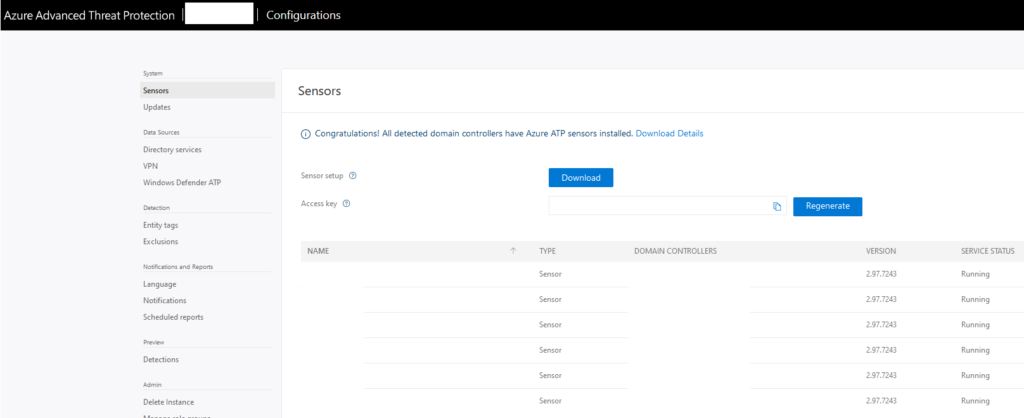
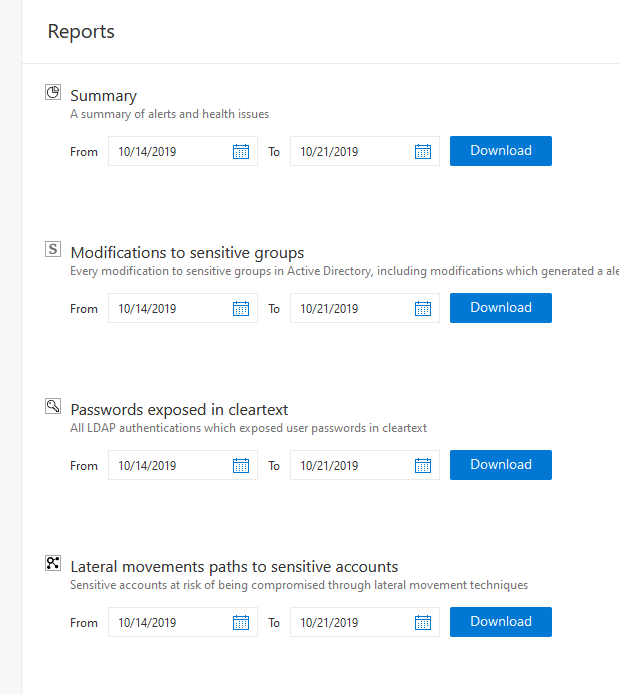
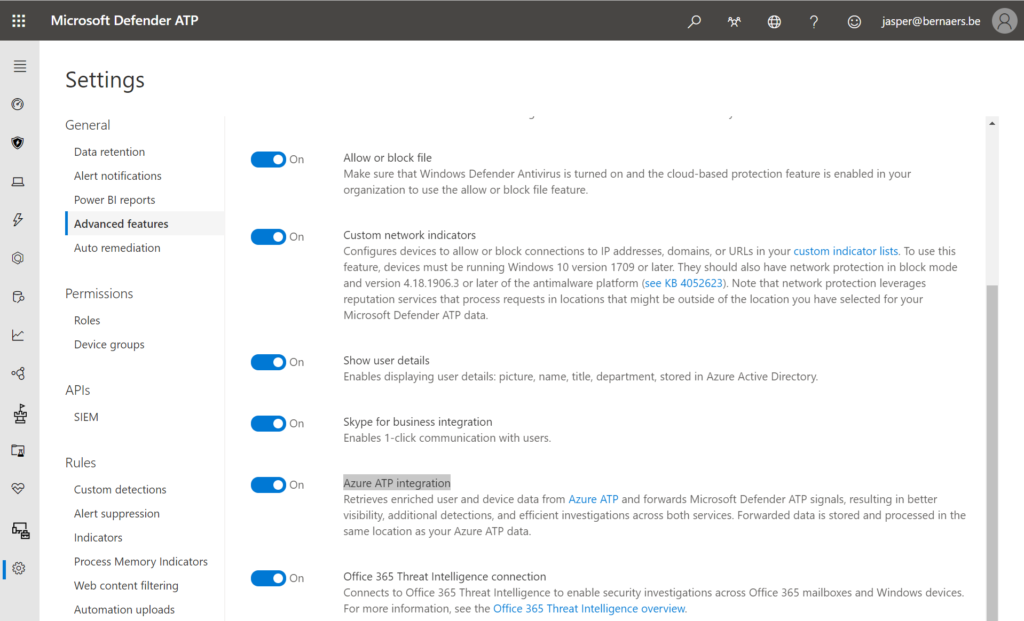
Integrate ATP for on-premises alerts from lateral movements, plain text passwords, pass-the-ticket/hash to understand which alerts occur.
