Cybersecurity for local governments – in 10 steps
Thank you so much for reading my blog about: Cybersecurity for local governments.
In this article I’ve written an high-level approach for implementation and shift from a more a more classic or less secure environment towards future proof.
I would love to receive feedback in in the comment, on Linkedin or Twitter. Also read: The value of Microsoft 365 E3 and E5 or The top 10 security recommendations we should consider while working from home.
First step, zoom out
Security has 2 main challenges:
People: Awareness is the fundamental step for each security implementation. If you want to improve with ‘security’ the general thoughts and awareness. It’s a responsibility of each individual to carry out the importance of ‘doing it right’, ‘be aware’, ‘understand the risk’, ‘know what to do before opening a strange e-mail’,…
Example: If people don’t understand the risks they will not improve the organisation or themselves.
Technology: Technology can help to met the challenges of today. The main things to implement are easy and could be implemented without big efforts — but still these challenges are not implemented on 100 customers i’ve seen over the last year.
Example: Multi-factor Authentication, Enablement of conditions to get rid of pop-ups AND integrate the workstation in the Microsoft 365 stack.
Microsoft and Office 365
If your government has Windows 10 on their local machines, Office 365 for collaboration the Microsoft (only) choices already has been made.
To keep it simple: in the early days, all infrastructure was on-premises. In the modern days some things are on-premises, some are in the Cloud. If is Google or Office 365 — it doesn’t really matter. Is not on-premise anymore, documents have been shifted to cloud.
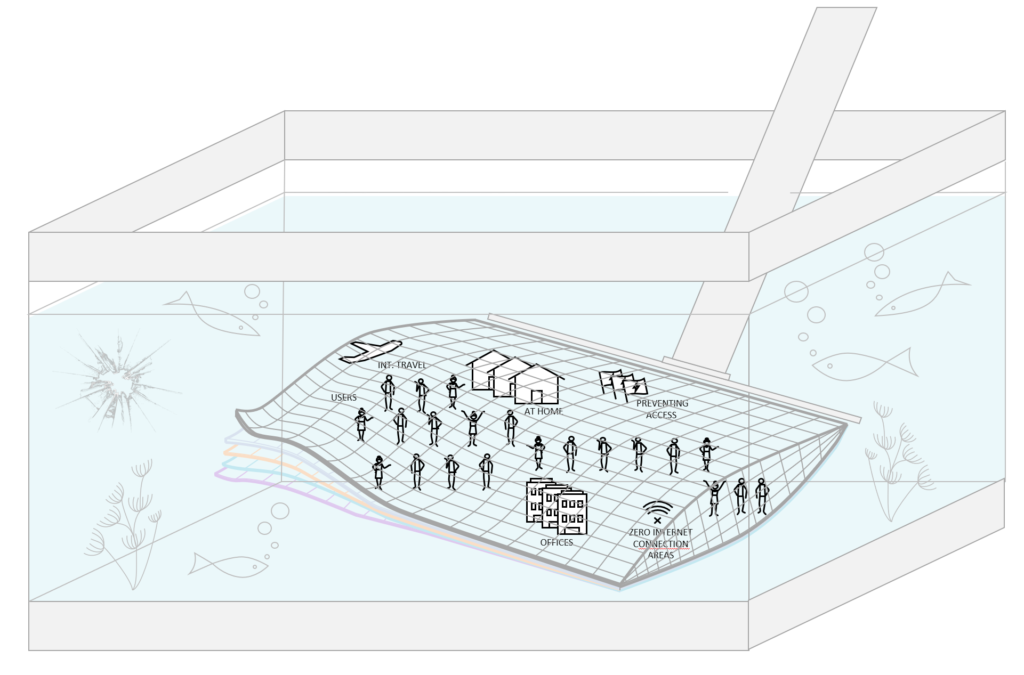
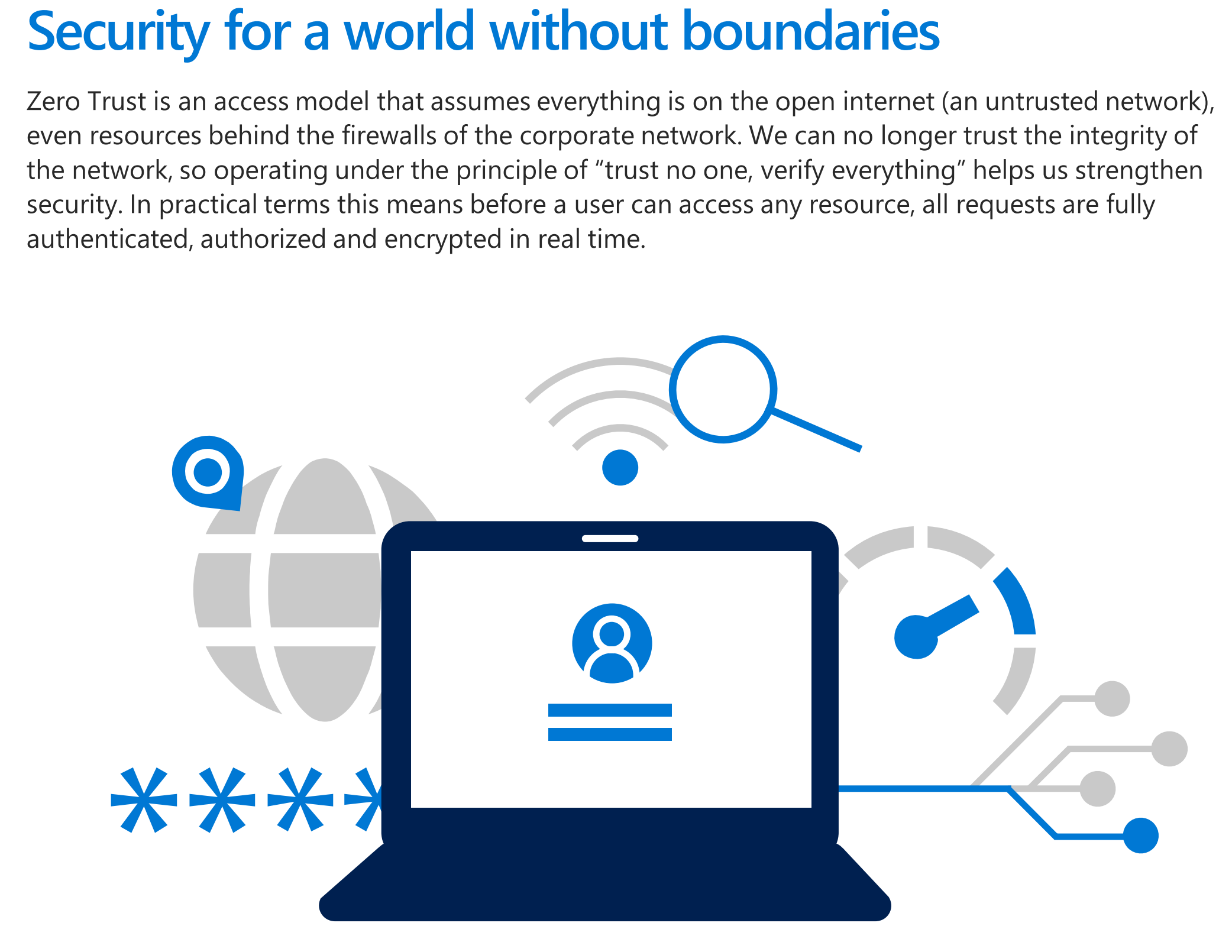
We need to think beyond the on-premise OR cloud. It’s hybrid, or full-cloud.
I didn’t see any government in Belgium yet that has their full infrastructure in the Microsoft or Amazon or different cloud.
