Modern Desktop implementation – Behind the scenes
Introduction & Vision
At Synergics we truly believe the mission of Microsoft to empower every person and every organization on the planet to achieve more. Every great implemented project start with a vision and with goals/milestones.
In the first project we delivered workshops to understand the transformation needs of the organization. we identified these digital outcomes below. (the description is basic, I know. But it’s another side-traject of this implementation)
- Empower information workers and firstline workers so they can collaborate and communicate.
- Simplified communication – Communicate through the full organization.
- Increase agility for the IT-Organization – adaptability.
- Futureproof design – Technical design, cloud first strategy.
You can read the reference-case in NL or FR! Microsoft Surface with Windows Autopilot ensure efficiency gains and easier IT management for the city of Lokeren. Reference Case.
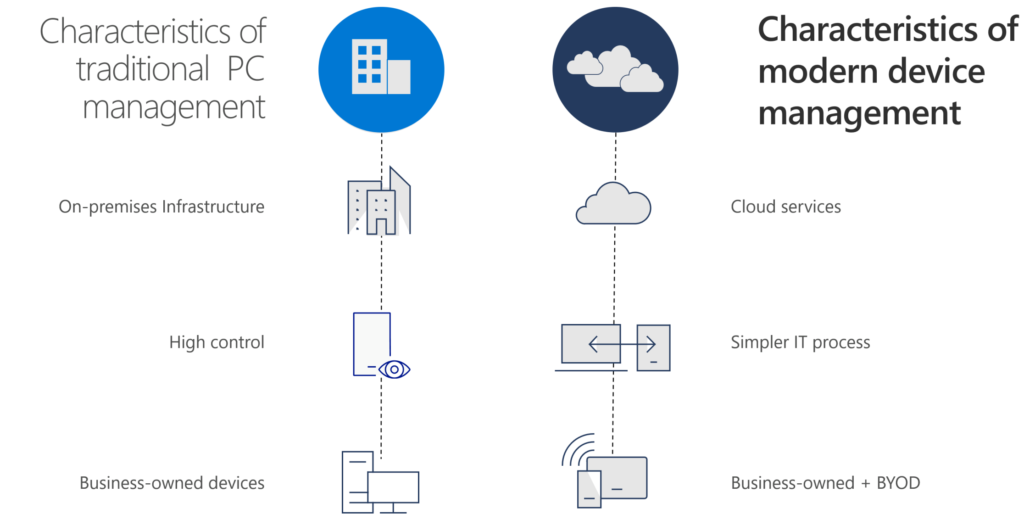
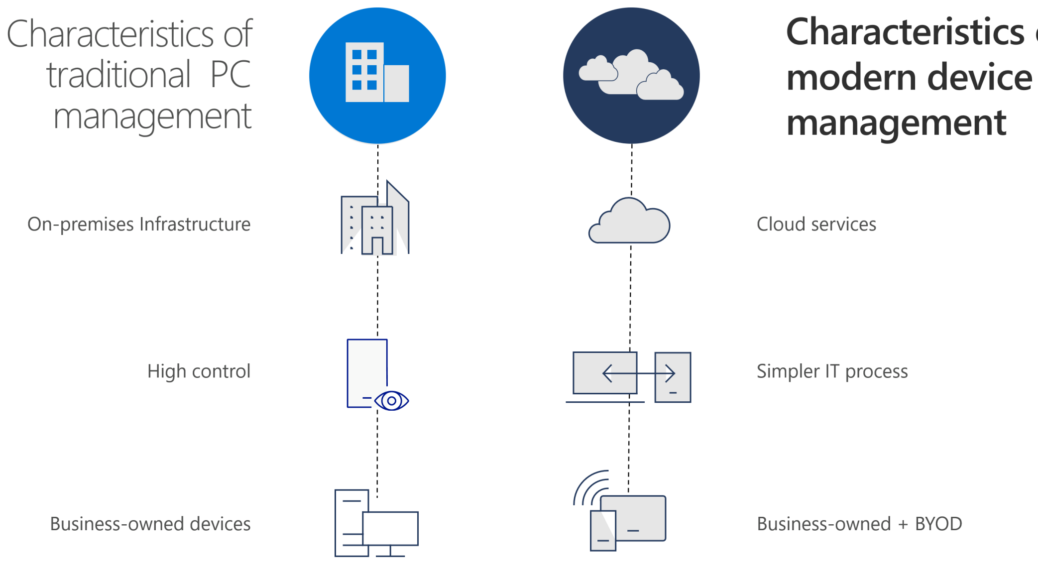
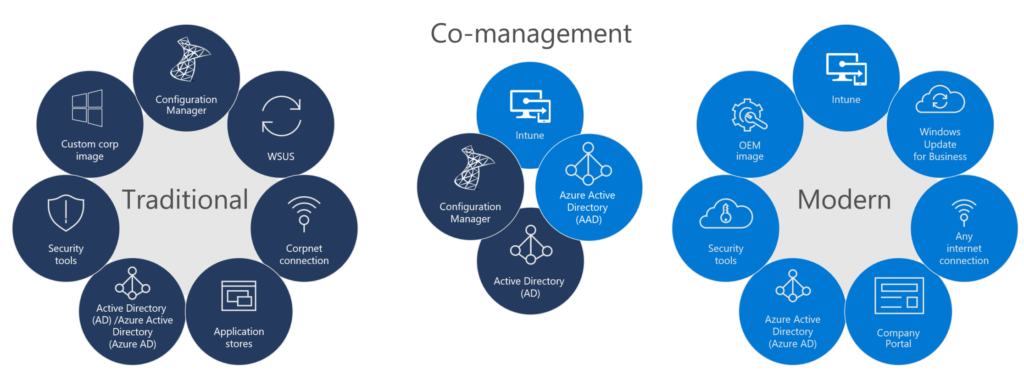
Evolution to modern management – 100% CLOUD!
- Less complexity
- built-in automation
- brand-new configuration & policies
- higher security standards
- self-service possibilities
- 100% CLOUD!
To achieve more it’s important to give control to the people (empower), update your platform, easier roll-out’s of new devices etc.. (Scenario on the right, 100%…)
New device setup experience with Autopilot
Imaging/cloning/etc of devices is taking a lot of crucial time – compared to Autopilot. This isn’t the easiest enabler because there are policies, GPO’s, in place. With Autopilot we deliver the roll-out of the Windows 10 Devices and sync back the Device-Object so on-premise resources can still be accessed in transition for future plans.
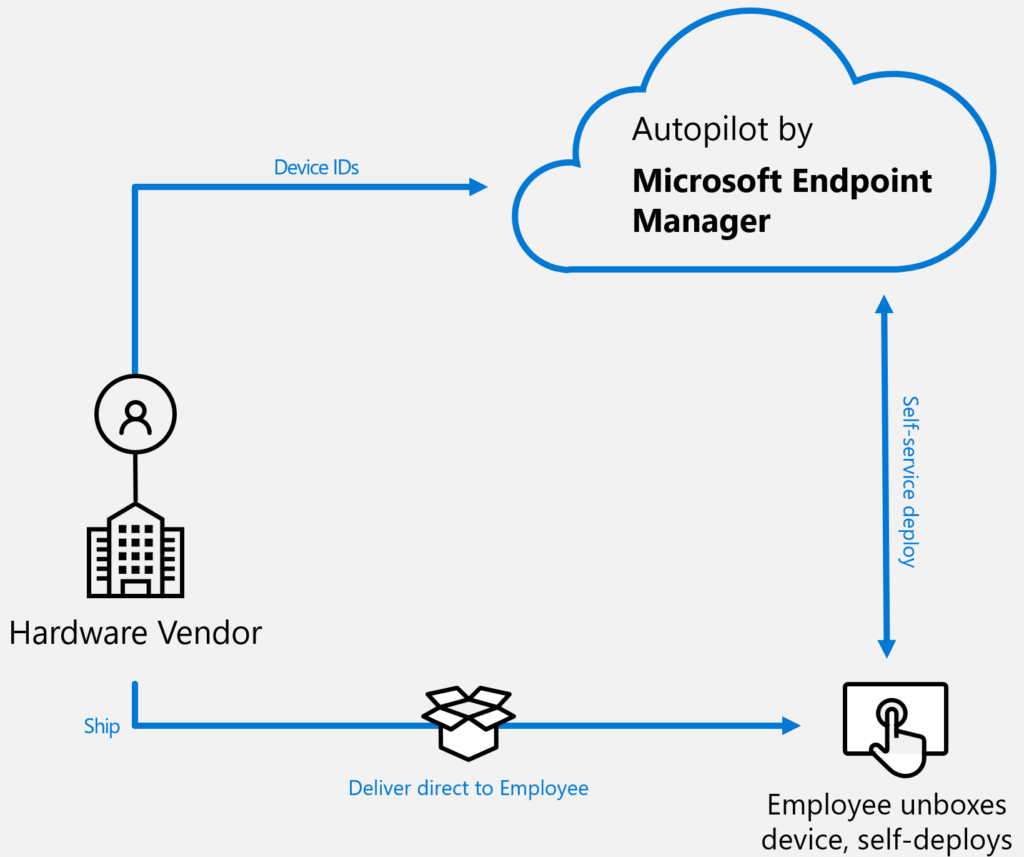
- – Old GPO’s can stay for some time.