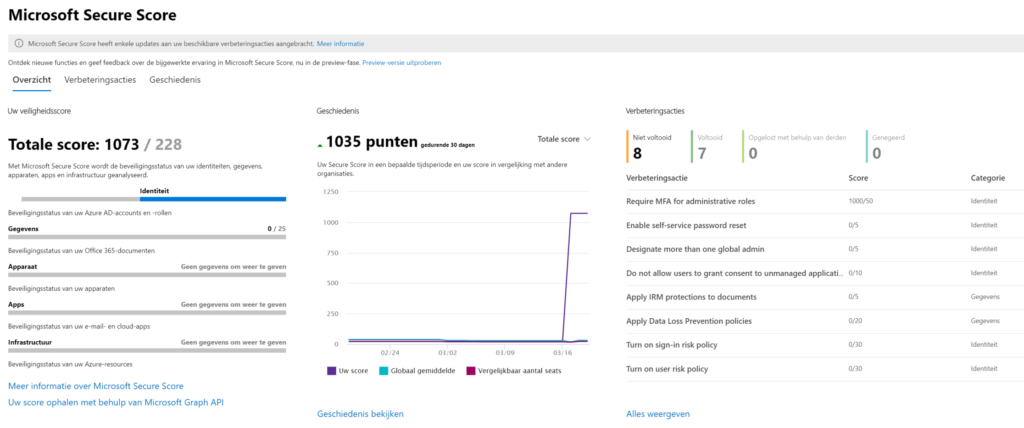
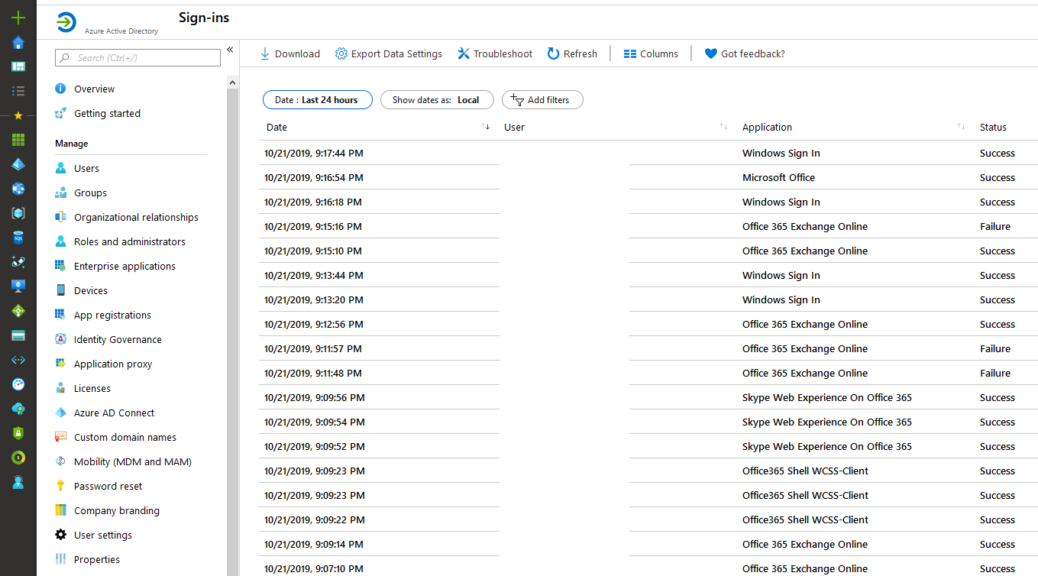
Detect (3)
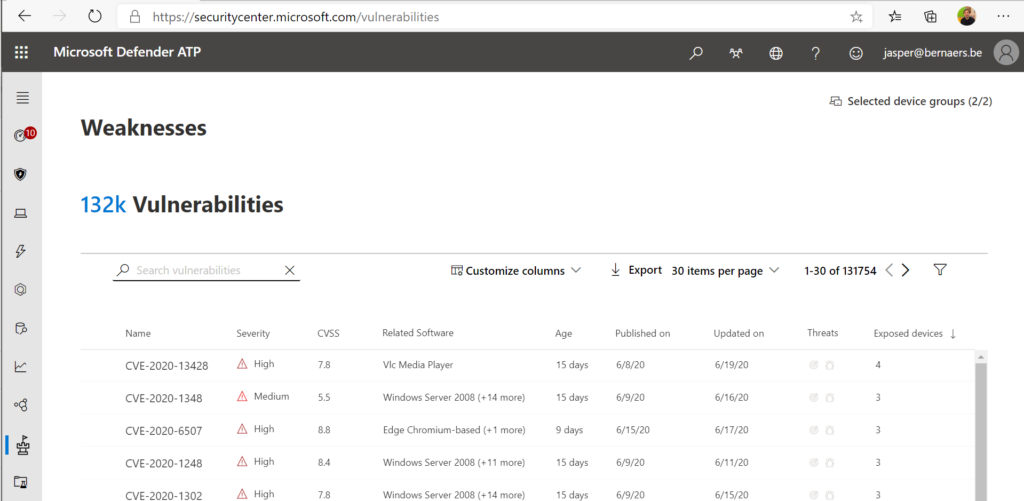
Weaknesses in SecurityCenter: Easy to bring these in the first process and create processes with service levels to fix these gaps.