Connecting the dots
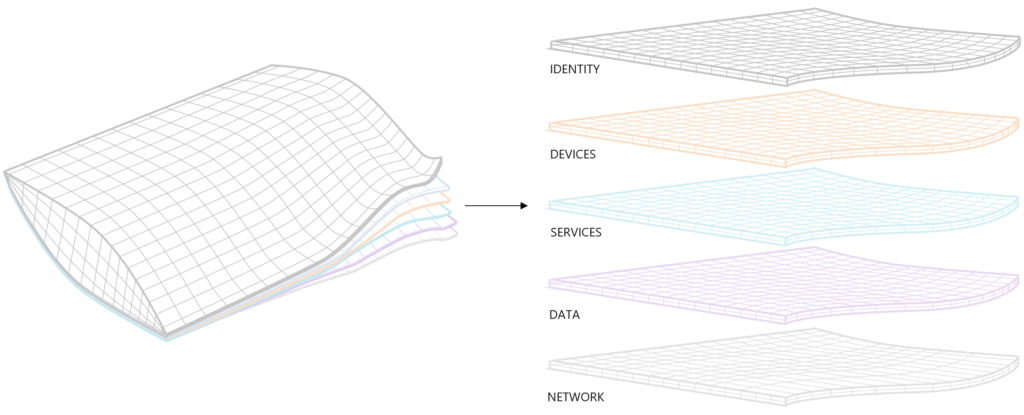
To get a simple context of improvements their is only one most important aspect. And this is: the identity. ‘The username and the password’ that lays in the heart of authenticating with your ‘account’ on your computer, office 365, Google, fileserver, laptop, computer, application,..
Next to the identity you have a device with Windows 10. That can be integrated in Office 365 for additional security. Why? To bring these 2 pieces together and connect them to understand the risks better — from a technical point of view.
If you feel the need for a deep dive read this blog.
In these 10 steps pointed out an actionplan to work and increase the security in each organization — which is a big need in governments at this moment.
1. Identity protection
- 1.2 million of all Office 365 or Microsoft 365 accounts (each month) are compromised. This represents 0.5% of all accounts in your environment. Source: theregister-co-uk
Multi-factor authentication prevents 99.9% of all attacks.
- Activate MFA, for Office 365 or Google or .. This will decrease the risk of account breach.
- Run a Microsoft Attack Simulator. It cost 2 hours. And will show the potential risk.
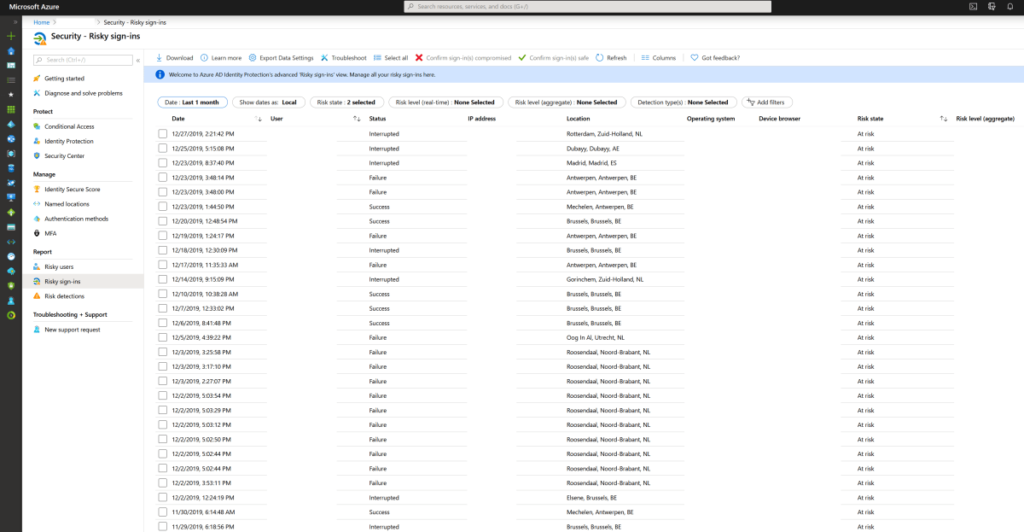
- See which account has most likely been compromised through risky sign-ins.
- IMAP, POP3 disablement and implementation of MFA in 1 click? Enable Azure AD Security Defaults

2. Patching & updates
- Take control of all devices in your organisation with Microsoft EndPoint Manager / Intune.