- – New possibilities of modern management becomes active.

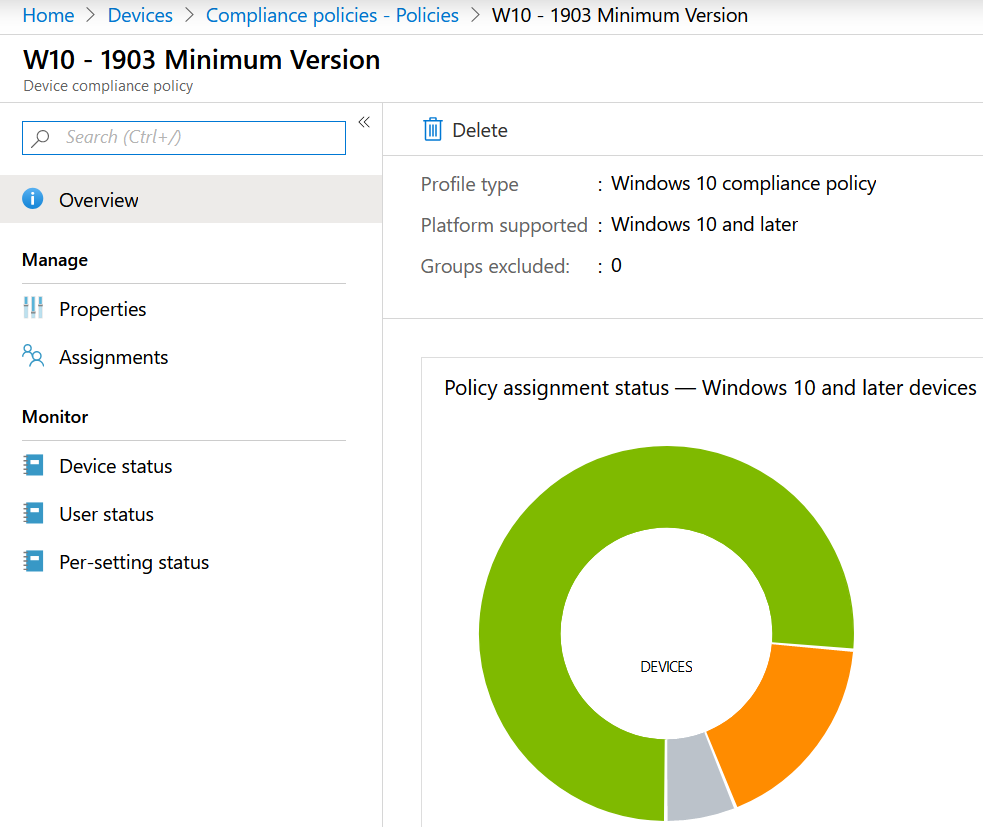
Microsoft Windows update in waves & delivery optimization
It looks like a easy job but most of the time it’s a non-controlled mechanisms.
