The value of Microsoft 365 E3 or E5
Creating the modern workplace!
- Digital business transformation. Every company has a digital transformation initiative. Microsoft 365 drives this digital transformation.
- Increasing agility. The ability to respond to and drive market change quickly is the fundamental measure of business agility.
- Empower information workers and firstline workers so they can collaborate and communicate better. Internally as with customers.
- Support different working styles for millennial’s, Gen Z, Gen X, Baby boomers.
- Generate better intelligence and analytics with a single view into your company information!
- Increase mobility. people are working from home. From clients and during travel. In regard to collaboration, 98% of information workers collaborate or communicate with someone else at work on a weekly basis.
- Improve security and compliance. Most of the time there is no control of data compliance in the current on-premise environment. Security systems are complex and static without growing or proven improvements. Start with a Zero Trust model.
Microsoft 365 E3 OR E5?
- Decision making is crucial. Also simplicity. Make IT-system simple to move faster and support your business better. 2-3 Flavors of license scenario’s or strategies will be great. Don’t mess with addons id you will not use or active them..build trust, choose platform, choose Microsoft.
- Start with activating basic security mechanisms. Start support of what you are using. grow. Don’t buy E5 when you are not mature enough, yet. Buy E5 and enable CASB to understand shadow IT or act when people extract crucial organization data… etc..
- Don’t think it’s complex. Even when your company size is 50 people. You could start using Microsoft Business, full cloud. With real value and benefits as in Microsoft 365 E3. You could even use M365 E5 for small business when data control and cloud security is required.

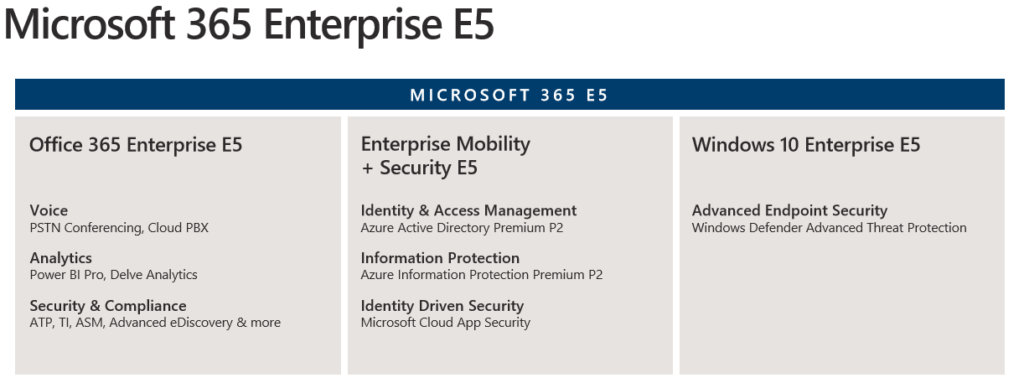
Office 365 – standard set
- Every company is using e-mail, calendar, contacts move to exchange Online. it’s a proven standard.
- Voice, Video, Meetings. Microsoft Teams. It’s used by 500.000 organization and became a standard. Shift to Microsoft Teams for better collaboration.
- Office ProPlus: Everyone is using rich office clients: Word, Excel, PowerPoint. It’s there for decades and became a standard.
- Planner, Yammer, OneDrive, SharePoint,.. it isn’t always a standard but we currently have tools to Plan tasks, Share thoughts, Share Documents and colleborate in our organization. Proven standard
Office 365 – advanced
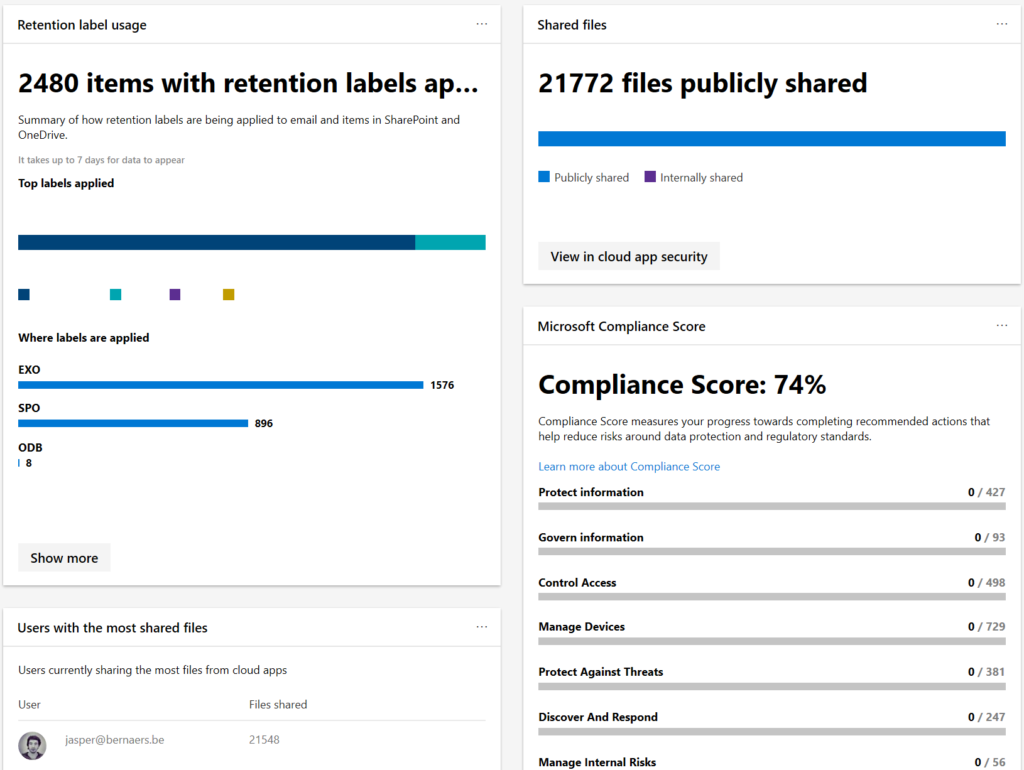
- ‘Built-in’ Analytics – did you know there are free/default/built-in dashboards for a lot of Microsoft 365 Services. I know. These are not organizational related. So they can give rich insights of usability of Office 365 tools.
- Workplace Analytics for example: Measure progress toward transformation goals or Evaluate effectiveness of change efforts. Measure meeting hours, Discover inefficient processes, Identify hurdles to innovation, Gaps in learning, Identify Influencers,..