- Take control of Mobile Devices, or at least use Mobile Aplication Management and protect your corporate data. (iOS, Android, W10, MacOSX,..)
3. Passwords and management of authentication
- Create a password policy. Check if 100% is during renewals. Enable MFA for everyone. In case you don’t do it create policy for example: IF not with MFA than set password +100 characters. (for applications, not users) etc..
- Microsoft has advised to disable password renewals in this article. I think it’s possible IF you are doing multiple other steps of this article.
- Start using Windows Hello For Business
- Start using Passwordless Authentication
- Start using Self-Service Password Management
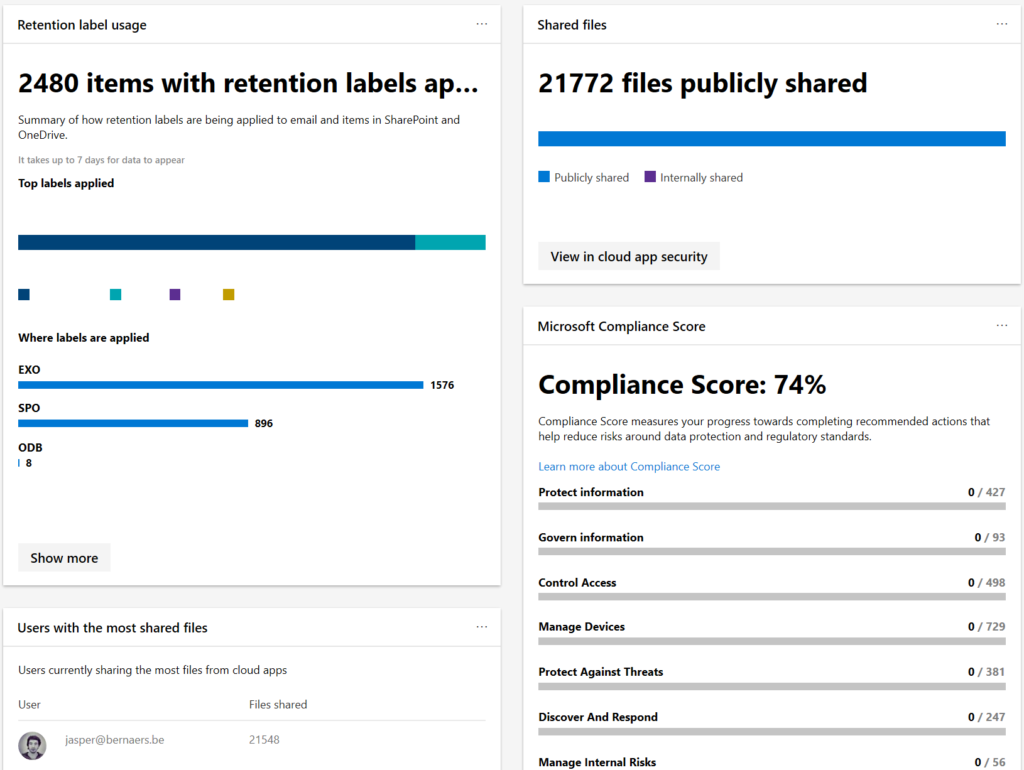
4. Create real-time reporting of security vulnerabilities
- Identity risks are in every organisation. Don’t think that your changes are low. Check the facts. It is very easy to use ‘risky users‘, ‘risky-sign’ ins and ‘risk detection’ to find out real risks.
- Integrate with Microsoft Defender ATP and ATP Sensors to have all intelligence in the Microsoft cloud.