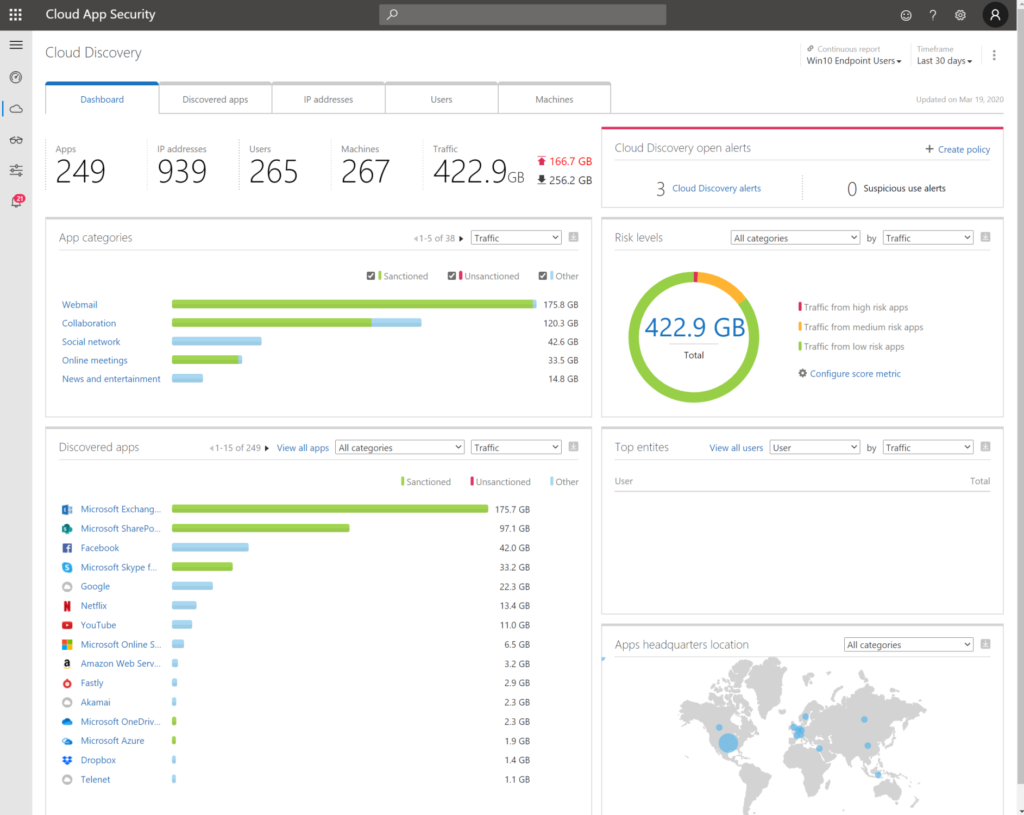
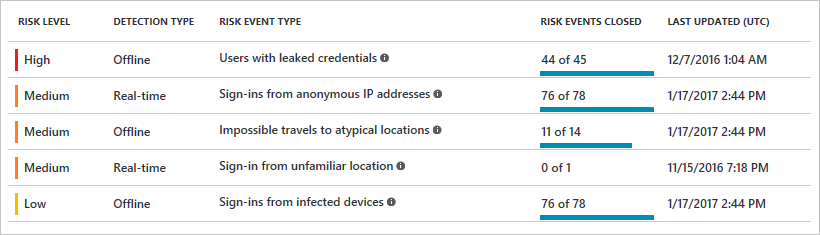
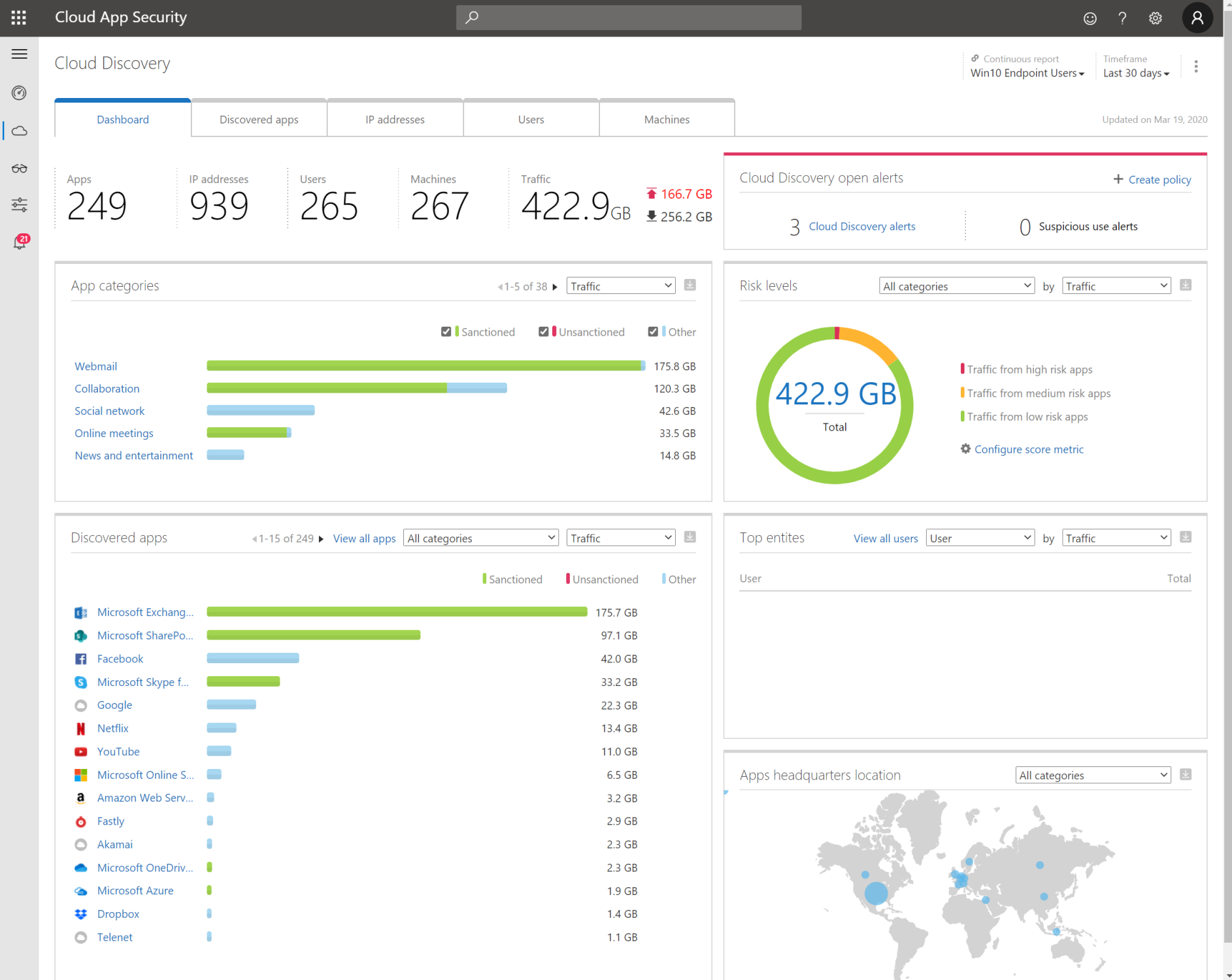