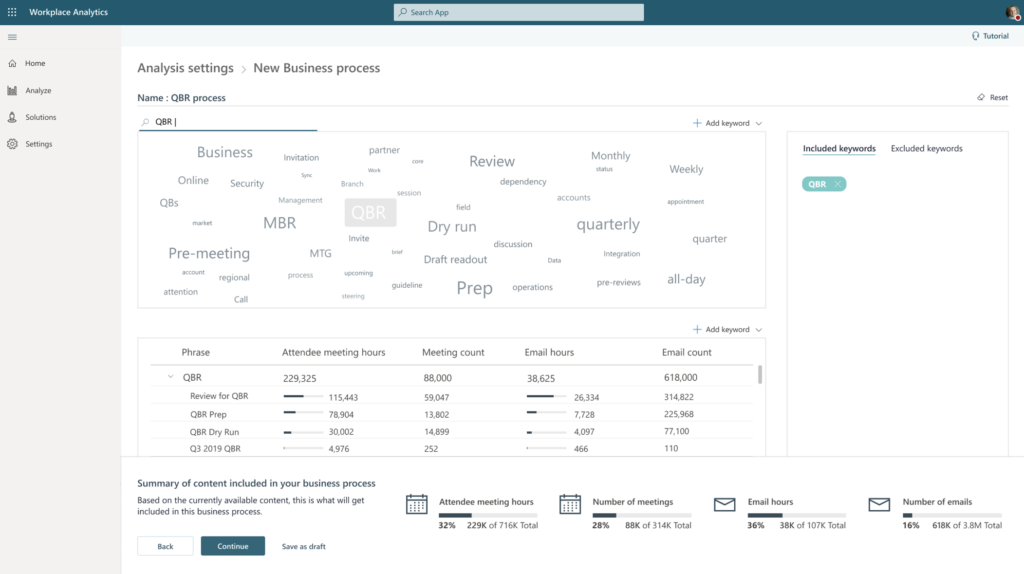
- MyAnalytics: It’s not to control – it’s to to help to find out how work is done. People in your organization can find out their own habits because of their Analytic-insights.
The bigger picture – Why?
To bring value of Microsoft 365 E3 or E5 it’s important to understand the bigger picture. In the underlaying topics I’ve brought as much features in the eco-system of the E5 license. The main question is what are the benefits for a organization to shift to cloud solutions?
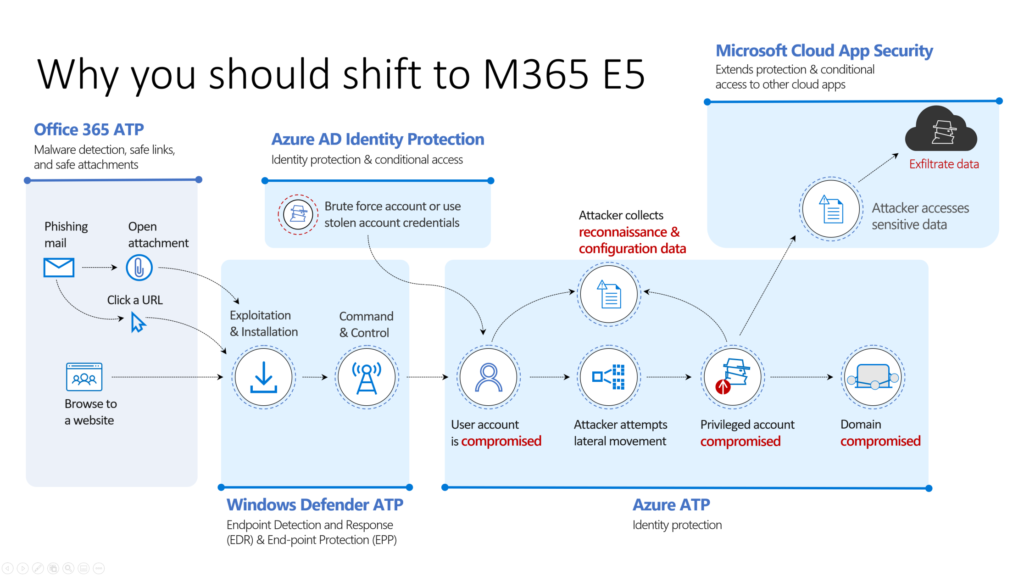
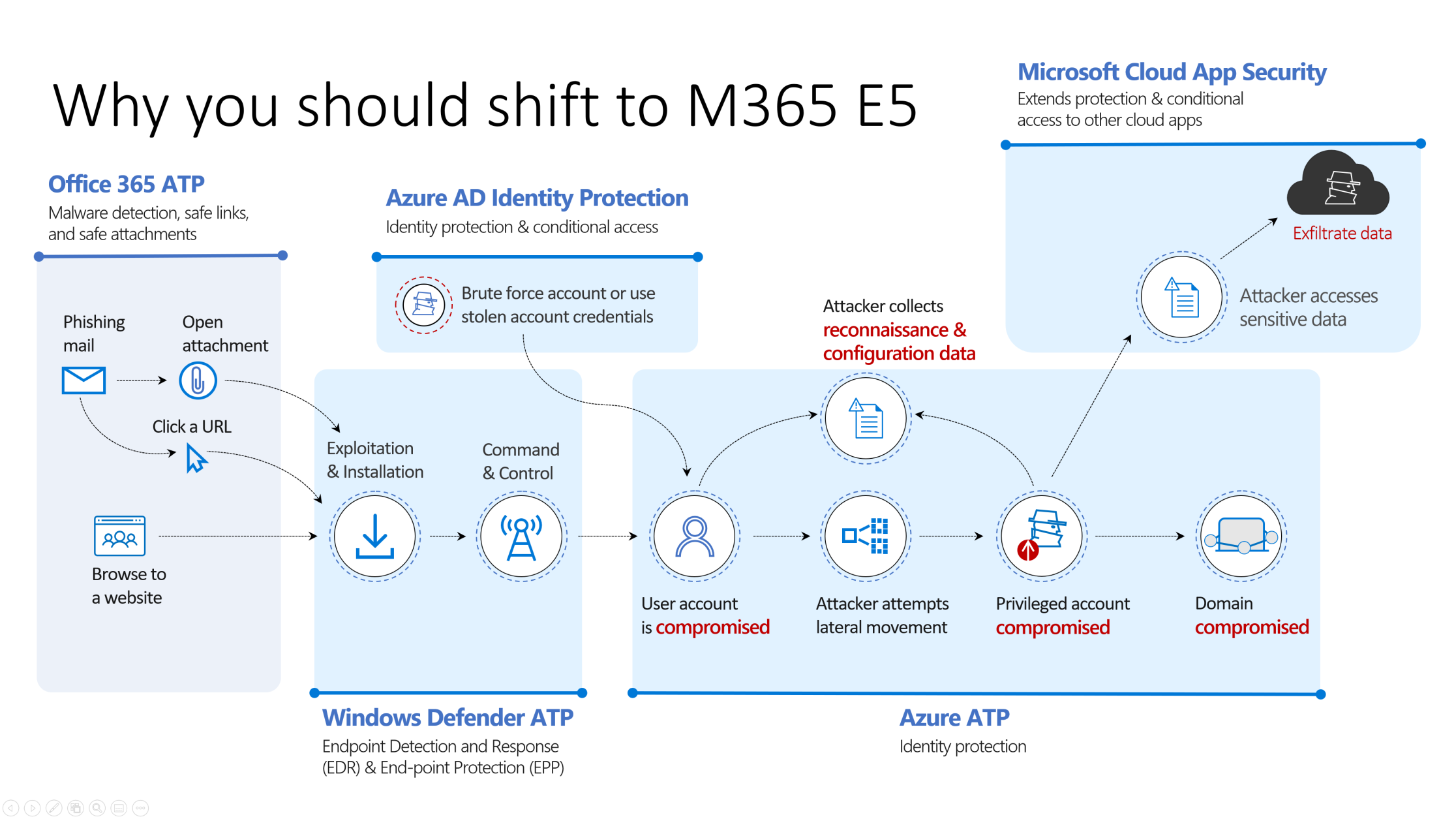
1. Protection across the attack kill chain
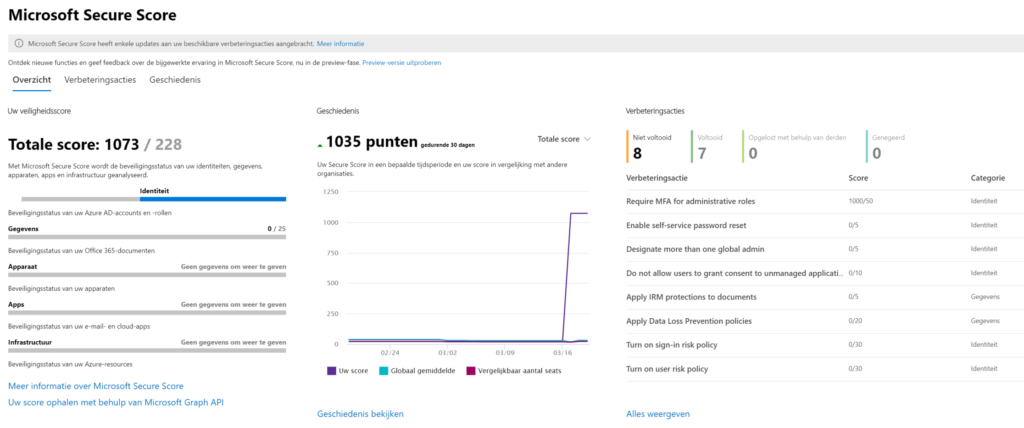
This slide shows the real value of Microsoft 365 E5. A lot of customers al laughing with MDATP because they think this is a isolated product. And are going deep in the license compare strategy of their current antivirus. Have a separated anti-spam solution, NO Azure AD Protection, NO cloud App Security..