5. Create automated and intelligent alerts
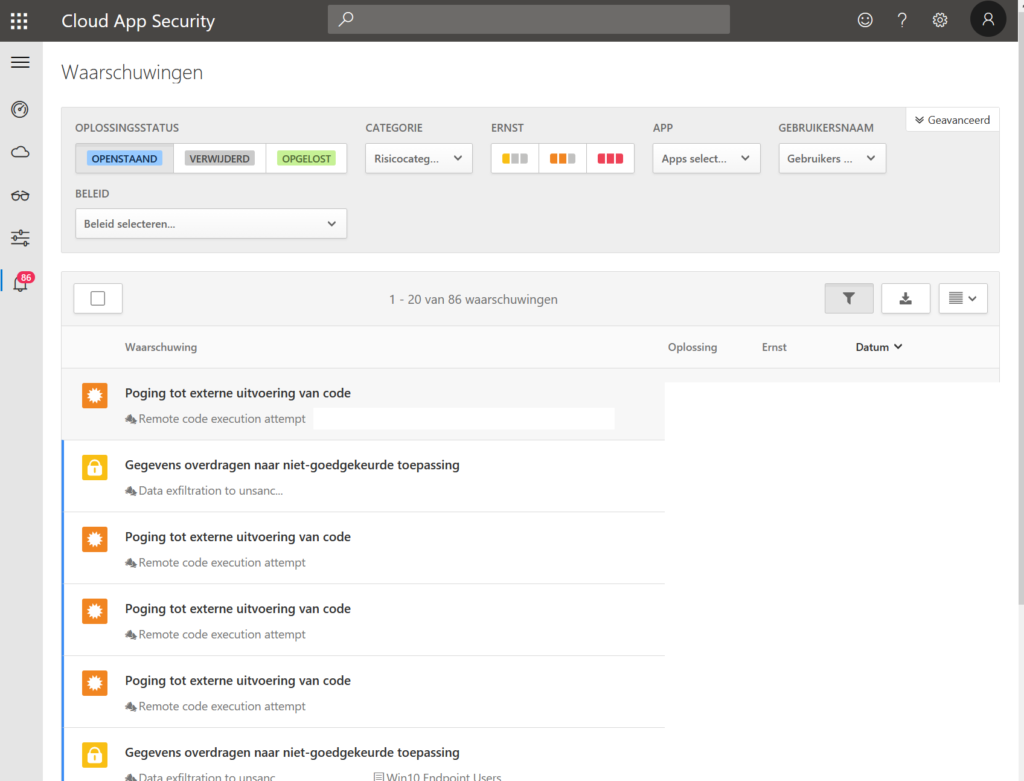
- There is only 1 answer to the ‘control’ question.. Microsoft Cloud App Security. Create alerts when 100 files are deleted. Copied to Dropbox for example.
6. Install antivirus on ALL endpoints + go beyond antivirus
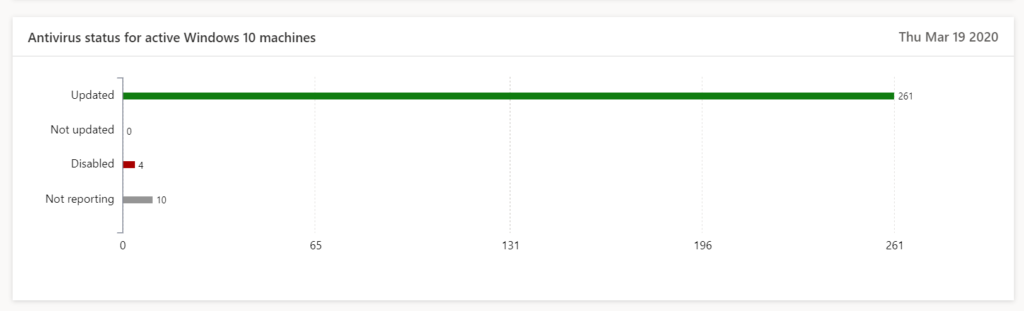
- Microsoft Defender ATP, sentinel-one, Norton, McAfee, it doesn’t really matter. As long as you are able to protect all endpoints.
- The second factor is to make sure that your antivirus is enabled. Use a single console. OR use MDATP. Set security alerts so you know when you are at risk.
- Use EDR monitors to detect and respond to advanced attacks in real time.
7. Secure private(personal) devices and corporate devices
- workstations and portables (With W10 for example) are in control in most of the companies. Mobile devices are left unmanaged because we don’t know the options.
