Modern Workplace security: 5 steps to use Microsoft Teams in a safe way
In this blog I will go through 5 basic security improvement for organization that are shifting to Microsoft Teams. Also read my previous article: The Value Of Microsoft 365 E3 and E5.
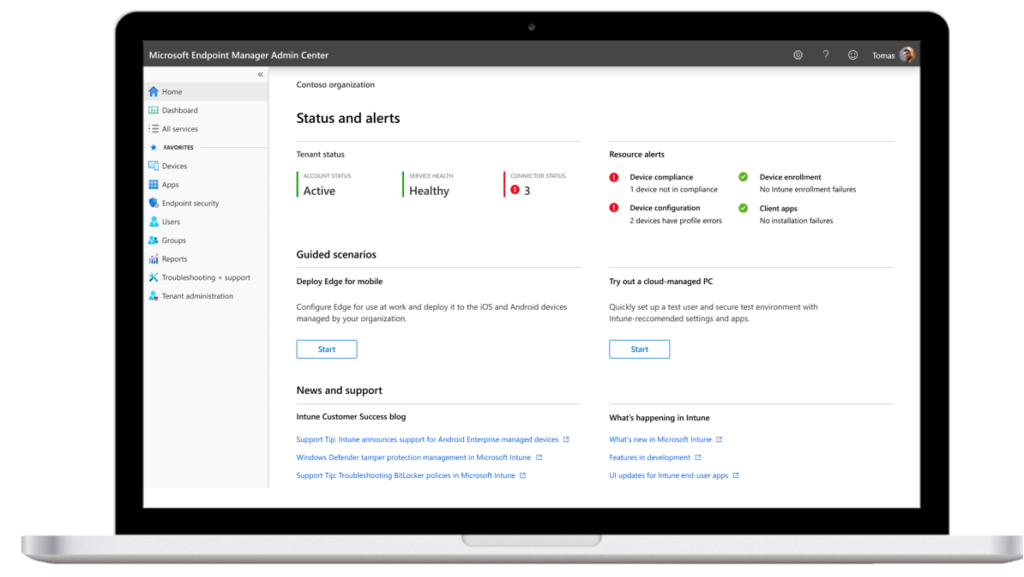
Security improvements are embedded in Teams, it just needs activation
I’ve met a lot of organizations over the last months implementing Microsoft Teams, and I really love to see the fast-deployments, the big-activation, simple communication, dedicated onboarding.
- Did you know that Microsoft Teams is not an addition to Office 365, but an integration of multiple services?
- Did you know you can integrate the product better in your current workplace than ‘we’ think?