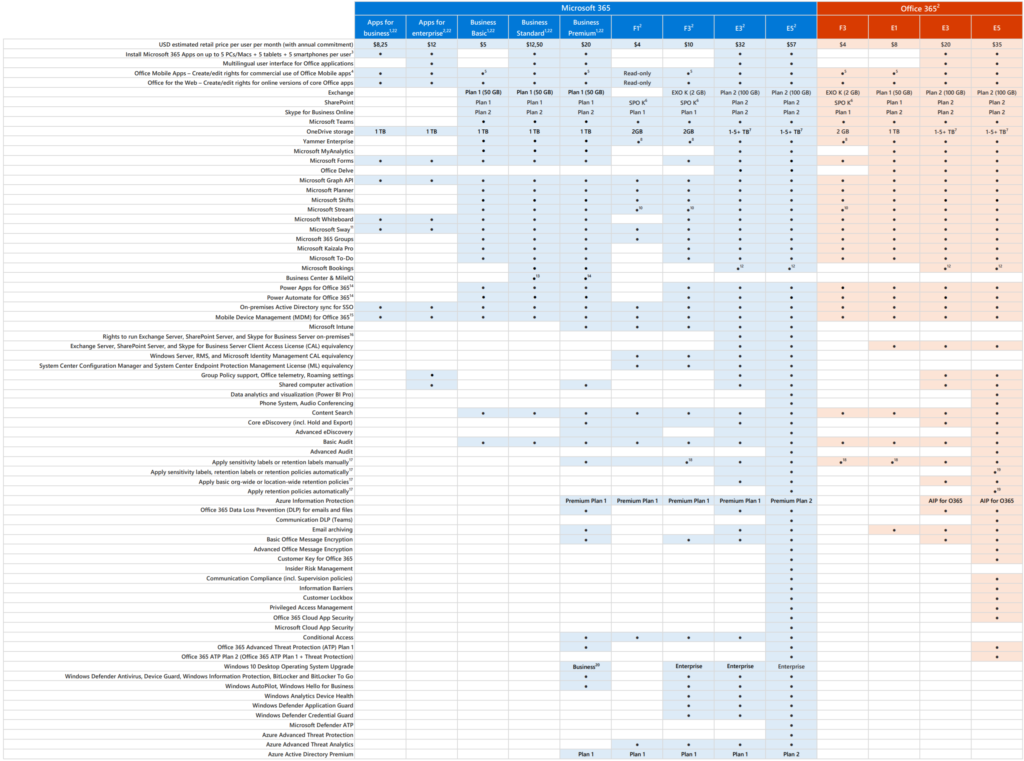
2. Microsoft 365 E5 license includes
O365 ATP, Windows Defender ATP, Azure ATP + Cloud App Security. Detailed descriptions can be found on the website of Microsoft.
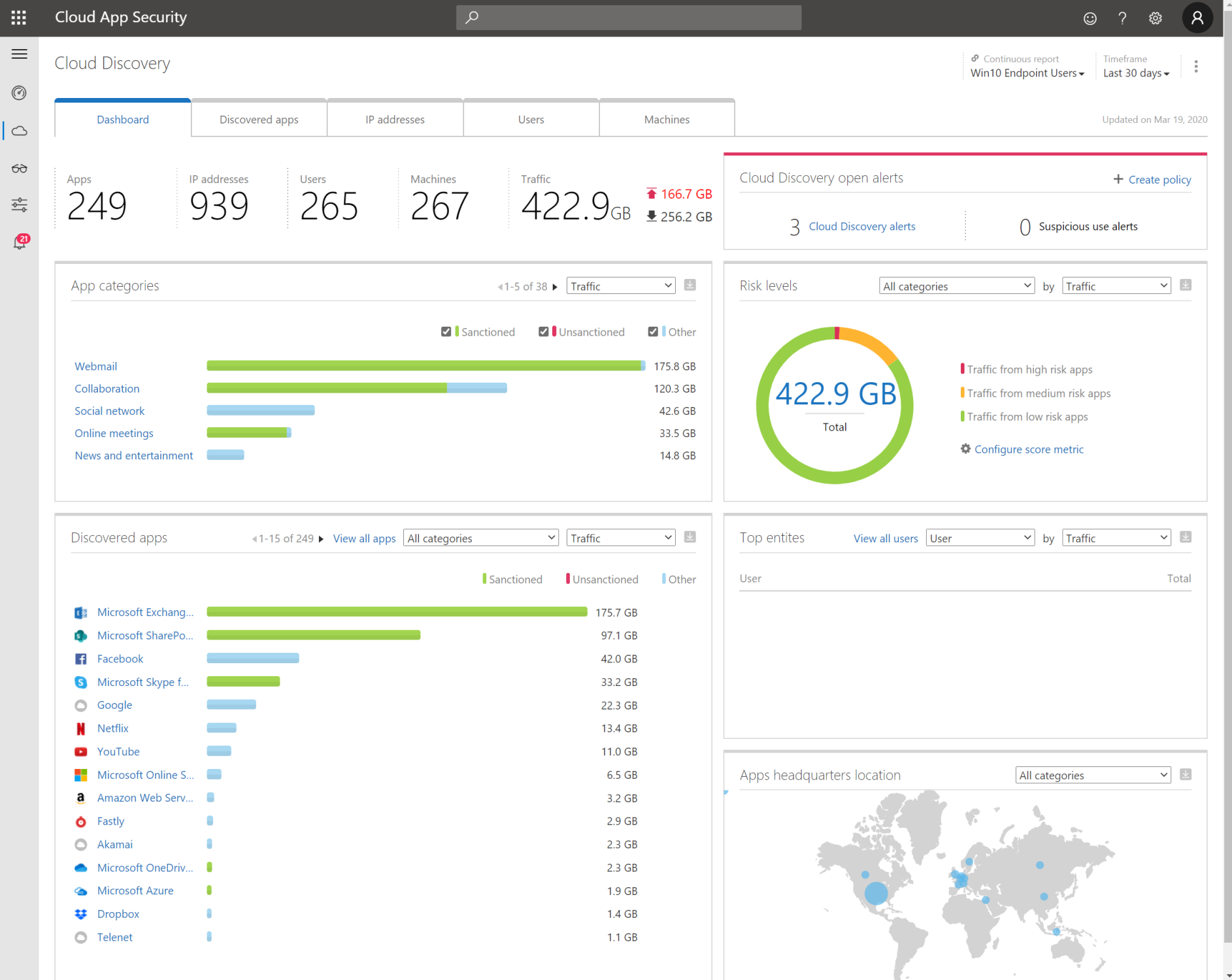
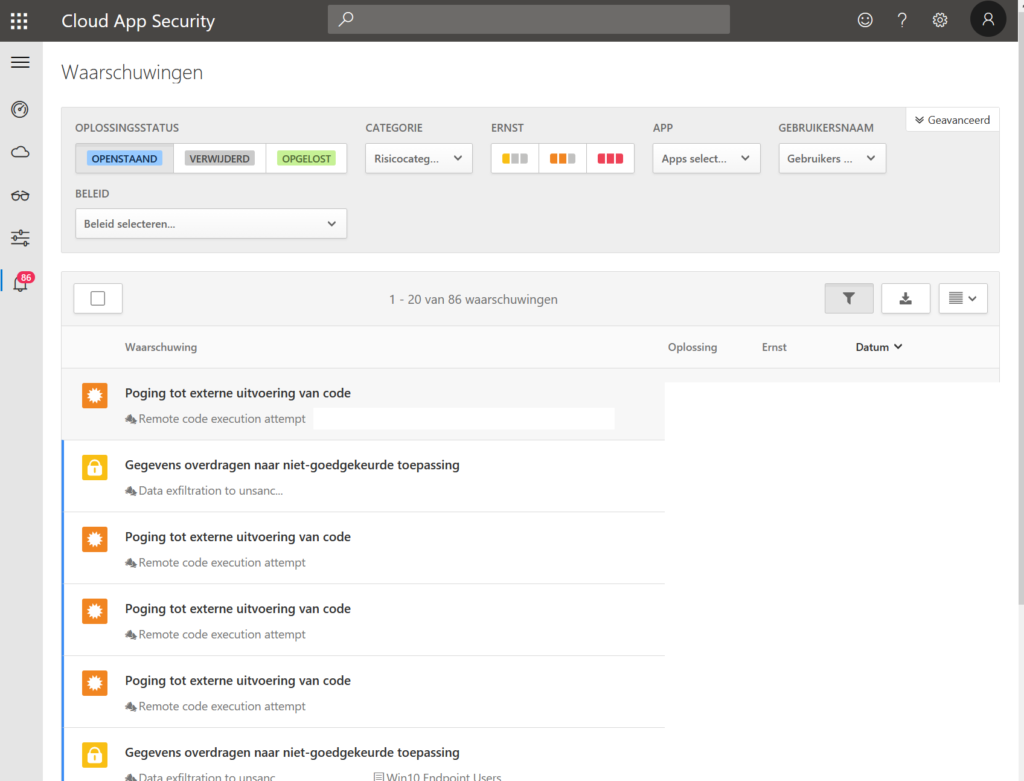
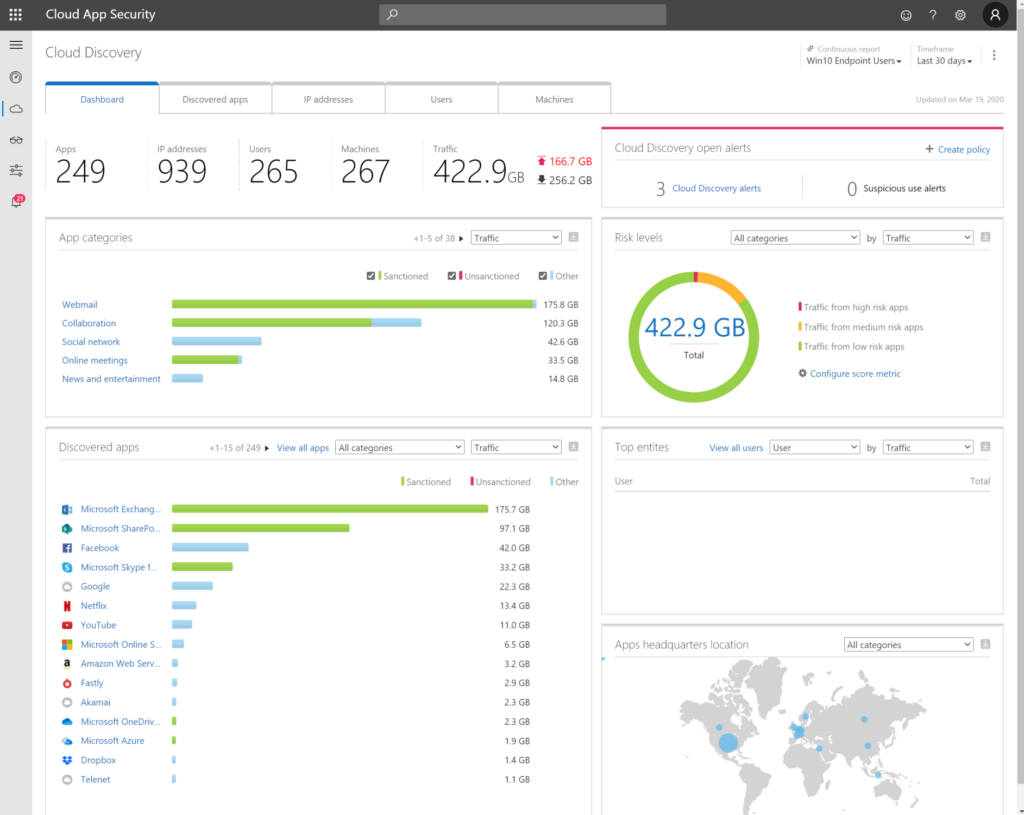