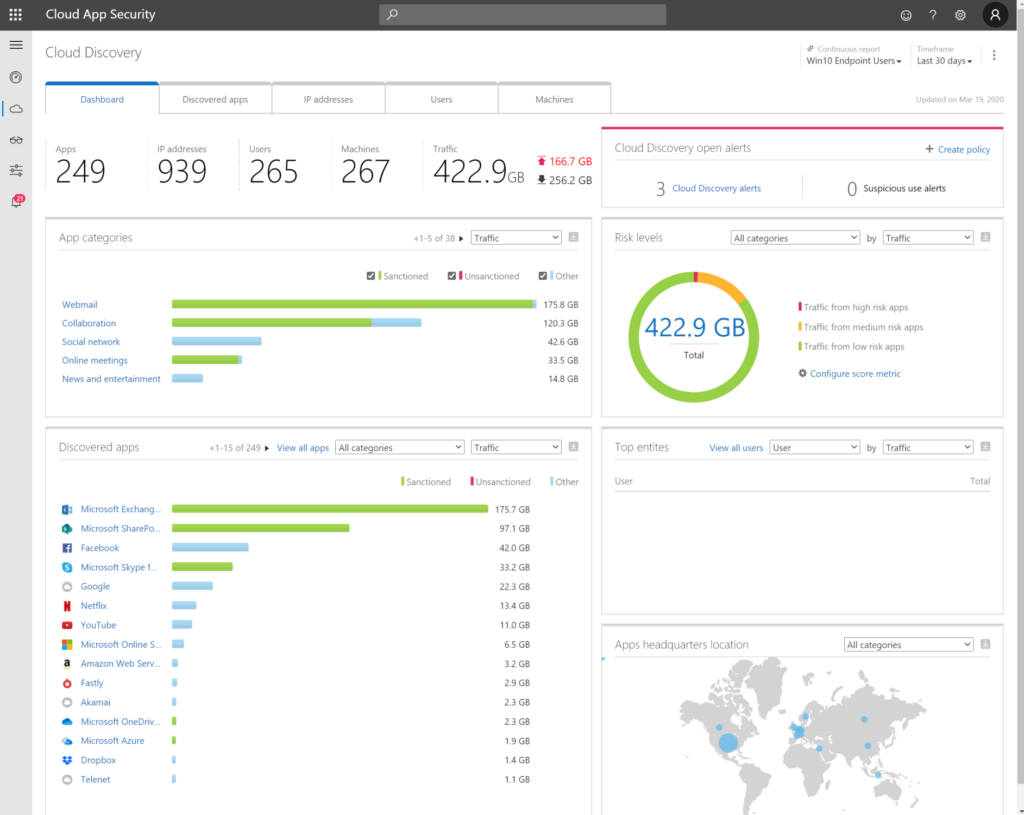
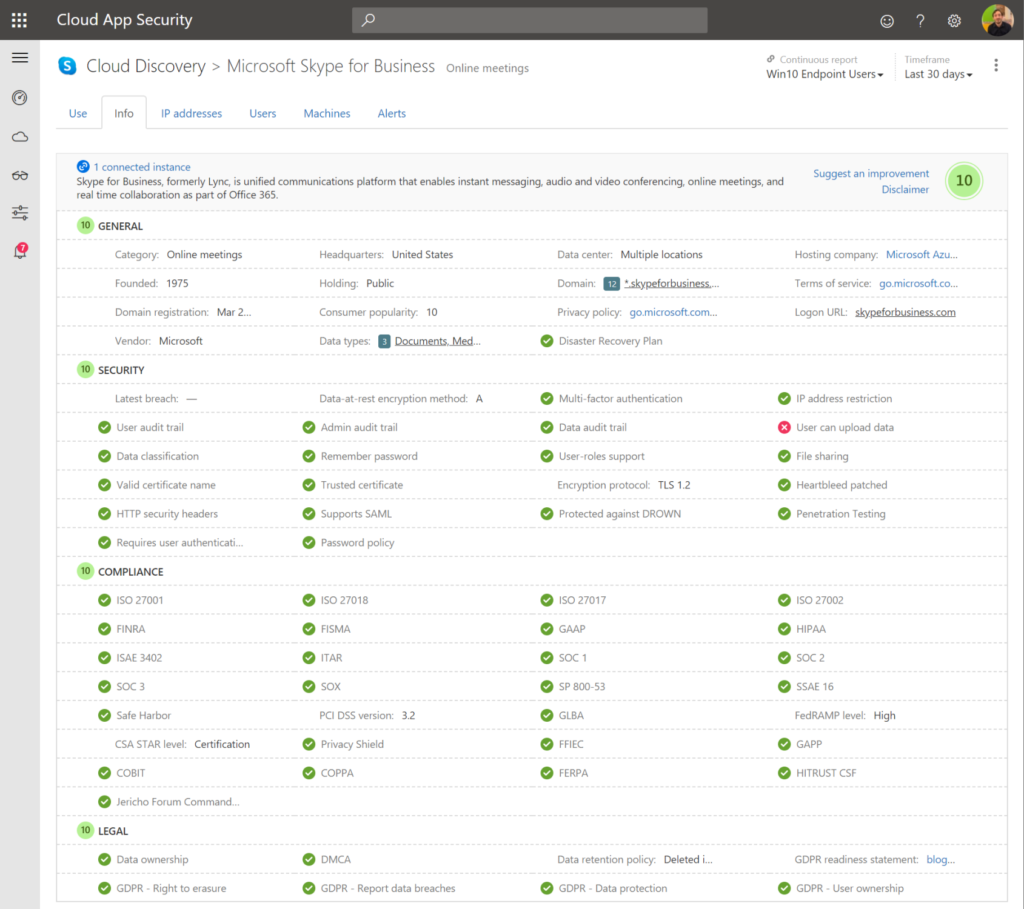
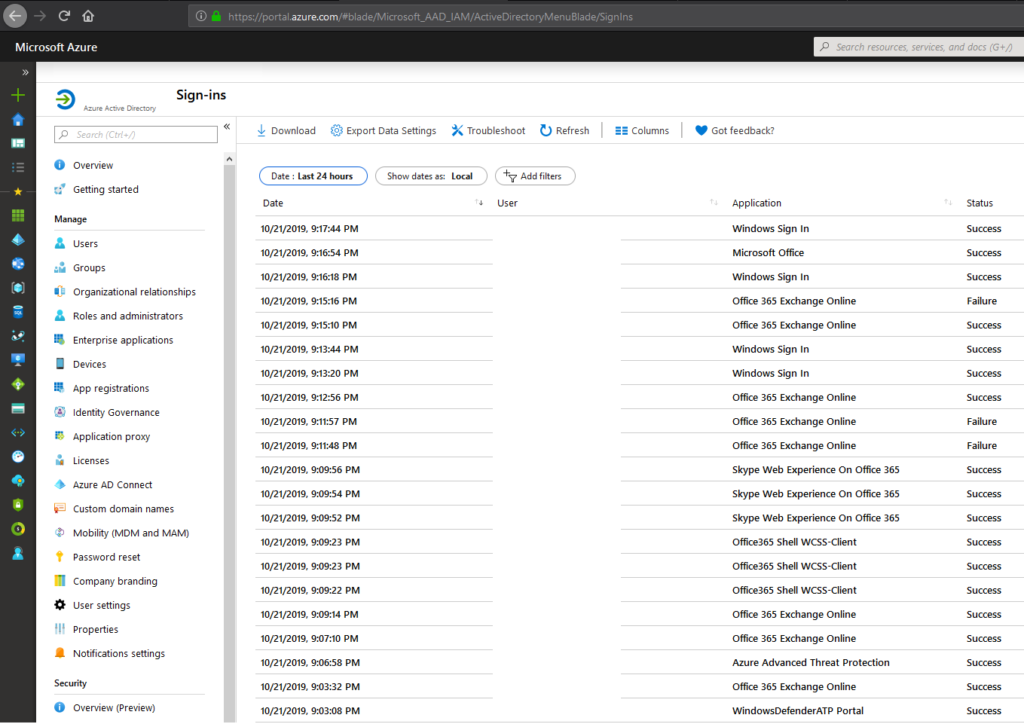
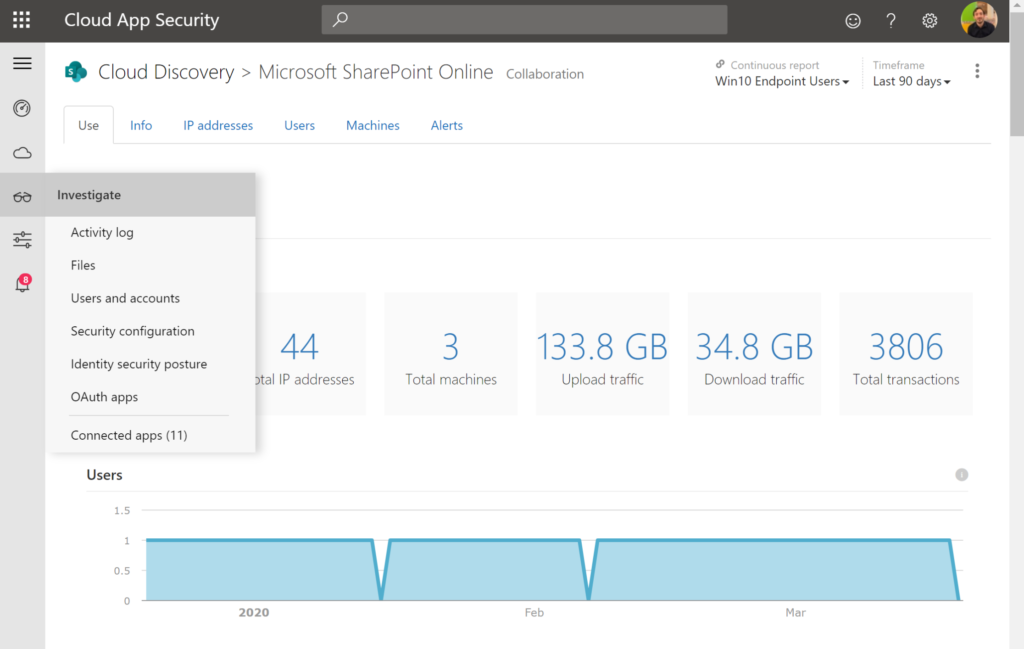