- And thousand other possibilities – now that’s the problem, right? We do not really knew, before..
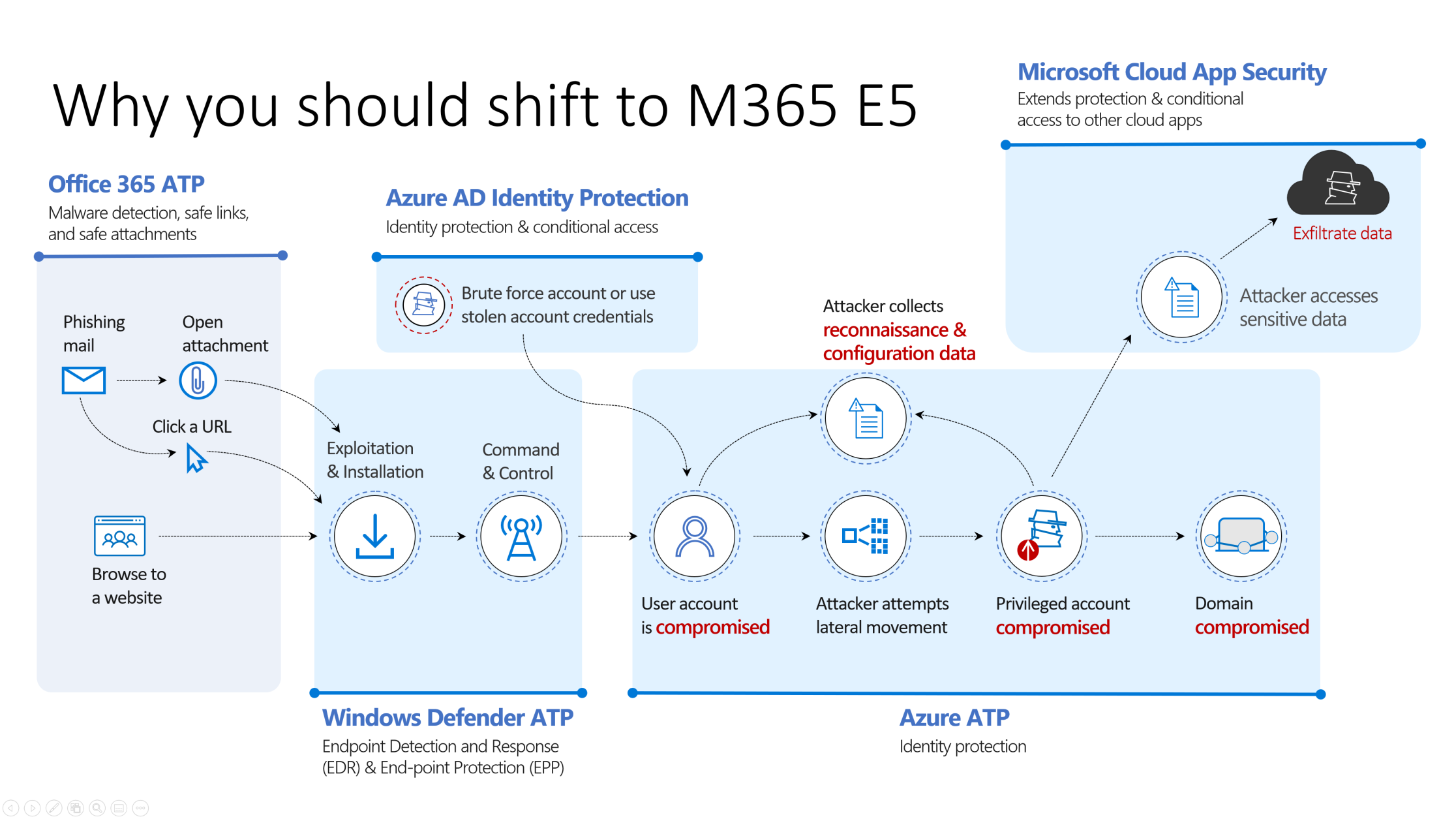
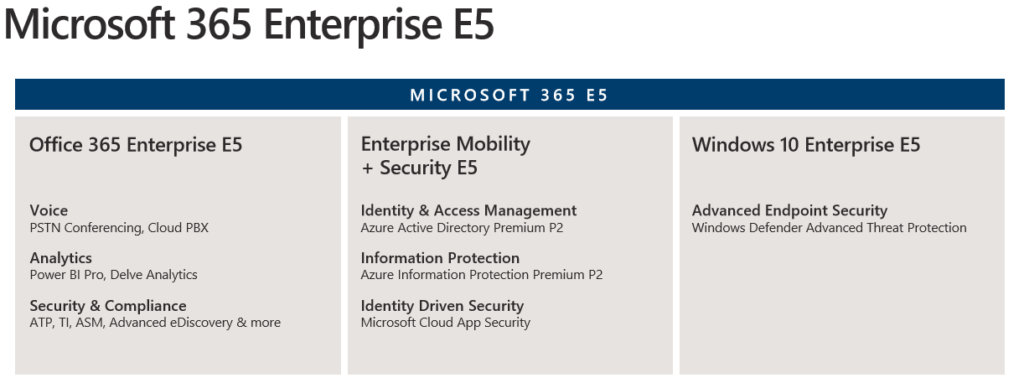
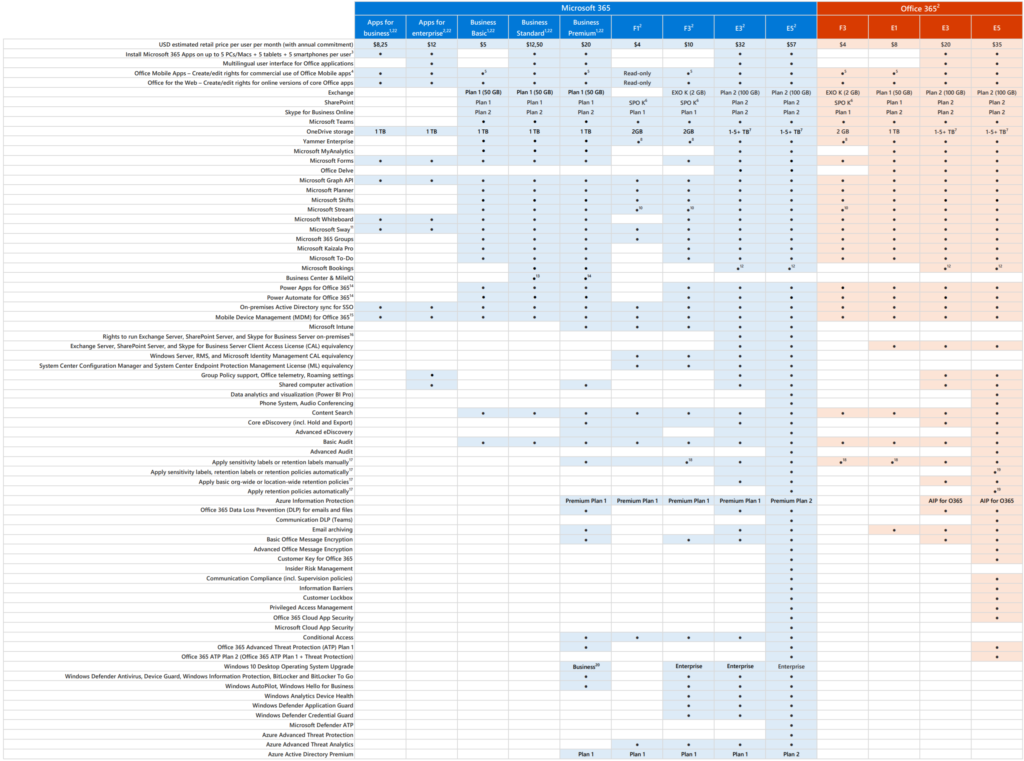
- I know I’ve used Microsoft 365 E5 licenses. You can figure something out without CASB and with Azure Premium P1 + EndPoint Manager.
Introduction: Microsoft Teams Architecture
Did you know that Microsoft Teams is part of Office 365 or Microsoft 365 and is using: Azure AD, OneDrive, SharePoint, Exchange Online, SharePoint, Yammer, Stream, etc all out of the box. I mean, I suppose your organization will use deep integration when shifting to Microsoft Teams. Let’s dig into solutions now!

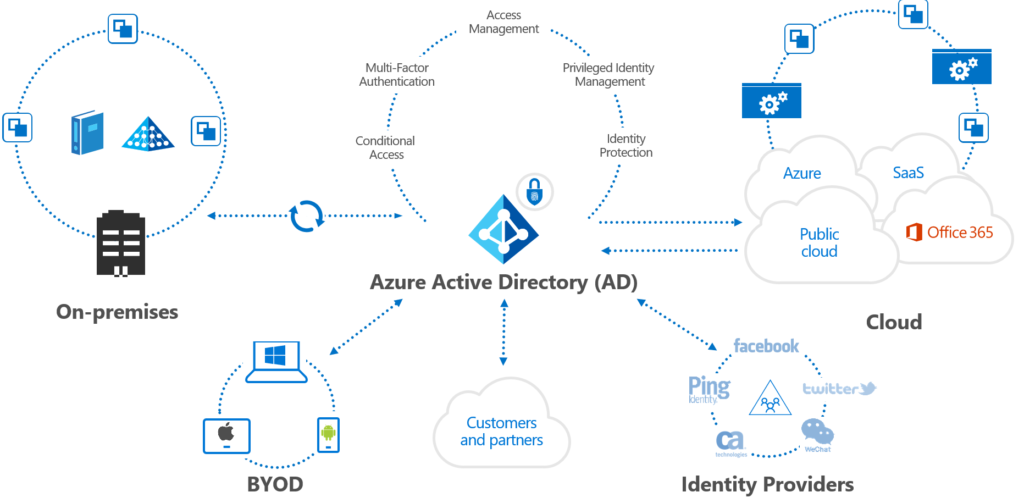