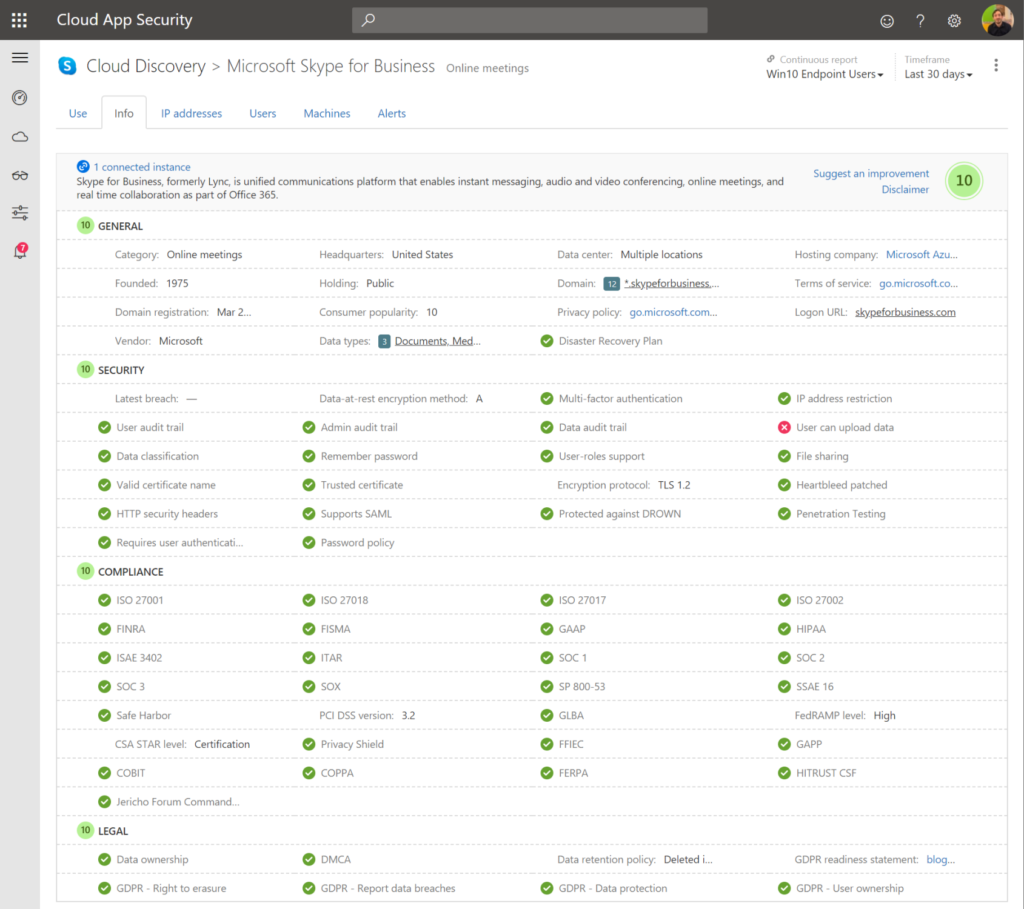
3. Cloud App Security
Cloud App Security shows you exactly whether data is passing on all endpoints. Document data, lateral movements, usage of applications, global traffic, count of applications in use in your organisation. Risk levels, GDPR proof applications. Bring network devices logging in CASB to have more insights.