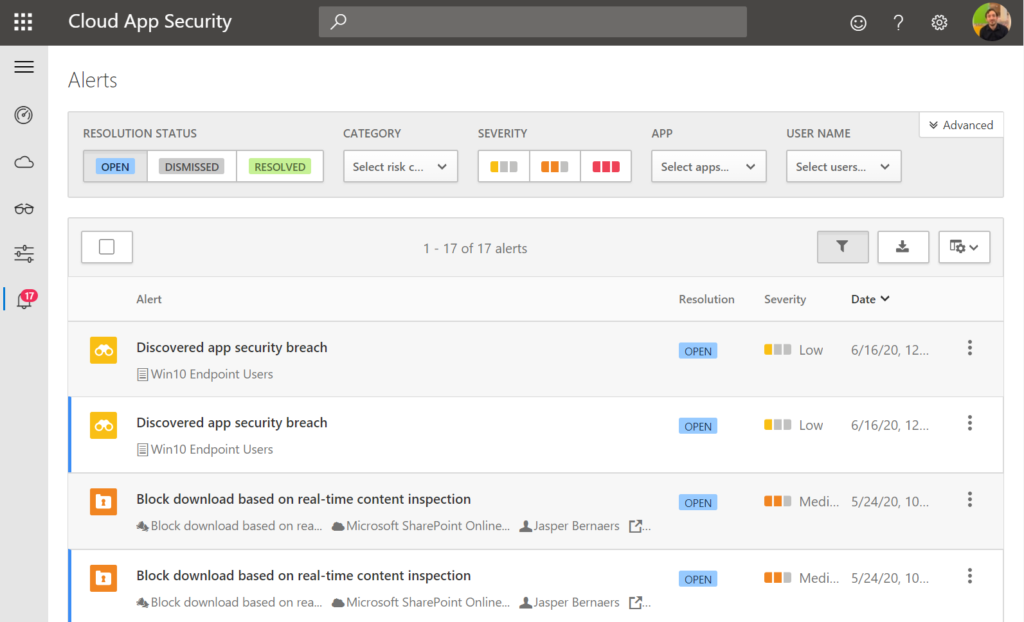
Cloud App Security: Find anomalies based on Alerts of sign in or device based.