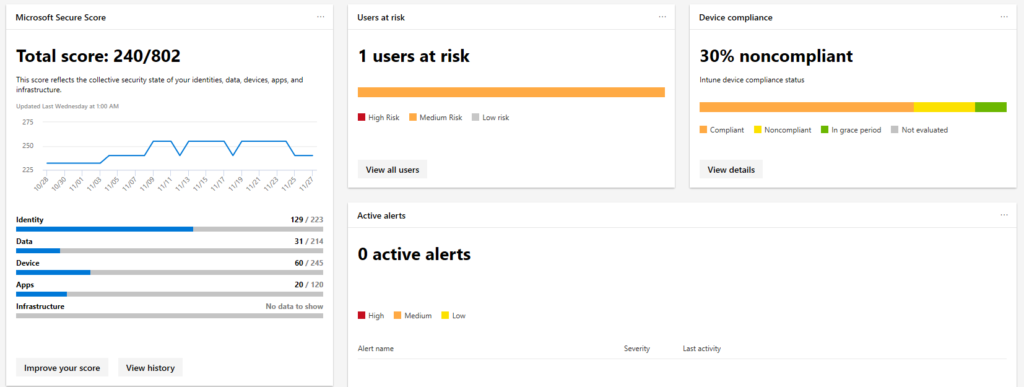
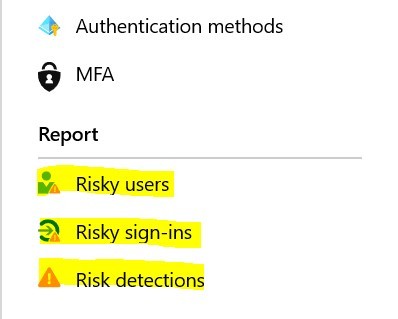
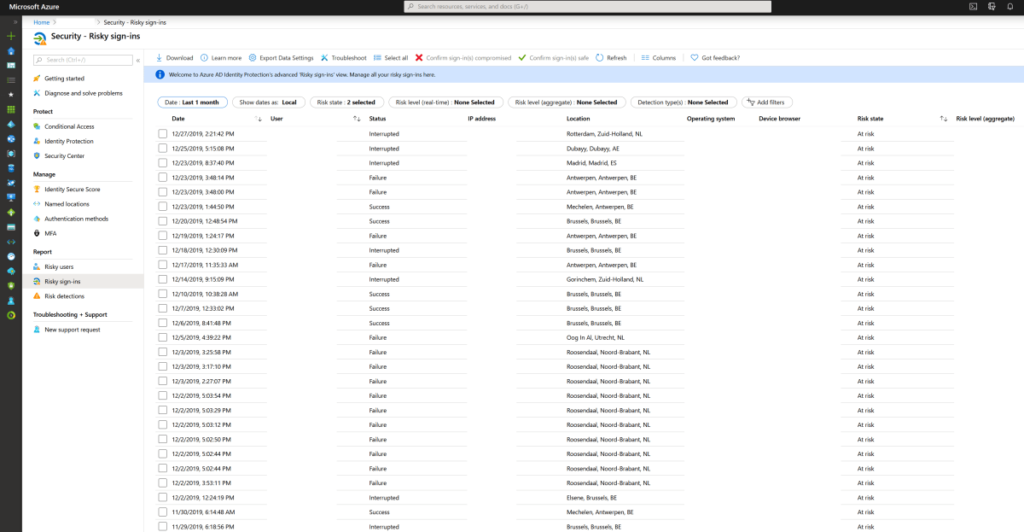
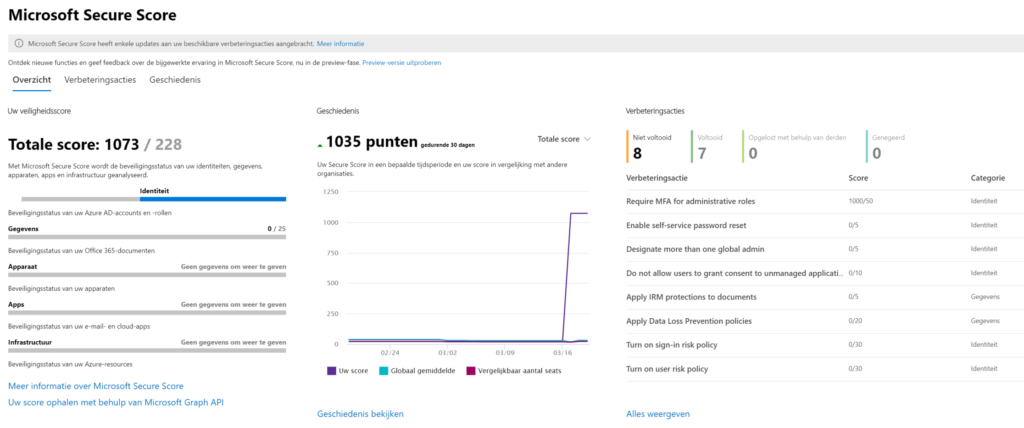
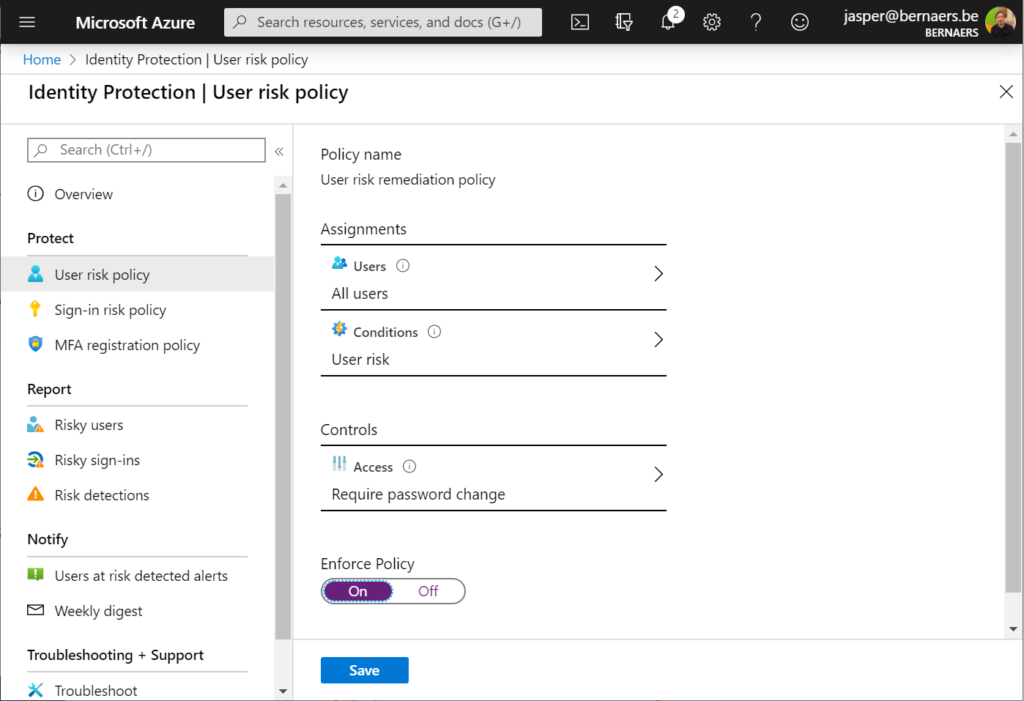
1. Identity Protection: MFA + Azure AD Conditional Access Policies + Risk Policy
The first step is to have a security-identity. Everything comes to Identity security and authentication – access management in general.
- It’s still a best practice to activate Multi-Factor Authentication. I’ve written a lot about this in my previous article.
- Activate Conditional Access to not get craziness of pop-ups and deliver a productive workplace.
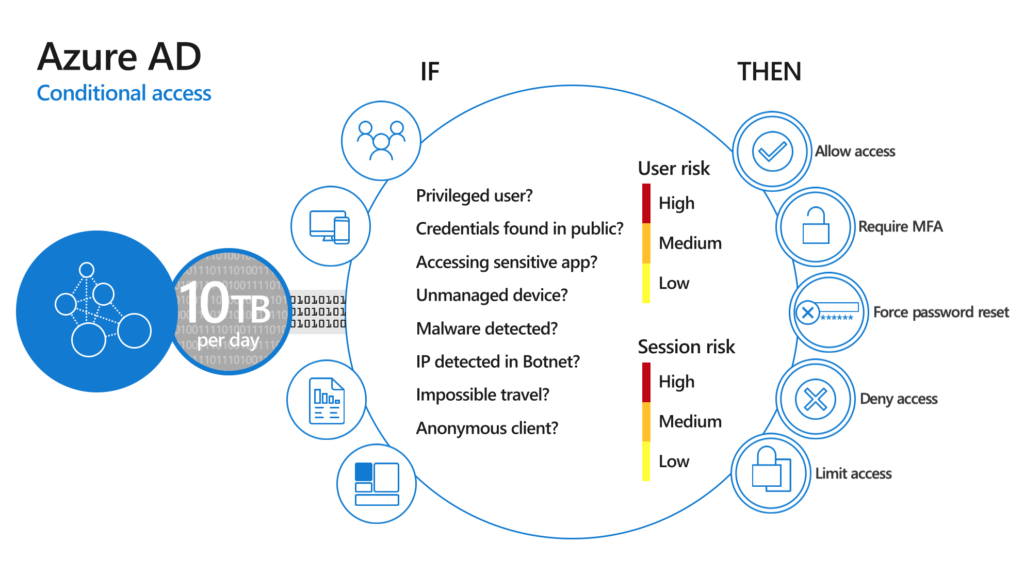
- Force a password change when assuming breach, risk-policies to be sure you can harbor save identities.