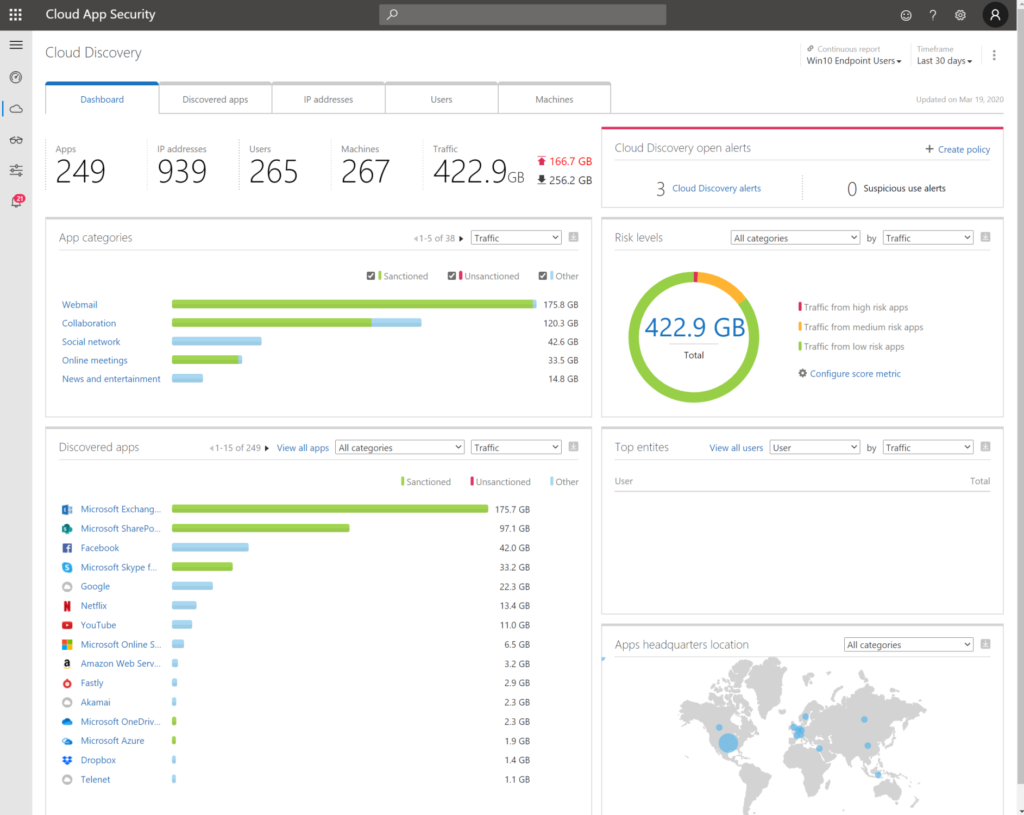
4. Security & Compliance
I’ve seen that there a not enough organizations aware of the richness of the Security & Compliance possibilities in Microsoft 365. Because of shifting to Microsoft 365 the compliance will be in control of your organization. Even if you leave some file-servers and SharePoint services on-premise.
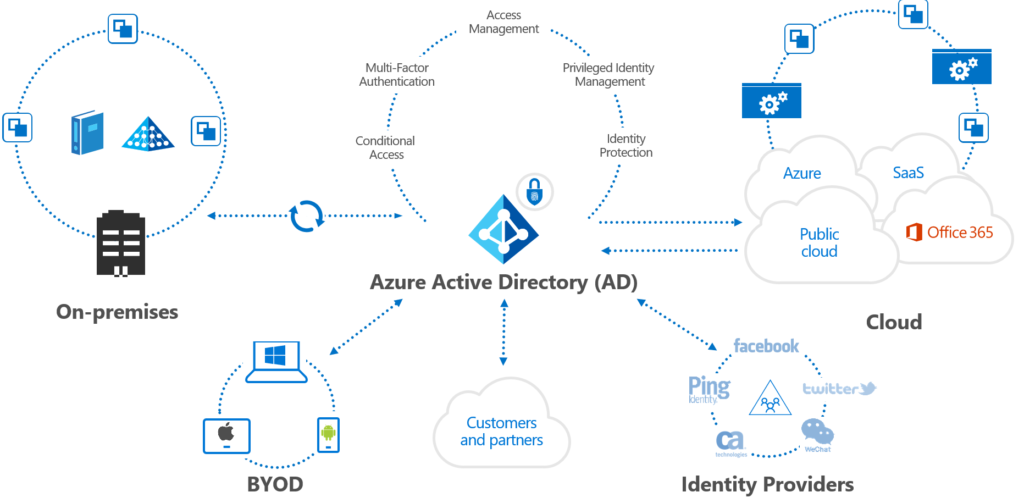
5. Identity & Access management
Because of simplified Identity management organizations are able to work with Security perimeters to protect their users and organization. Because of these simplified configuration users will be able to reset their own password, control their own devices, or configure additional security components. (ZERO-IT)
6. Self-Service Password Reset (SSPR)
The SSPR possibility Is an Azure Active Directory (AD) feature that enables users to reset their passwords without contacting IT staff for help. People can unblock themselves and continue working no matter where they are.
7. Managed Mobile Device
Cloud intelligence drives management. Use Autopilot to roll-out new devices and Increase productivity, reduce help-desk costs and Provide the best employee experience. Manage you Windows 10 devices and your mobile devices. Stop allowing personal devices without taking control of organization data. Use MAM and be diplomatic for end-users.