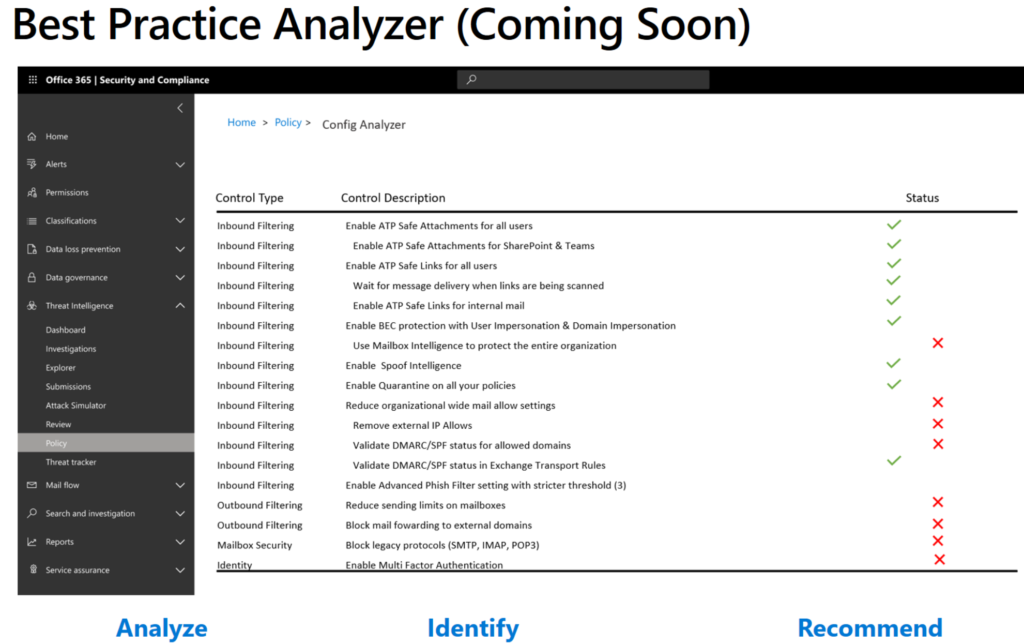
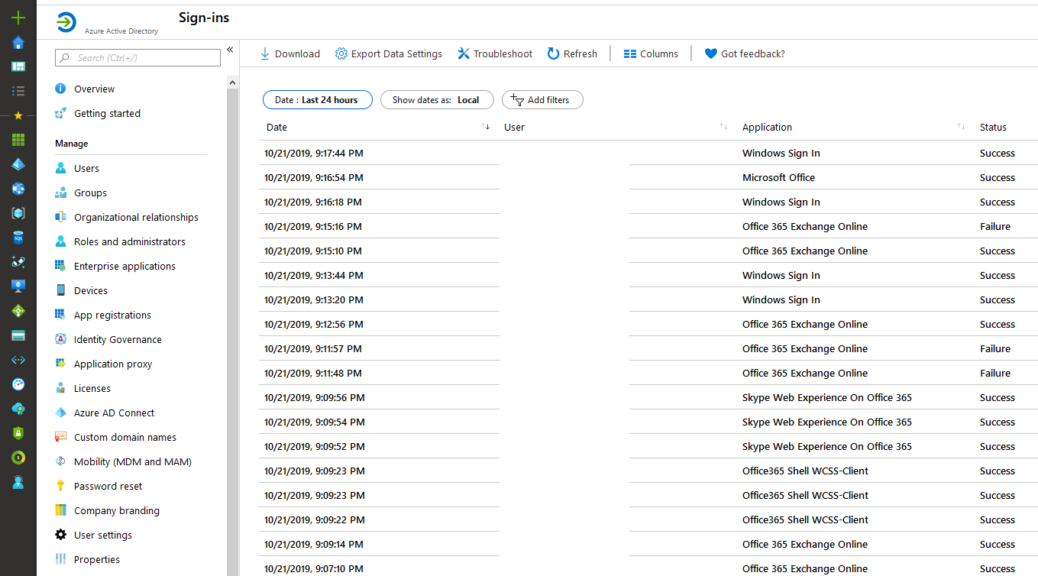
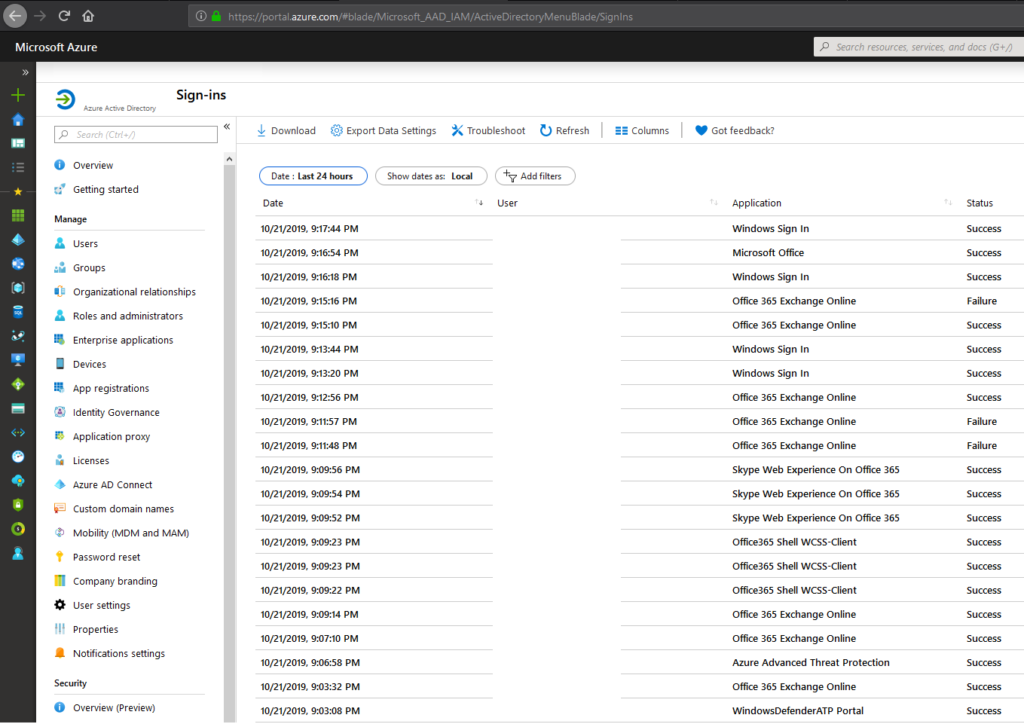
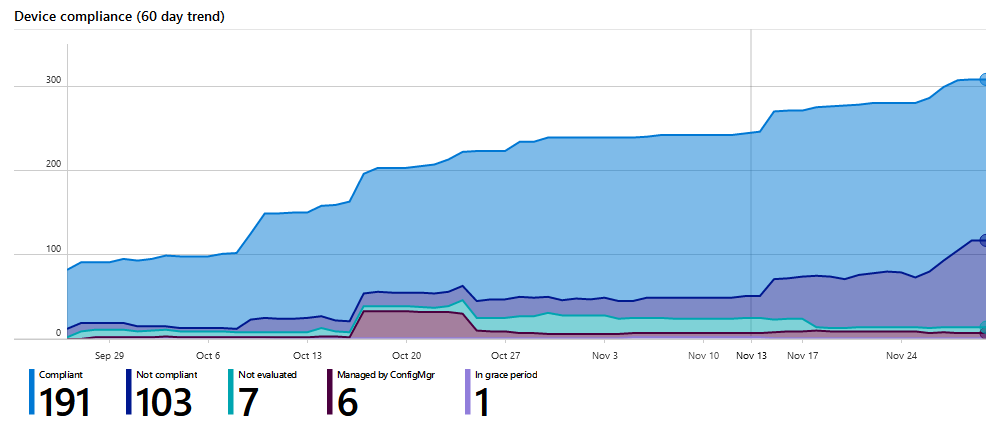
Windows 10 started in 2015 with builds as: 1511, 1607, 1703,1709, 1803,1809,1903,1909. As you see can in the screenshot, now we are transforming to 1903! and 1909 starting soon.