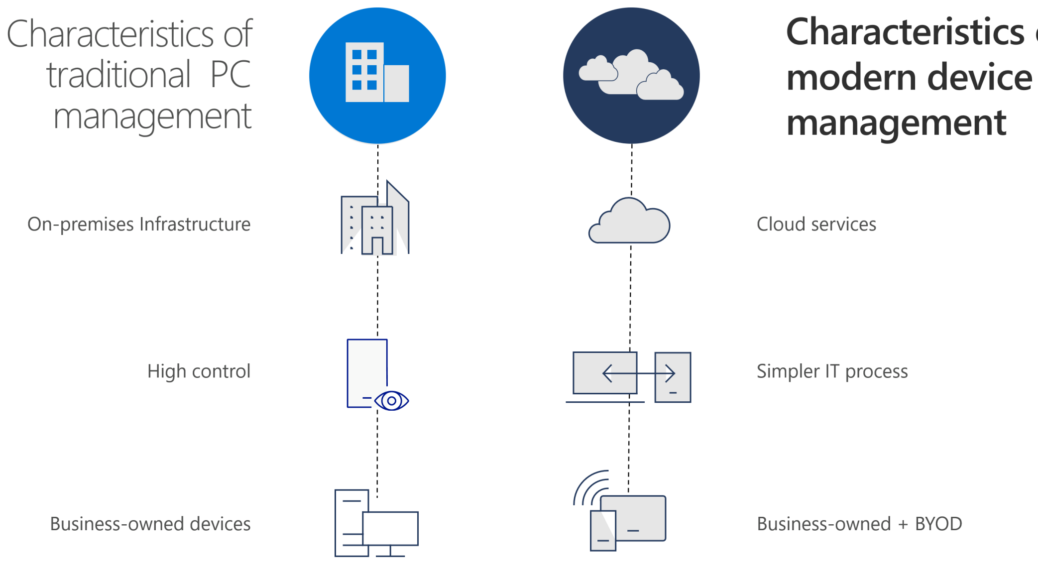
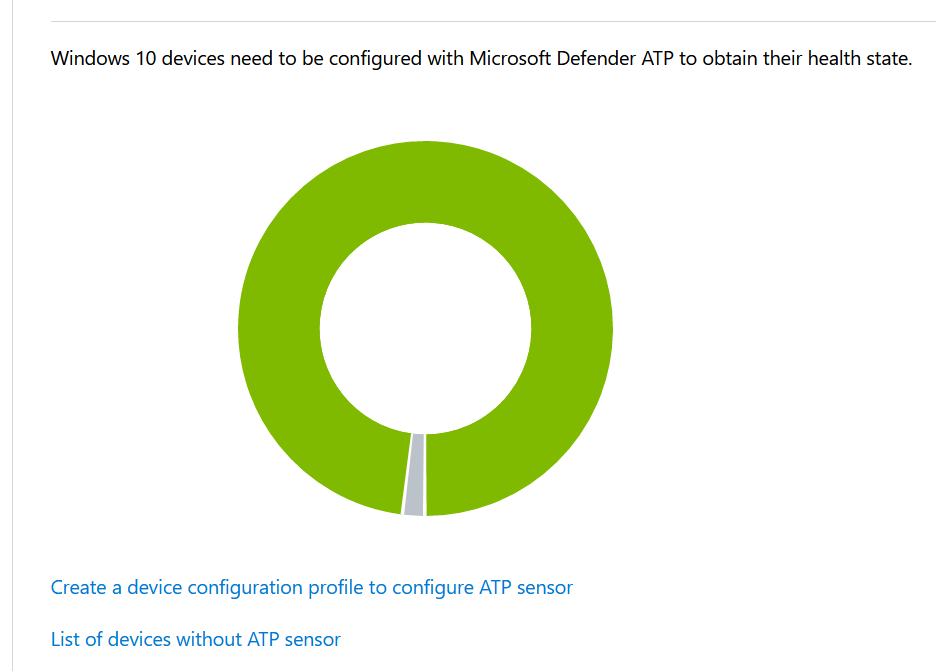
2. Registration for Windows 10: Device Onboarding
Make your Windows 10 devices known in the organization. So you have them in control, and you can do smart things with knowing.
Register or enroll your devices into Azure AD to provide an identity-token to the device. This identity is used to authenticate the device when a user signs in and apply conditional access rules that require domain-joined or compliant PCs.
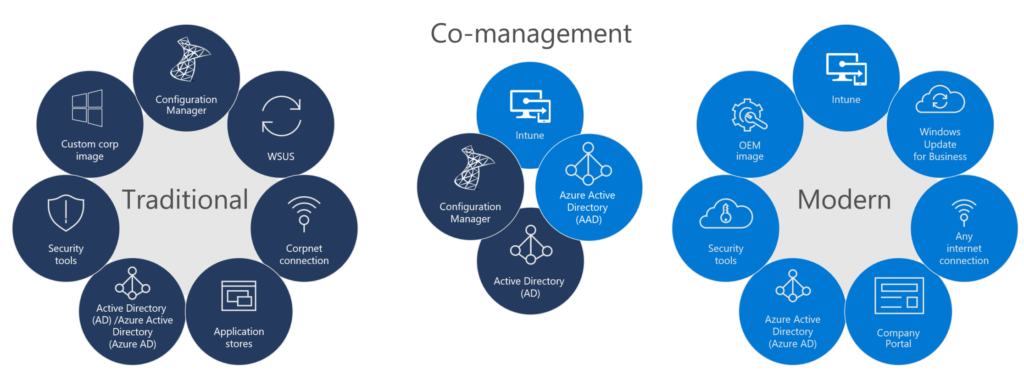
- Hybrid Azure AD Join: Enables devices in Active Directory to register in Azure AD For Access Management.