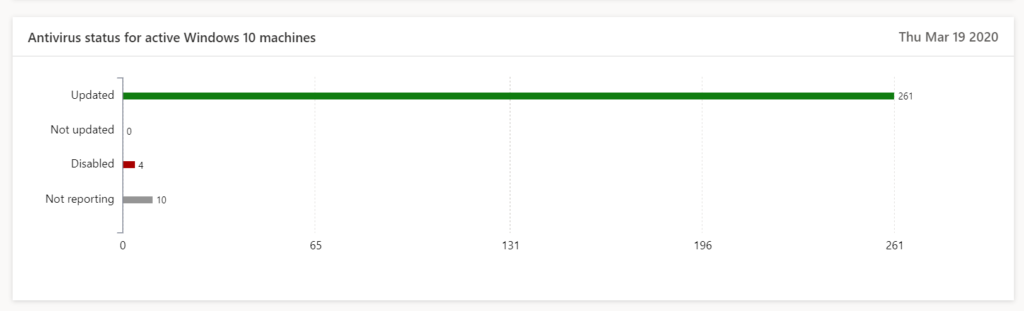
8. Microsoft Defender Security Center Security operations dashboard
The Security operations dashboard is where the endpoint detection and response capabilities are surfaced. It provides a high level overview of where detections were seen and highlights where response actions are needed. USE your built-in possibility for SECOPS reporting. You HAVE IT.
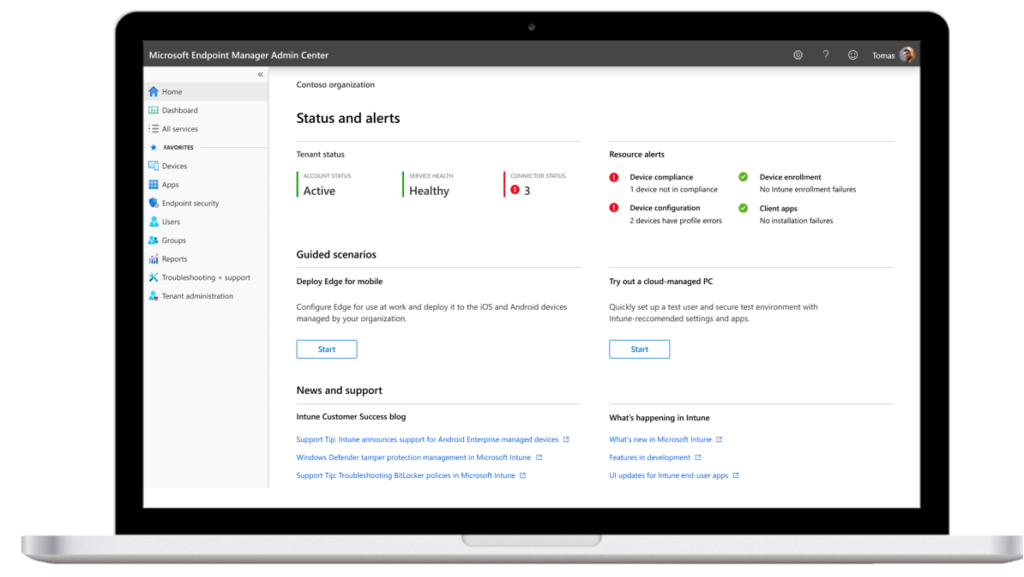
9. Identity driven Security
Because of the use of a single identity in Azure. Or hybrid synced from your local Active Directory services organizations will be able to protect and automatically act when necessary. request for update your password if breached. Ask MFA when your device is not trusted. etc.. let your users update their password from home. Increase productivity.
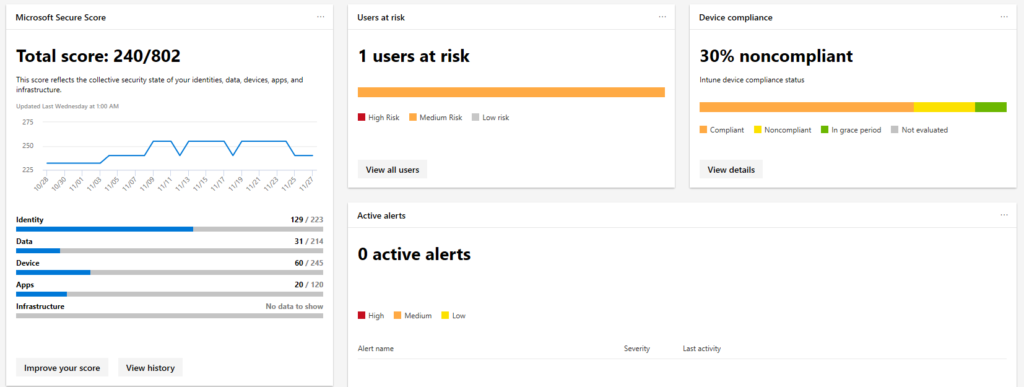
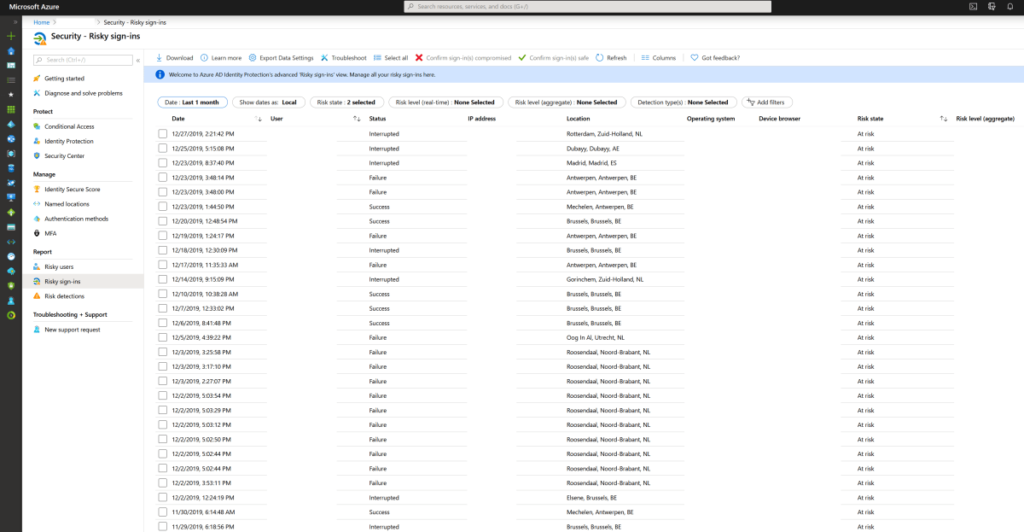
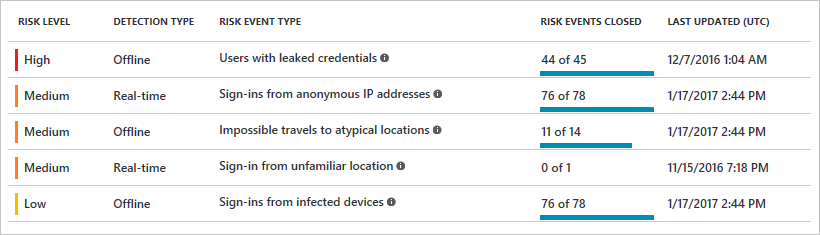
10. Risky Sign-ins
This great feature will bring based on cloud intelligence insights to understand the RISK of a user. for example unfamiliar location, anonymous IP addresses, leaked credentials.. (more info here)

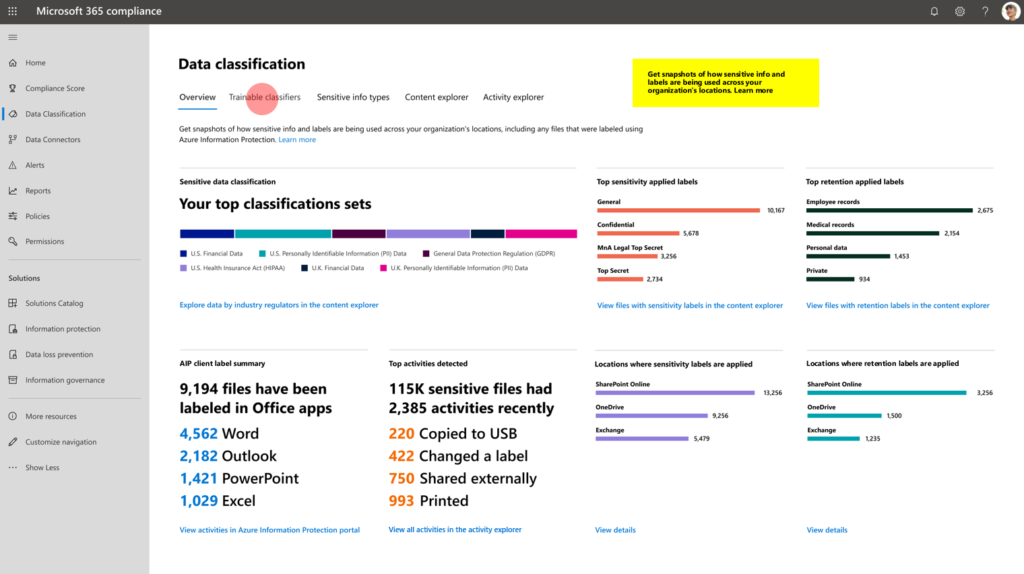
11. Information Protection
To start with classification and labeling of document choose your battles. Define 1-2-3 labels for example: “High-Confidential Internal Only”, “Public” and “Internal Only”. It’s a good start without auto-labeling documents so people can learn how to protect their confidential data. In a later phase you can enable auto-labeling when a document is highly confidential because of there are credit-card numbers, personal information etc in this document. The activation of Information Protection could come from the fact that 1 million files are shared with external people. Or that you want to stop third-party applications so company data stays safe in the environment.
12. Advanced Threat Protection
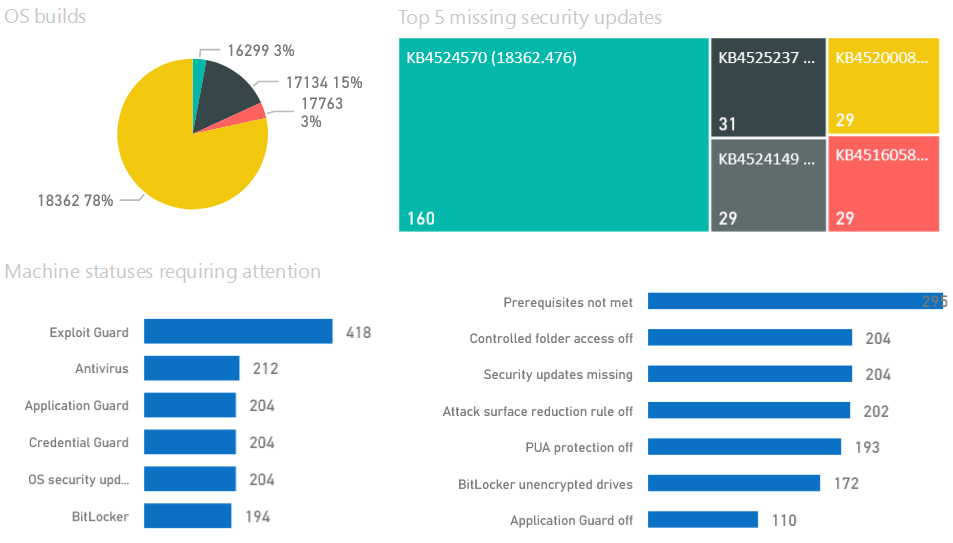