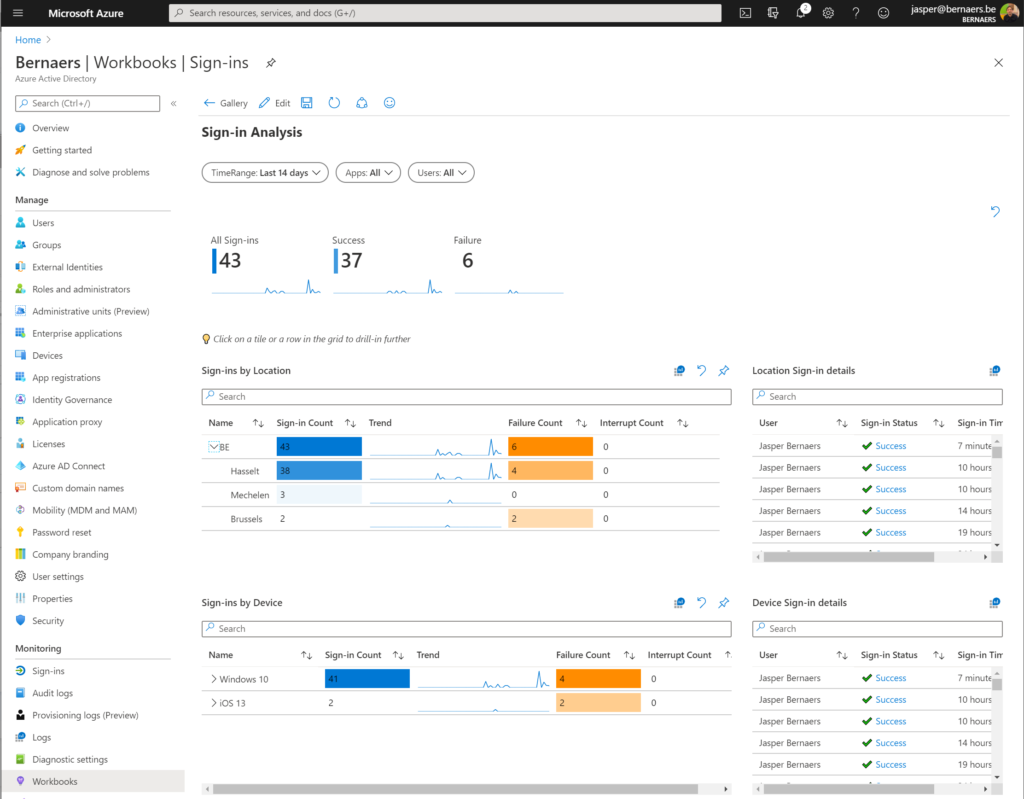
Azure Workbooks for sign-in analyses
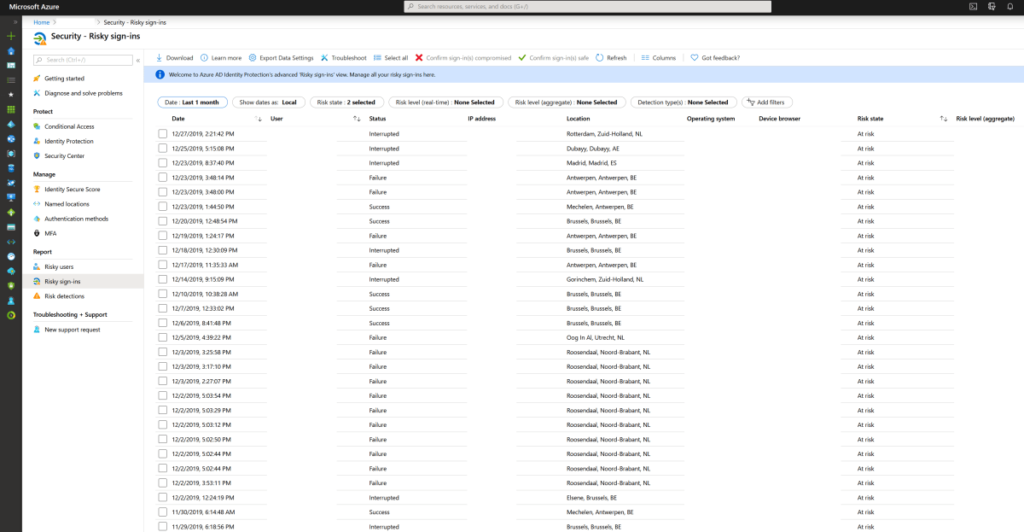
Other possibilities: Risky Sign-ins, Security center, Log Analytics queries,..