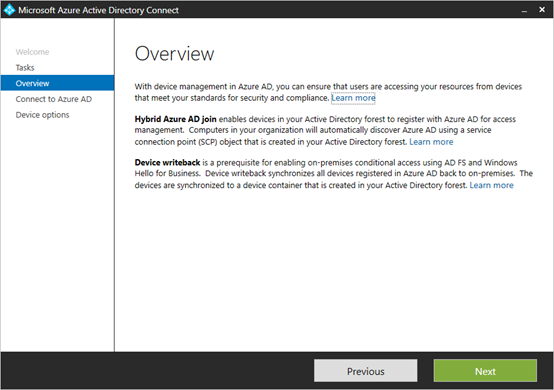
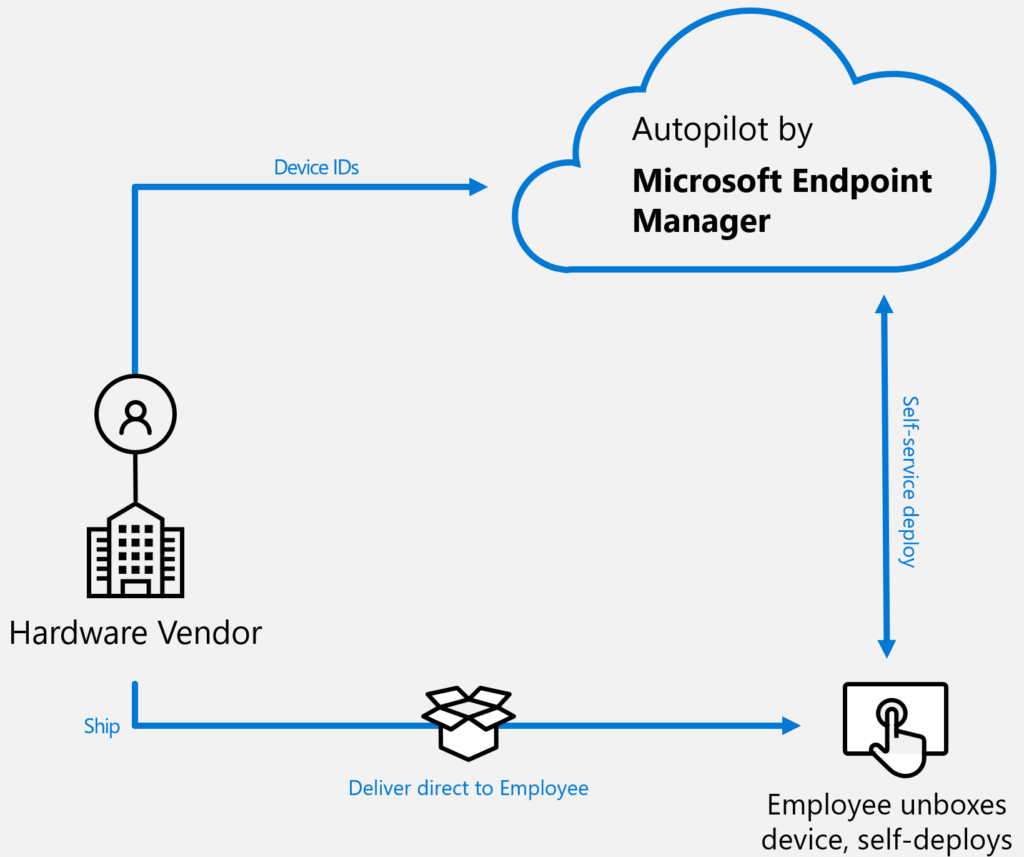
- Go through Autopilot and let new devices join in Cloud-Only modus. With an Hybrid Identity. I’m not fan of doing registration only. It has value, but you can give than only Access Management. I’ve seen companies being able to go direct with Autopilot and shift to only Cloud Modern Management and have the devices in Azure AD only. It’s not a requirement Cloud or Hybrid. But it can help with straight-forward implementations.
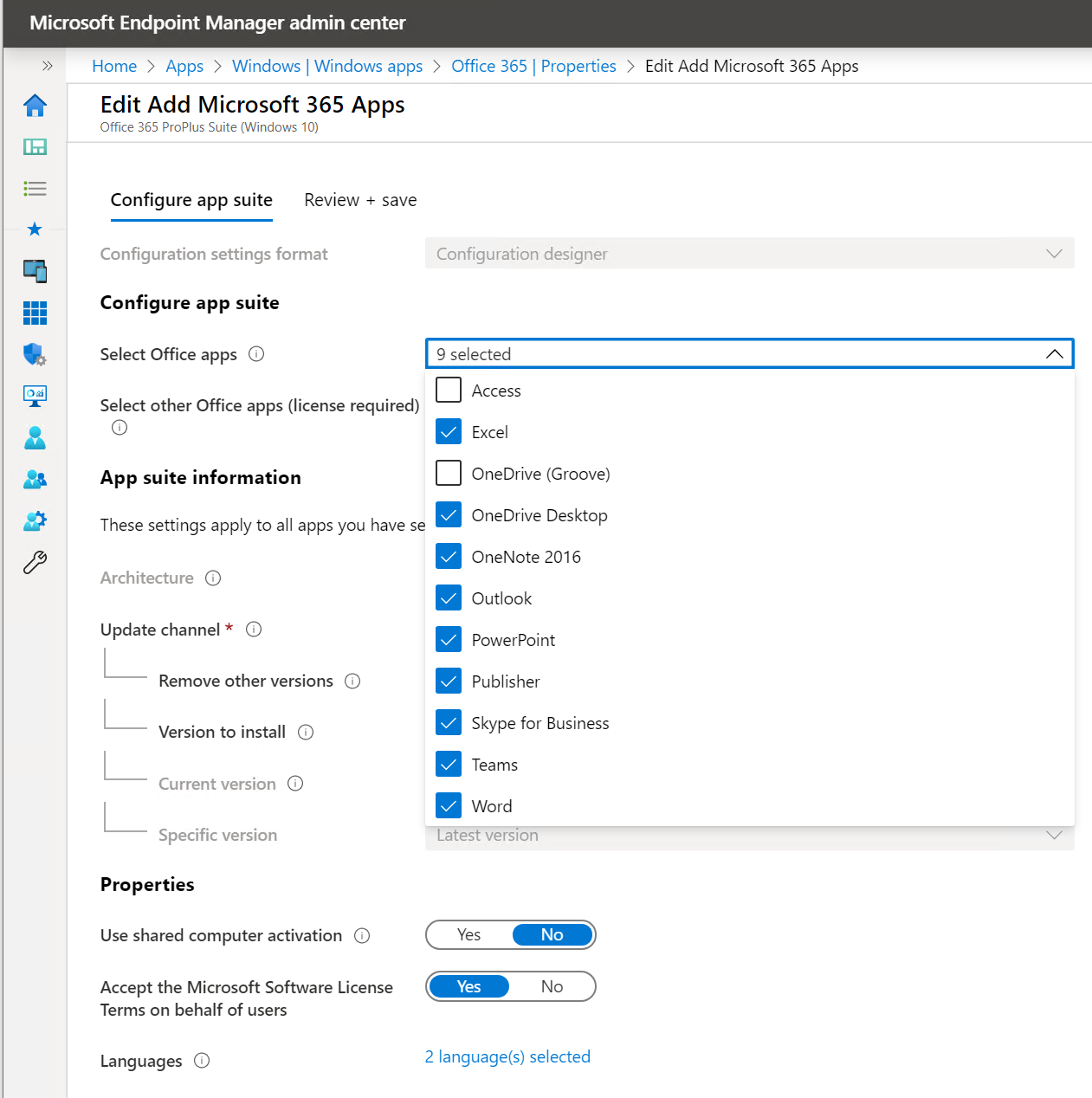
- Later you can do EndPoint Manager. Deploy Microsoft Teams, and the Office 365 suite to all endpoints.