- With Intune (EndPoint Manager) you can isolate and segment applications without having to manage the device. The corp. applications is under control. The organization’s data is protected. The most important thing is done!
- Choose a fingerprint, faceID worst-case pincode in app protection.
- Below you may find an example of the Outlook application which is protected by Mobile Application Management. In case organisations are not the owner of these devices this is a great option. And simple to implement.
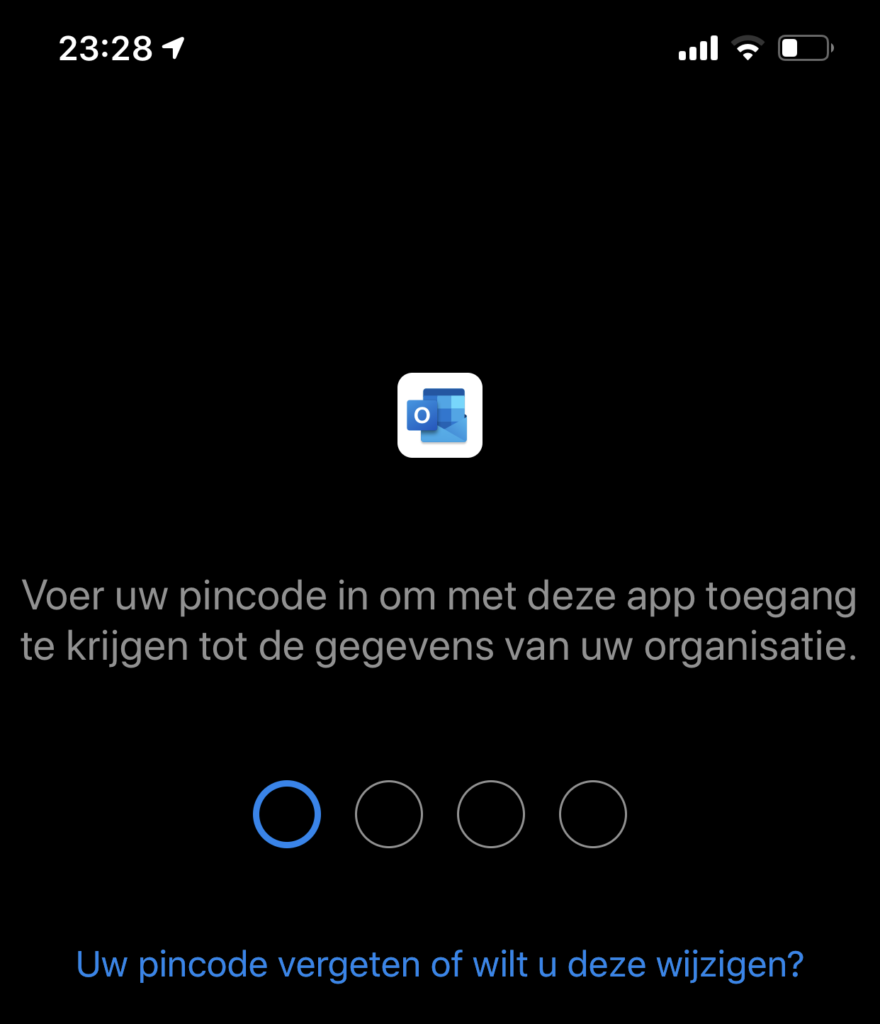
8) Evaluate regularly which users have access to data, devices and physical network
- Cloud App Security shows you exactly whether data is passing on all endpoints.
- Document data, lateral movements, usage of applications, global traffic, count of applications in use in your organisation. Risk levels, GDPR proof applications..
- Bring network devices logging in CASB to have more insights.