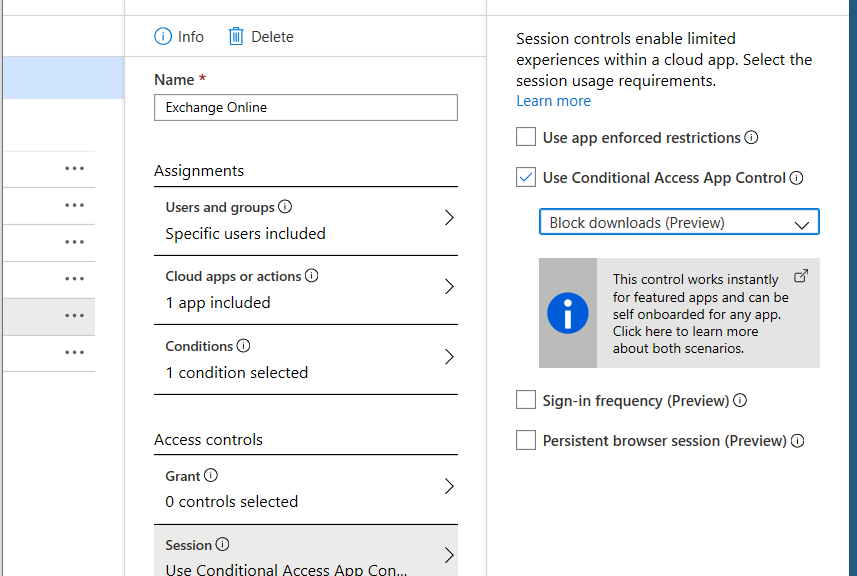
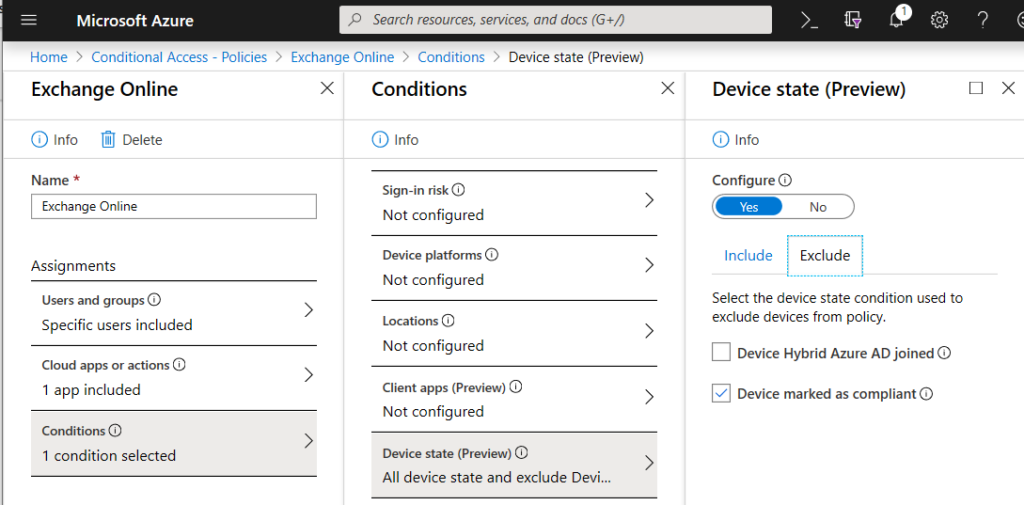
Respond (4)
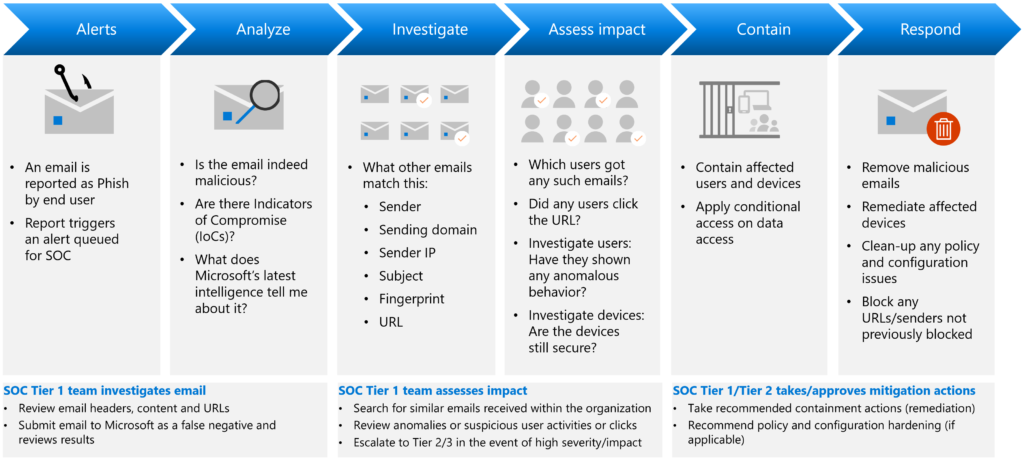
Responding is actually doing something to prevent that the breached device or identity is being taking care of. It’s doing an action to prevent different users from having the same risk. As for example isolate a device when doing to research. Or locking an account as long as the risks is valid. Also work with ATP.