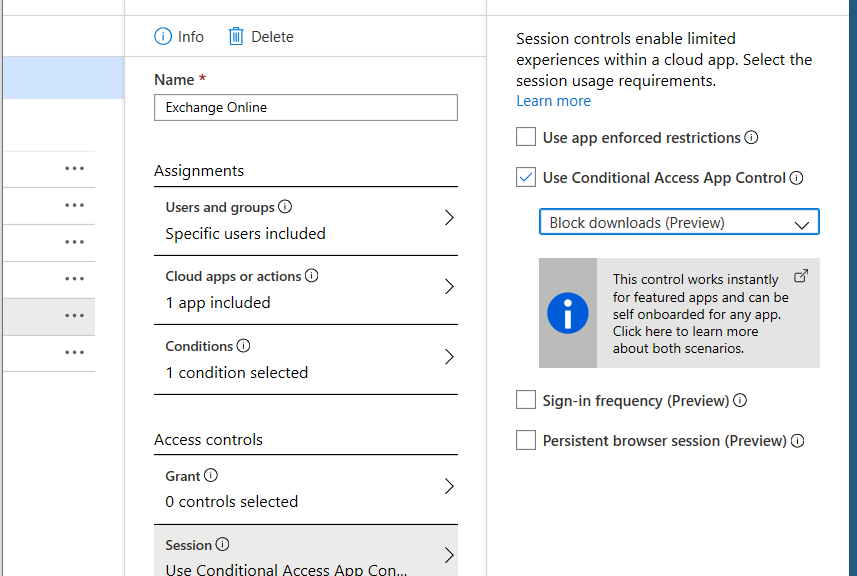
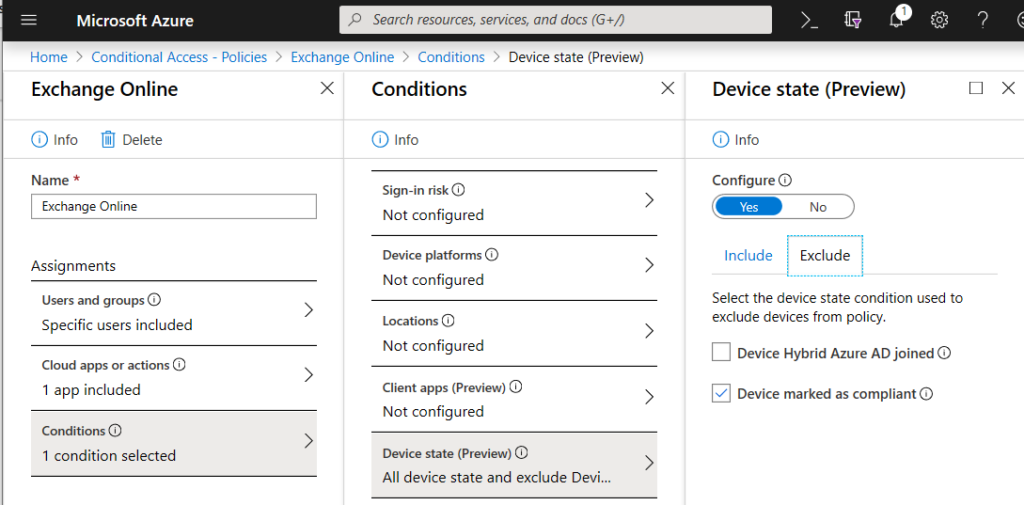
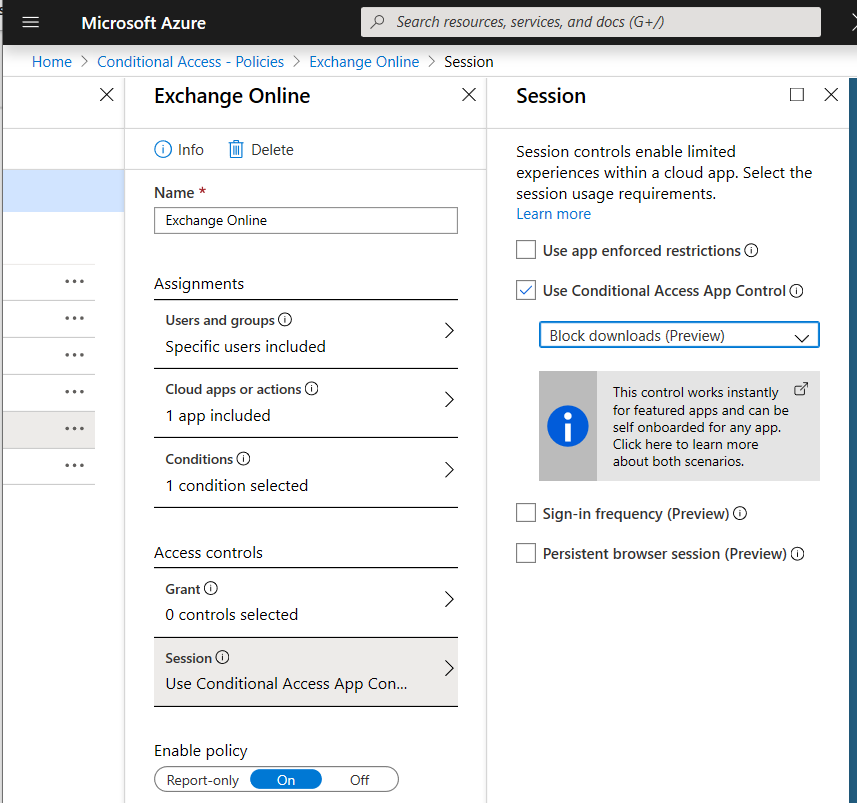
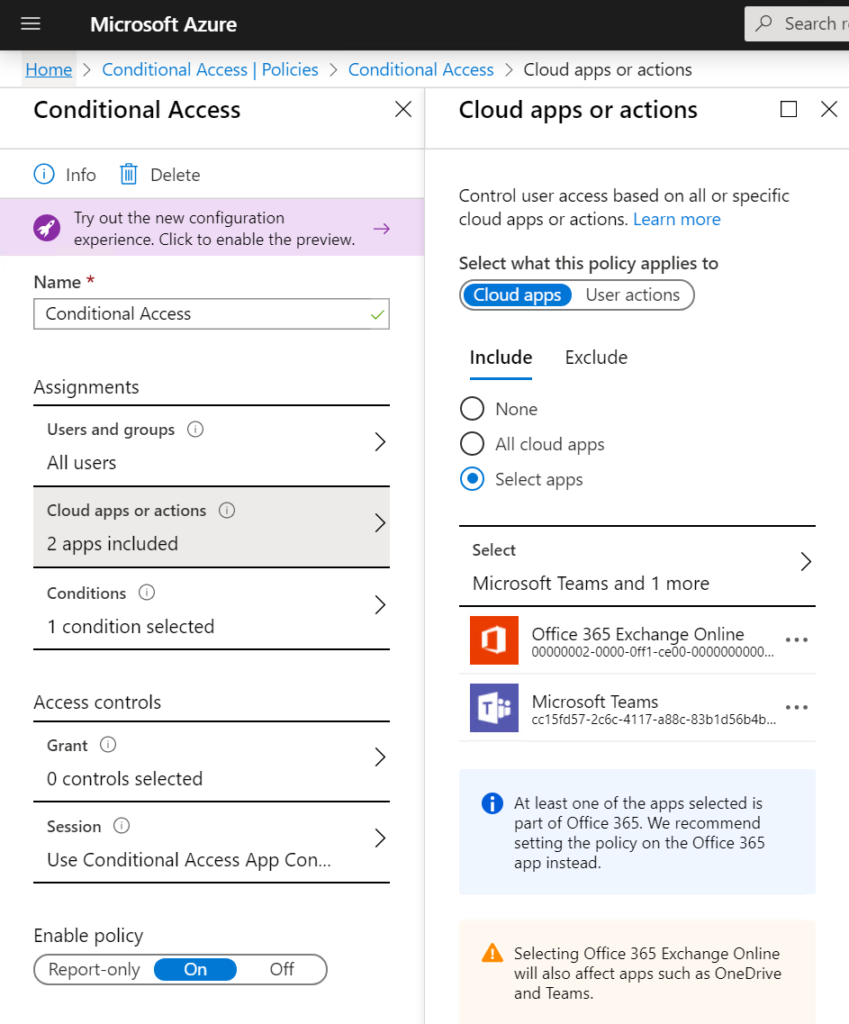
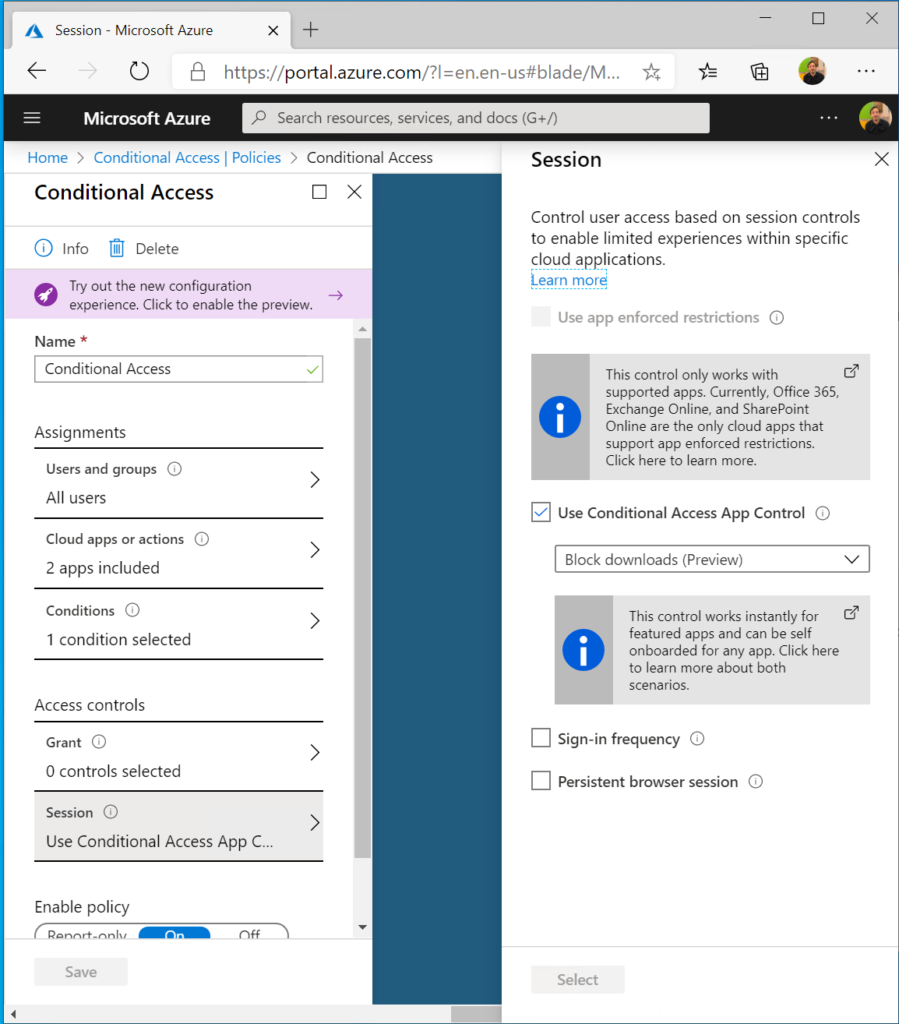
3. Block downloading of document on non-trusted devices
If your device is not trusted. Accessing corporates data should be possibly (sometimes not, I know) but different than a real trusted device.
- Set simple and transparent conditional access policies. Don’t make it to complex.
- You could use this App Control (preview) to easily block downloading of ANY Office 365 document on a ‘non-trusted’, ‘non-compliant’ device.