- Delivery optimization
- Updates in collections – pilot/key users
- Peer-to-peer distribution
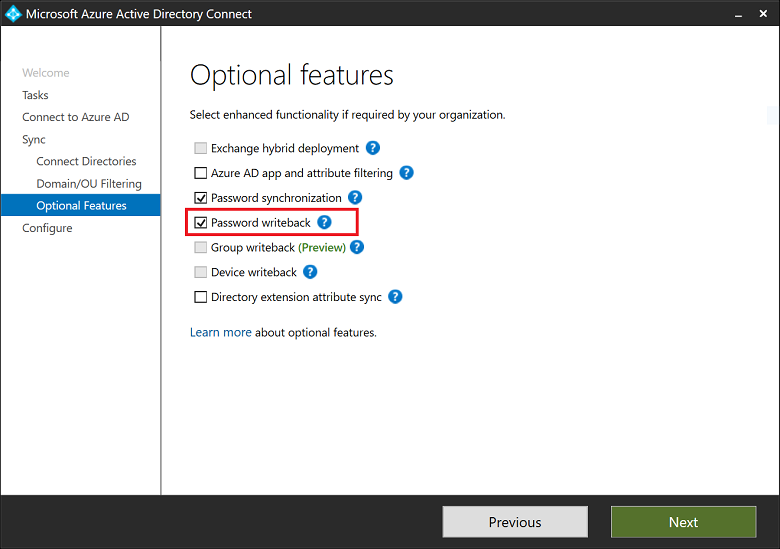
Hybrid Identity – and password write-back
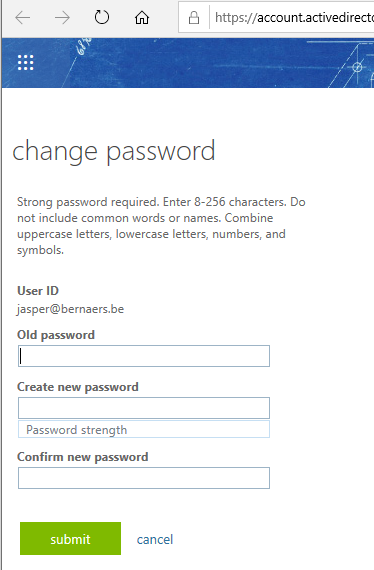
I was hoping to write cloud-identity but we still live in a world of on-premise infrastructure waiting to move to the cloud. For now we are creating and maintaining identities on-premise. We enable password-write-back so users are able to change their password.
- No Servicedesk calls anymore for password resets
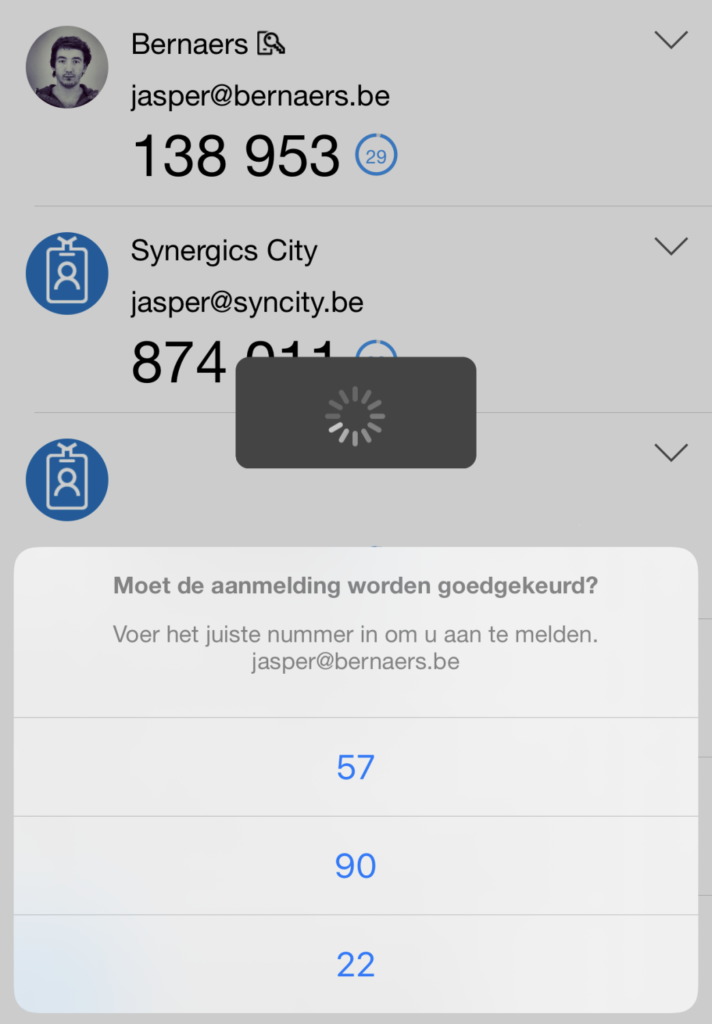
- Multi Factor Implementation, check!
- Self-Service Password Writeback!
- Hybrid-Identity
Intune mobile device management authority
Office 365 ProPlus distribution based on dynamic collections
It sounds very easy but I’ve seen a lot of customers fighting with licenses and automated processes.
- When a user is in a M365 E3 dynamic collection because of the parameters Office ProPlus is automatically distributed.
- When a user has no ProPlus acces, like a O365 F1 user, office 365 ProPlus will be removed.
Onedrive Known Folder Move (KFM)
There are two primary advantages of moving or redirecting Windows known folders (Desktop, Documents, Pictures, Screenshots, and Camera Roll) to OneDrive for Business for the users in your domain:
- Your users can continue using the folders they’re familiar with. They don’t have to change their daily work habits to save files to OneDrive.