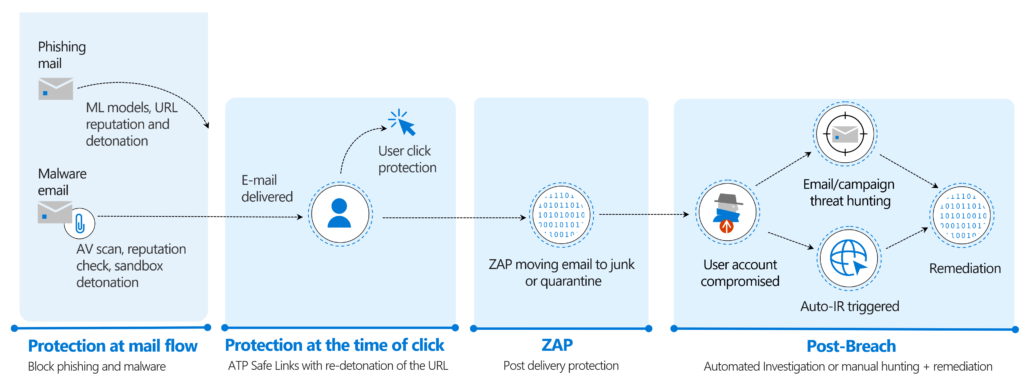
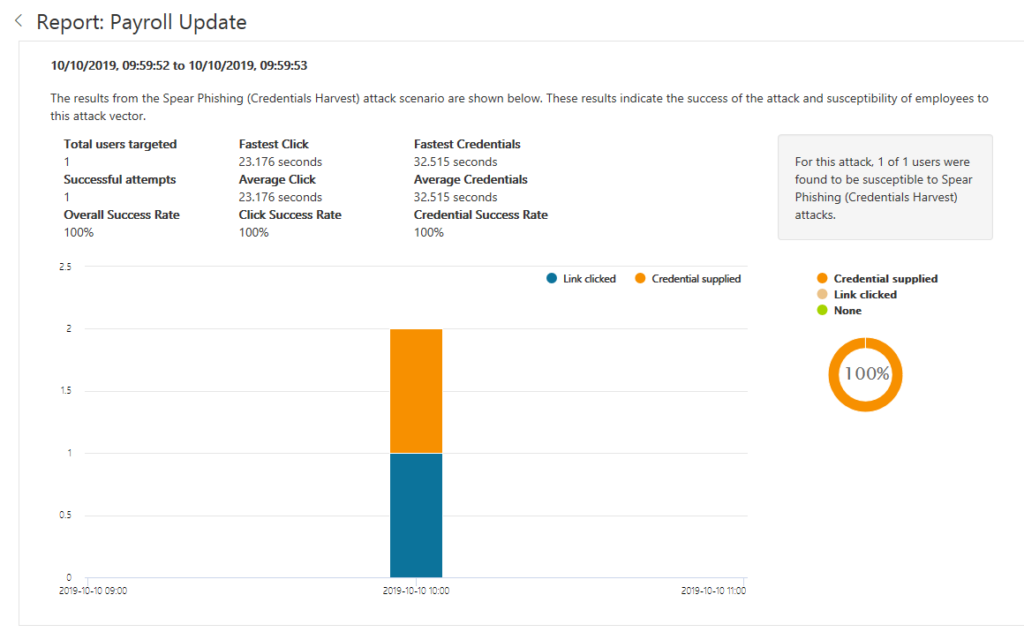
Automatic investigation can start with: User-reporting a phishing emails or
a user clicks a malicious link.
Recover (5)
Ransomware detection and recovering your files. (built-in)
SharePoint Site-restore for collections and sites. (built-in)
Backup with Microsoft technology of third-party. Azure Back-up, SQL Service backup.
Disaster recovery (Plan)
Cyber insurance
…
Conclusions
- Microsoft understand that automation is the way forward. Alerts creation, follow-up to have relations in events. It’s time to shift from complex Security Operation to understandable solutions with reporting, automation and long-term possibilities.
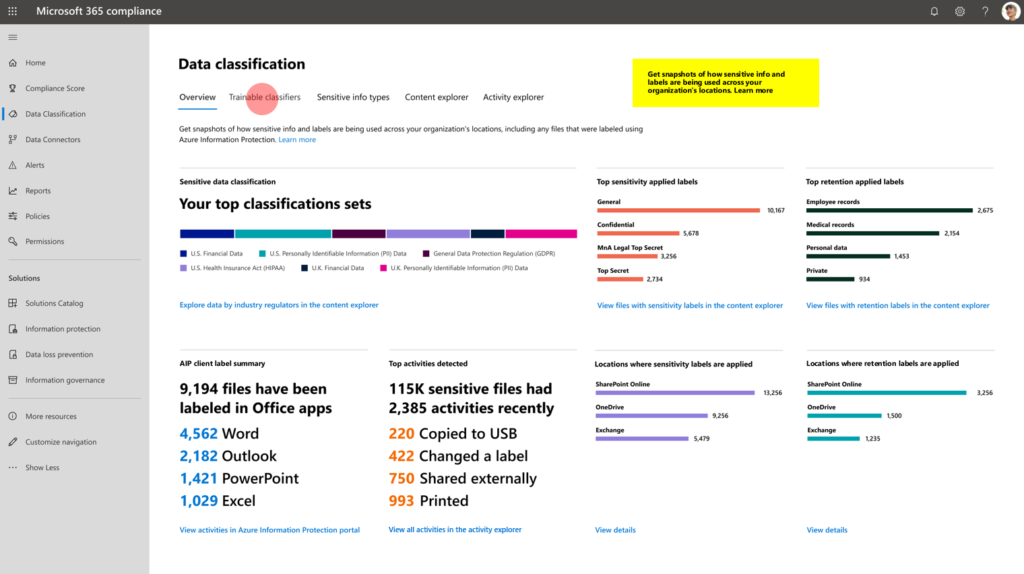
- Sensitive document data can be found in Office 365. (Exchange, SharePoint, Teams). Core-application as CRM and Server Infrastructure are integrated in Azure AD. The risks are shifting to the modern cloud. Focus on these new risks. Not the on-premises Active directory, not anymore.
- Focus on T1 and T2 automation. Next to reactive follow-up, work with the benefits of E5 MDATP. If you’re able to get the security baseline to a next level the standards will shift to a less risky environment.
- SIEM solutions can be integrated but keep in mind: If the full infrastructure + Office 365 is shifted. Do you still need an different solution on-premises or in Azure?
- Microsoft 365 E5 includes great security features with a cost. It’s best to use the full potential.
- Power Automate skills are important for SecOps and can be used for different Sysadmin tasks and other teams in the organization.
And after this journey? Logic Apps with building blocks for quick deployments and standards, reporting, Azure Sentinel workbooks with templates as in this blog, Integrations with ticket tools, prediction and whatever you like…
Thank you so much for reading! If you have feedback please comment below or reach out on Linkedin or Twitter.