- Keep in mind, when using this. If you only select Exchange, it still impacts Teams, SharePoint as stated in the tip in the first screenshot.
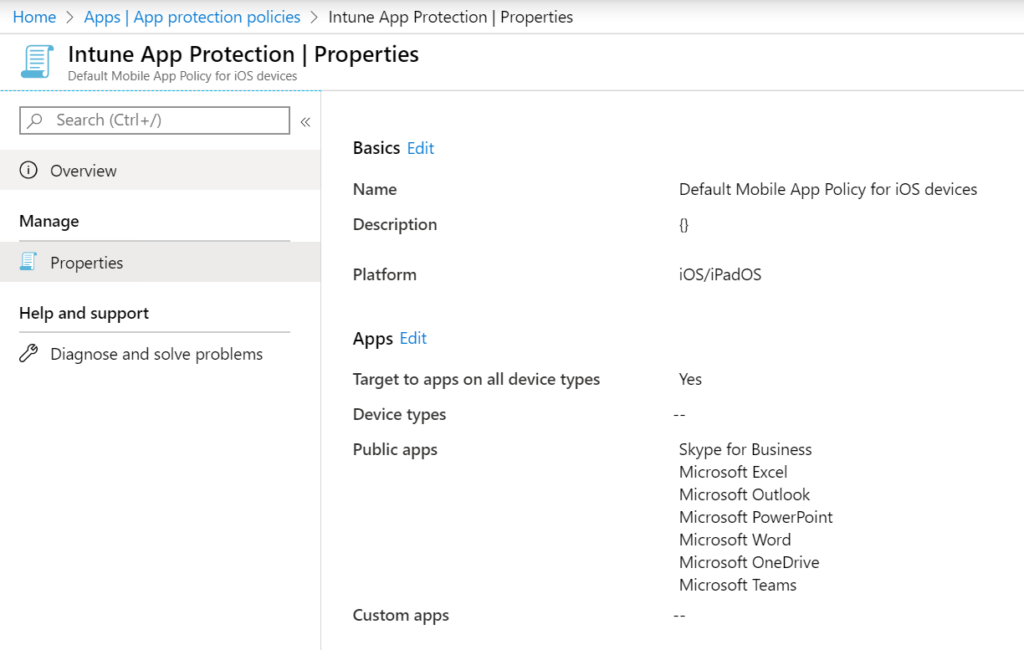
4. Intune App Protection policies for Mobile Devices
You’ve covered your identity, your Windows 10 devices. You’ve covered your non-trusted devices and now your mobile devices.
- I like to get feedback on this one. I’ve done App Protection policies on multiple customers without changing any definition of the standard policy you can create from: https://admin.microsoft.com – there is nothing wrong with standards. Better a policy activated than no policies.