- Saving files to OneDrive backs up your users’ data in the cloud and gives them access to their files from any device.
- This has value, value, value. Users can find their documents on their phones because of the automated move. When there workstations crashes, the data is still there..
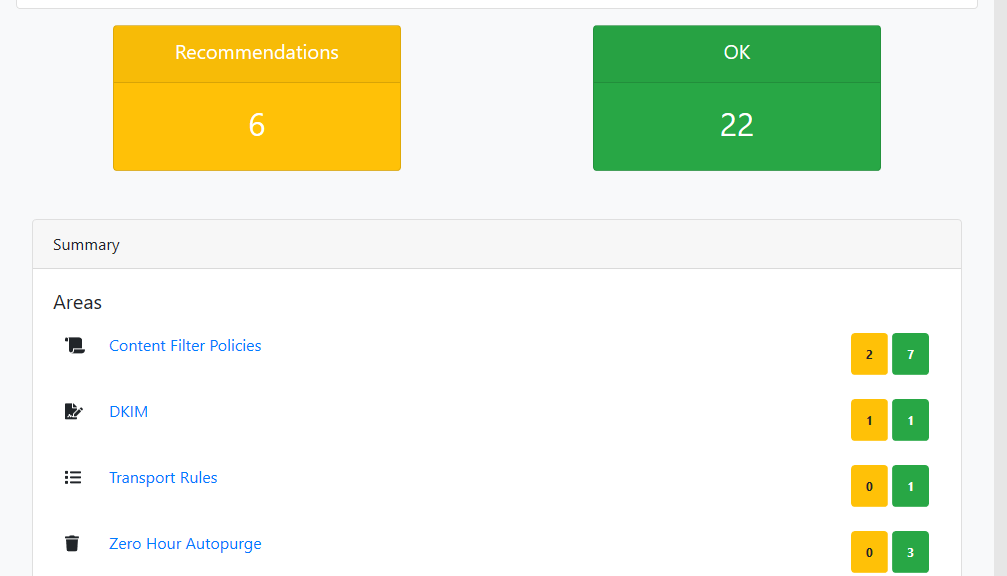
Microsoft Defender Advanced threat protection
All devices are fully managed under the greatest MDATP. (also see the quadrant)
- Multi-layered protection: Microsoft Defender ATP provides multi-layered protection (built into the endpoint and cloud-powered) from file-based malware, malicious scripts, memory-based attacks, and other advanced threats
- Threat Analytics: Contextual threat reports provide SecOps with near real-time visibility on how threats impact their organizations
- A new approach to Threat and Vulnerability Management: Real-time discovery, prioritization based-on business context and dynamic threat landscape, and built-in remediation process speed up mitigation of vulnerabilities and misconfiguration
- Built-in, cloud-powered protections: Real-time threat detection and protection with built-in advanced capabilities protect against broad-scale and targeted attacks like phishing and malware campaigns
- Automated security, SecureScore and +10 more features!
Enterprise state roaming (ESR)
With Windows 10, Azure AD users gain the ability to securely synchronize their user settings and application settings data to the cloud. Enterprise State Roaming provides users with a unified experience across their Windows devices and reduces the time needed for configuring a new device. Enterprise State Roaming operates similar to the standard consumer settings sync that was first introduced in Windows 8. Additionally, Enterprise State Roaming offers:
- Separation of corporate and consumer data – Organizations are in control of their data, and there is no mixing of corporate data in a consumer cloud account or consumer data in an enterprise cloud account.
- Enhanced security – Data is automatically encrypted before leaving the user’s Windows 10 device by using Azure Rights Management (Azure RMS), and data stays encrypted at rest in the cloud. All content stays encrypted at rest in the cloud, except for the namespaces, like settings names and Windows app names.
- Better management and monitoring – Provides control and visibility over who syncs settings in your organization and on which devices through the Azure AD portal integration.
- Even next to KFM! Even more great for data loss etc..
Future achievements..
- Everything starts with the value of Microsoft 365 E3 of E5.
- Analytics and data. My-analytics, Workplace Analytics?
- Security Operations – Advanced hunting?
- Proactive services – thousand scenario’s possible..
- Automation in processes with Power Automate?
- Deep integration with third-party applications?
- …