Work with Microsoft Defender Security Center (previous WDATP) it will give you insights for Applications, OS, Network, Accounts, Security Controls + Give insights for Software patching, Top vulnerable software, Top exposed machines. Most reports are built-in and seamless integration is done in the Eco-system of Microsoft 365 E5.
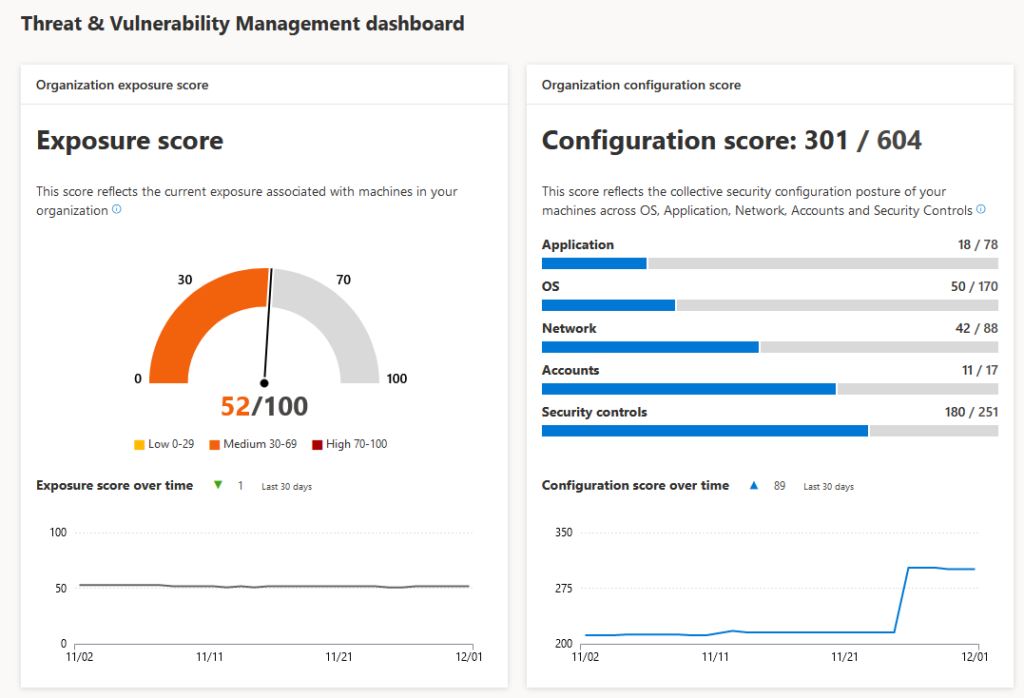
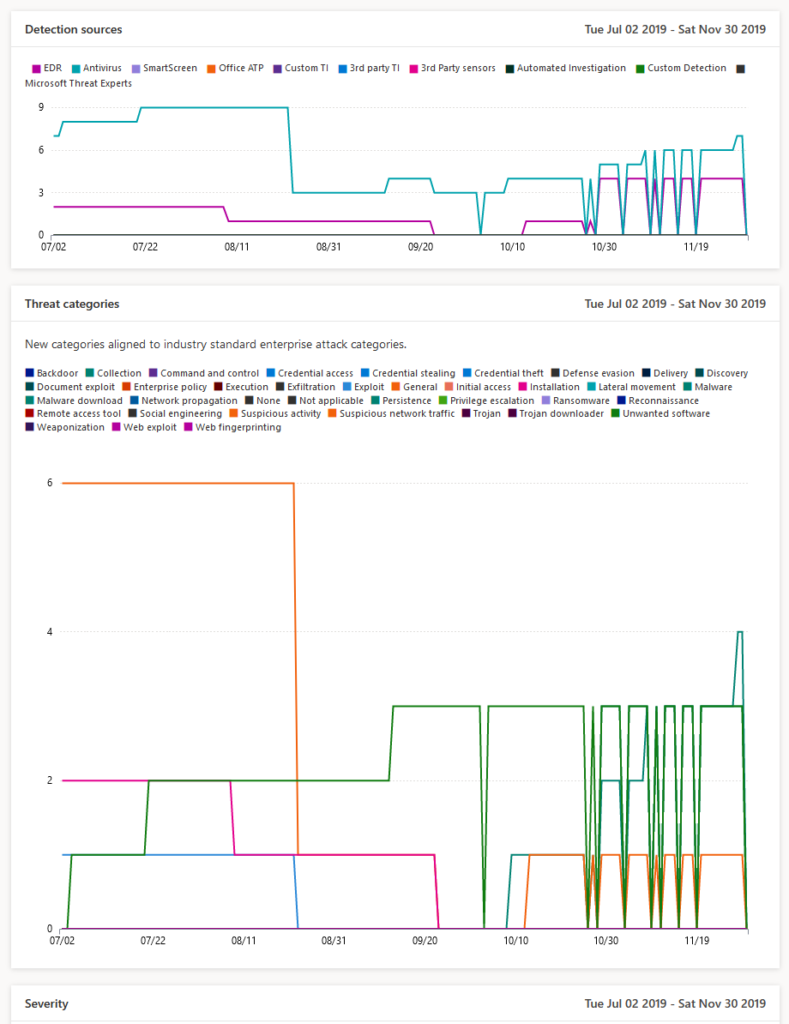
13. Windows 10 Enterprise with modern approach
Windows 10: My personal favorite. I really love customers which did their homework and started using Windows 10 without policies, governance, Intune (for example), management solutions and now they are stuck in the patching & management of these systems. This is wrong!
Microsoft Windows 10: Windows 10 has been released to insiders in 2015. version. 1507 afterwards 1511, 1607, 1703,1709, 1803,1809,1903,1909. Microsoft did understand the pain of shifting from Windows XP to Windows 7, Windows 8 to 8.1 and Windows 10. And now they want you to work on this NEW versions in a different way.
Microsoft’s Windows 10 Enterprise: comes in the flavor of continues improvement. And needs to be implemented in a service-model with automatic updates, roll-outs, deployment, patching, updating, software requests (self-service) and even more!
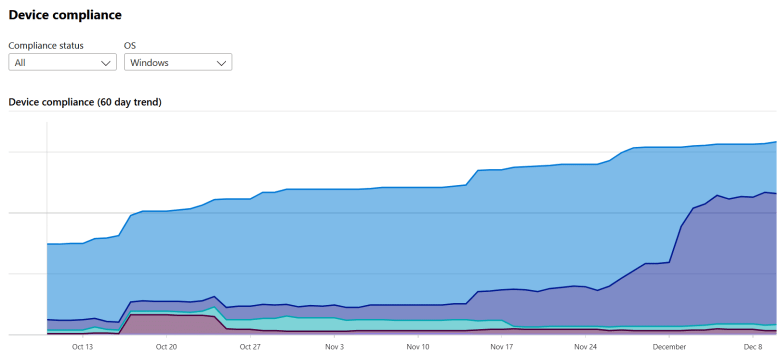
Set compliance policies: Because of deep integrations you will be able to work on the compliance of the devices and grow to a recurrent update-model.
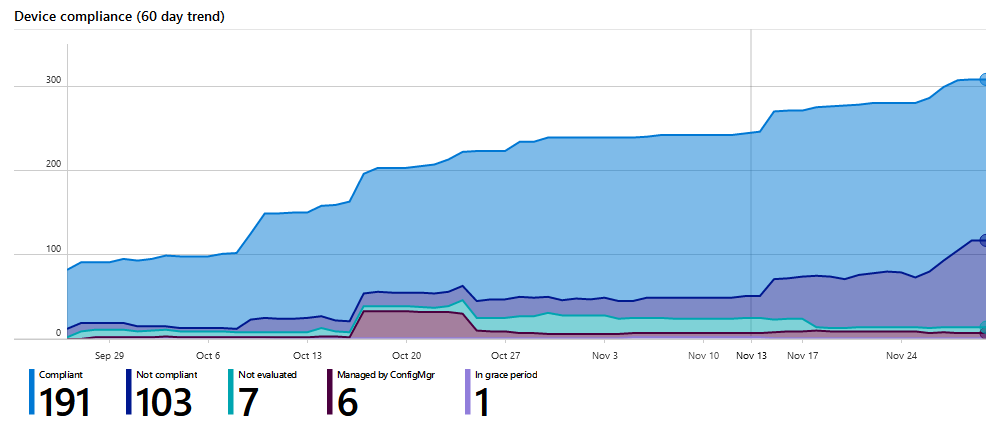
14. Desktop Analytics
Thanks to desktop analytics you will be able to evaluate the changes during updates as software distribution and compatibility issues. You can bring your organization to a next level. In case you were afraid that automation took your job, think again. These things need huge attention!
15. Native PowerBI Integration