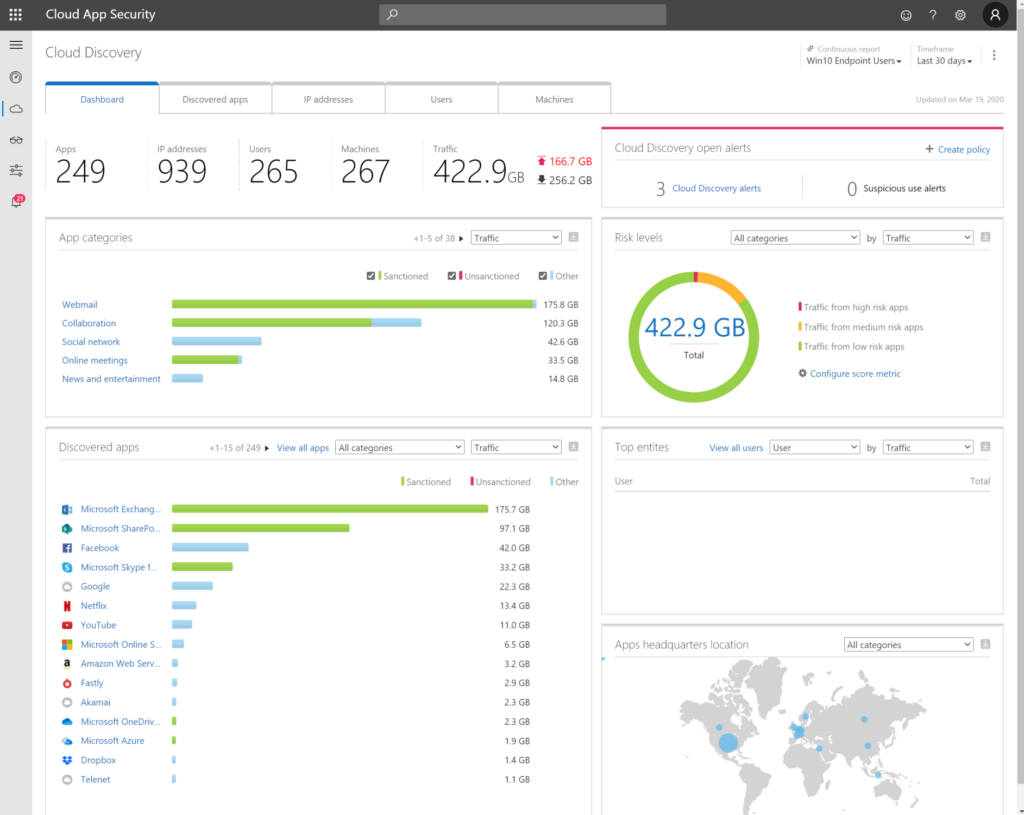
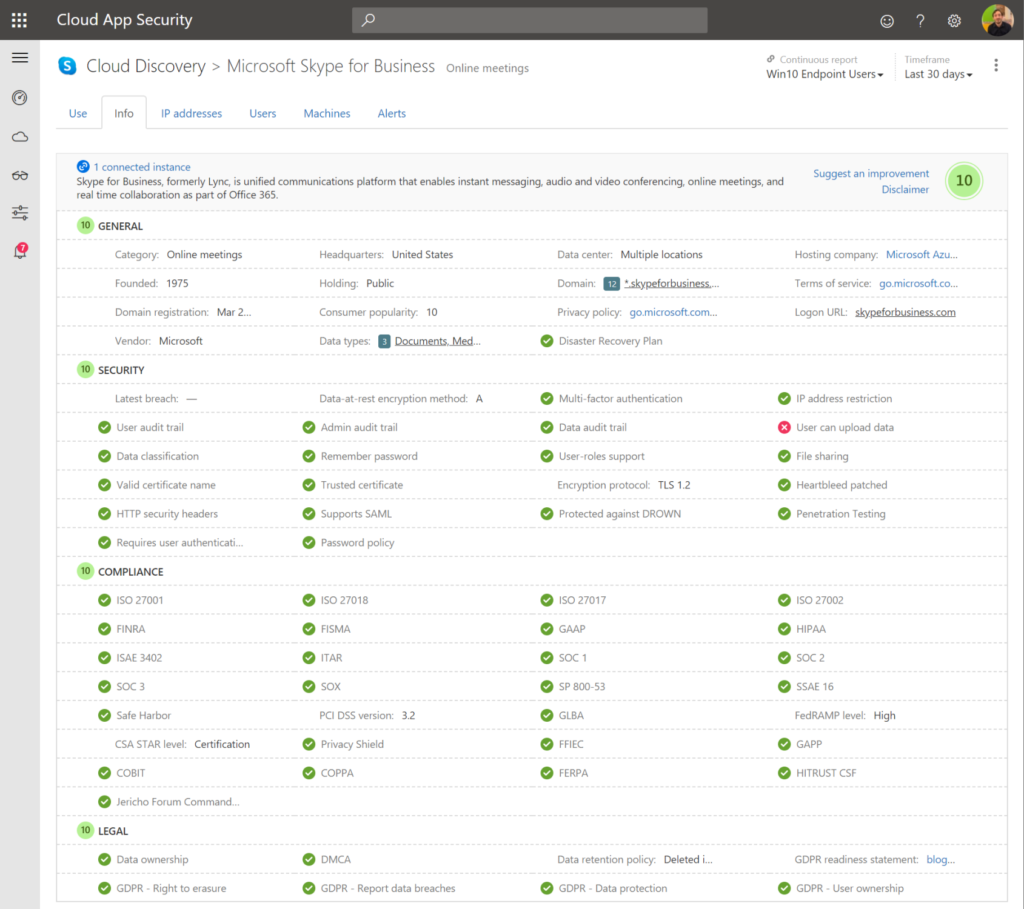
9. Track and block access for temporary projects or employees that left the company
- governance without enforcement is just good advice.
- Create simple written policies, enforce policies. Do monthly or weekly monitoring.
- Create retention policies for example in a Microsoft Team that removes the team after 180 days.
10. Use information protection to protect your data everywhere
- Use Information protection to protect document data. Even if you lose the document “physically”. There are still options to block this from opening and keep in secure from distribution, opening, editing,..
- Create document data insights from on-premises and cloud solutions with Microsoft Information Protection Policies.
Conclusions
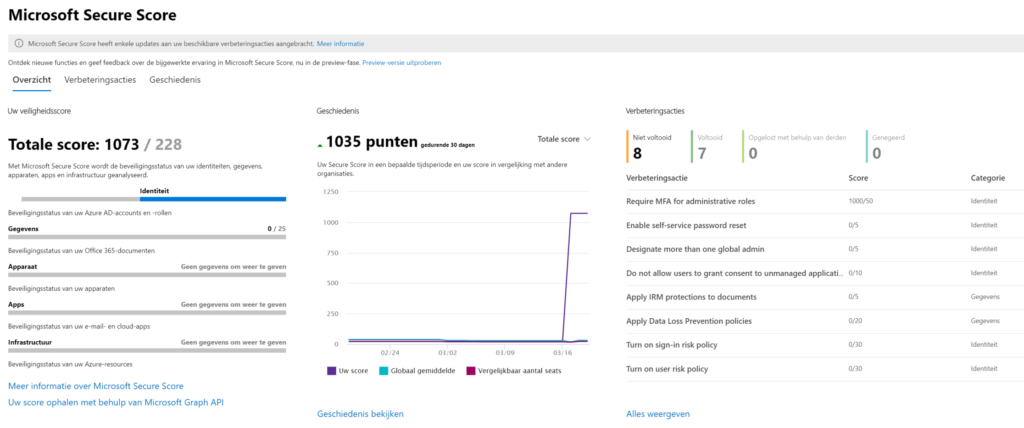
- Security priorities are difficult. However, I would always start with MFA because this is fundamental improvement for any organisation. It creates awareness + prevents risks on account breaches.
- Keep control of all assets. Implement Endpoint manager to increase the maturity of the workplace.
- Also think about automated actions. I’ve put valuable options in this blog.
- Start a security-team that is in control with deadlines and resources.
- Lets do it!
Thank you so much for reading! If you have feedback please comment below or reach out on Linkedin or Twitter.