Because of the rich Eco-system within Microsoft 365 everything can be measured. This report is default/standard without any manipulation of Power-bi. I know it sounds stupid, but without insights that can grow fast. You have nothing. Features/services are changing every year. Be prepared. Start consolidation and start using standards to built on.
Action Plan
- Create a STRATEGY to bring value for Microsoft 365 E3 or E5. Do you want to: increase agility, empower information workers create intelligence increase mobility short: Drive transformation. AND invest in your SECURITY MATURITY -> than you should start with a STRATEGY. Non of all these things are technical. Even if we think it’s technical. DECIDE.
- PLAN: Everything starts with a plan. PLAN to start a Microsoft Teams pilot, to evaluate, to pick-up the finding. and plan to go further. Most important PLAN to write a ROADMAP which describes the road ahead.
- READINESS CHECK: Are you technically READY to start with a Microsoft Teams Roll-out? Is your company READY to start? Are the people READY to start? Is everyone involved? Are you READY?
- IMPLEMENTATION: This is the easy part. Implement Microsoft Teams. Enable the features, check the boxes. Activate the subscriptions, copy the templates. Start the Pilot. Ask experts to deliver the technical requirements.
- NEW WAY OF WORK: Microsoft Teams as used in this example as ‘new tech’, think about the groups we had in the top of the article. millennial’s, Gen Z, Gen X, Baby boomers. Do you think you should make some scenario’s? training and standard adoption programs to help them work as they never did before? YES!
- TRANSFORM(ATION): Real transformation is successful when you KNOW/MEASURE it went well. Wen you see the activation/usage ratio in numbers. When you know the people are confident and happy to use new technology. When nobody is complaining and the organization has grown to a higher level of collaboration. And even when it fails or needs more improvements start over with this S-P-R-I-N-T.
Thank you for reading!
Jasper