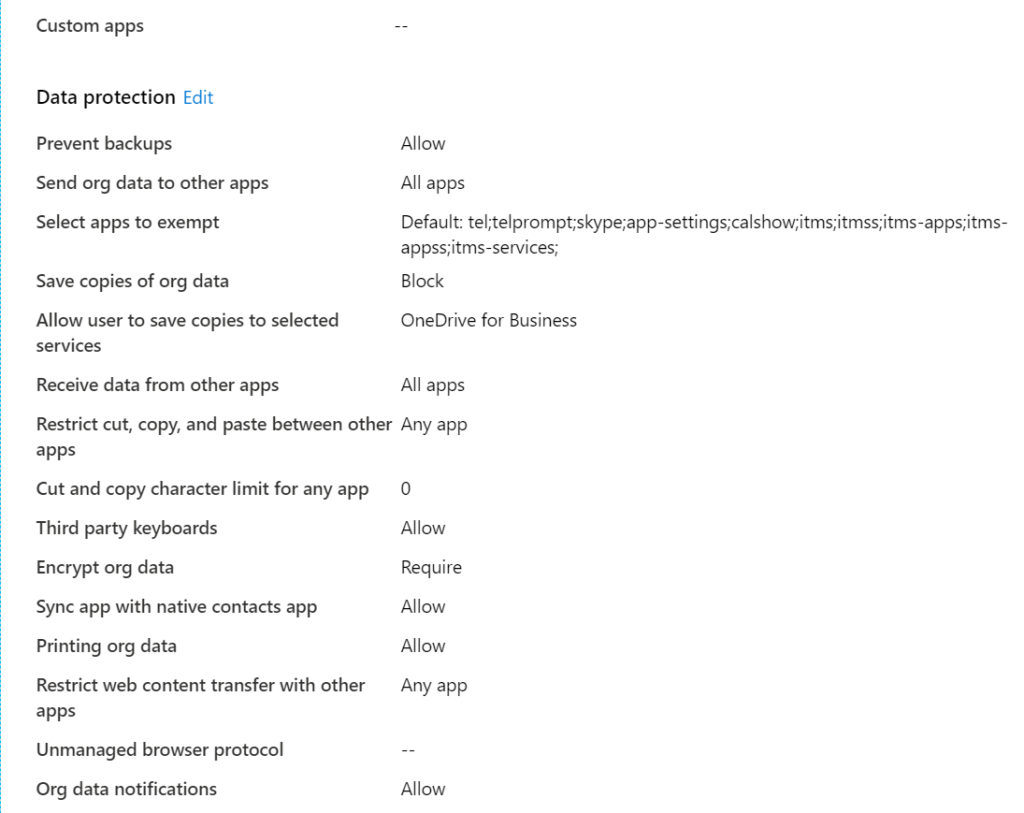
Or you can use the App Protection Policy Data Protection Framework. It provides 3 levels op App data protection configuration. (github)
- Level 1 enterprise basic data protection – Microsoft recommends this configuration as the minimum data protection configuration for an enterprise device.
- Level 2 enterprise enhanced data protection – Microsoft recommends this configuration for devices where users access sensitive or confidential information. This configuration is applicable to most mobile users accessing work or school data. Some of the controls may impact user experience.
- Level 3 enterprise high data protection – Microsoft recommends this configuration for devices run by an organization with a larger or more sophisticated security team, or for specific users or groups who are at uniquely high risk (as one example, one organization identified users who handle data whose theft would directly and seriously impact their stock price). An organization likely to be targeted by well-funded and sophisticated adversaries should aspire to this configuration.


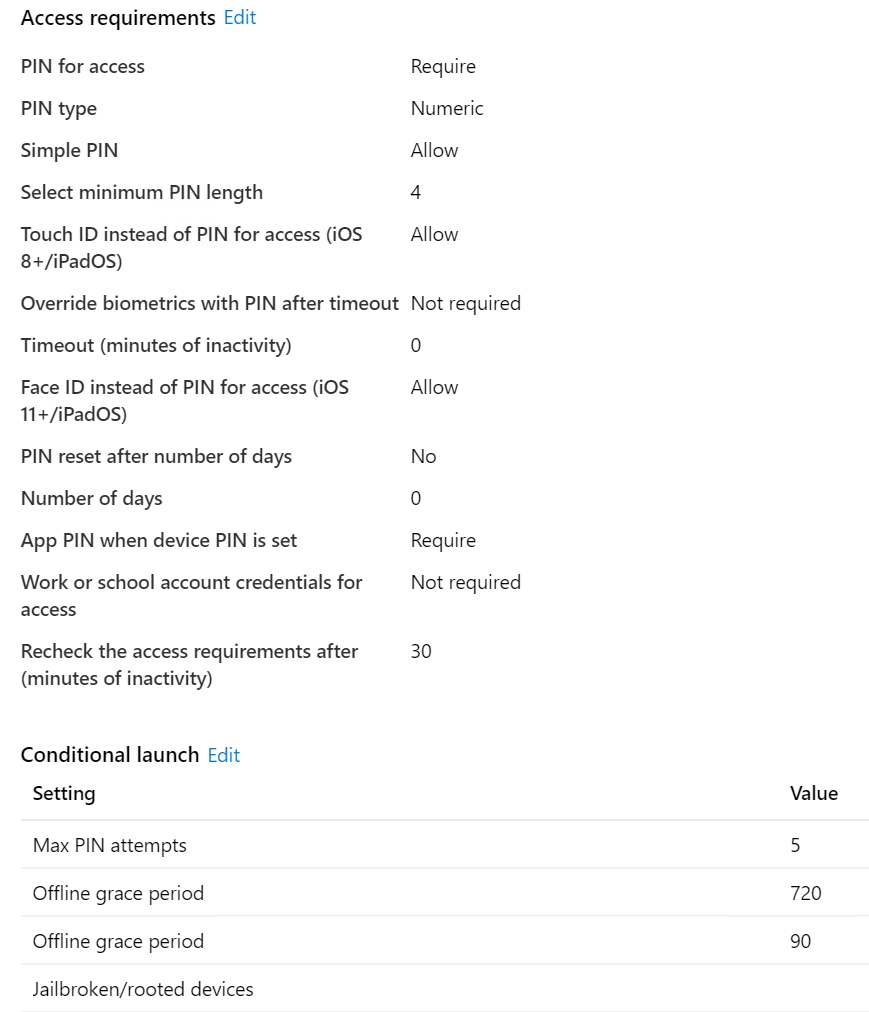
Access requirements: You can find this in: EndPoint Manager
- PIN for access: Require
- PIN type: Numeric
- Simple PIN Allow
- Select minimum PIN length 4
- Touch ID instead of PIN for access (iOS 8+/iPadOS): AllowOverride
- More details in the 3 screenshots for iOS. I’ve also created a policy for Android.
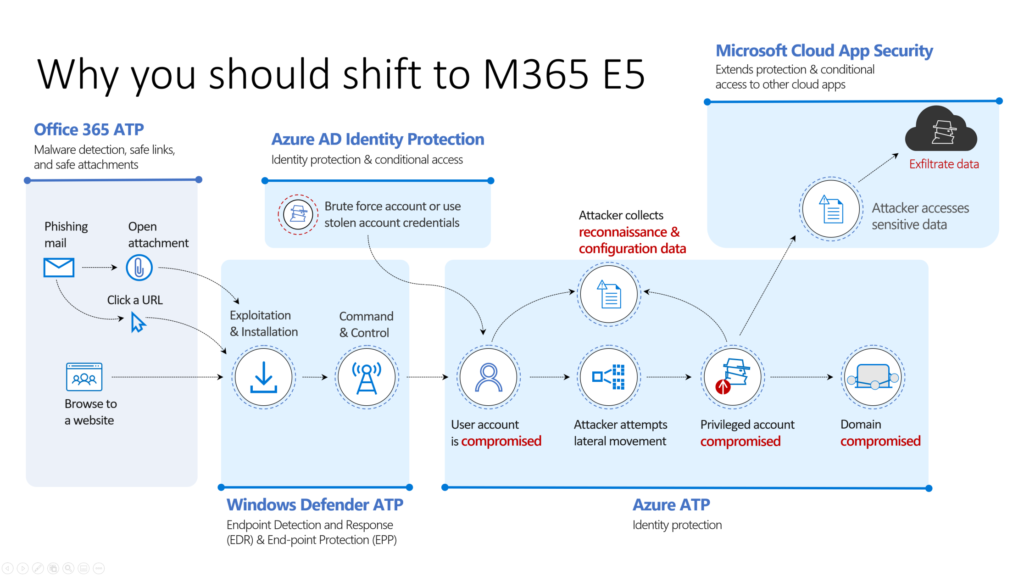
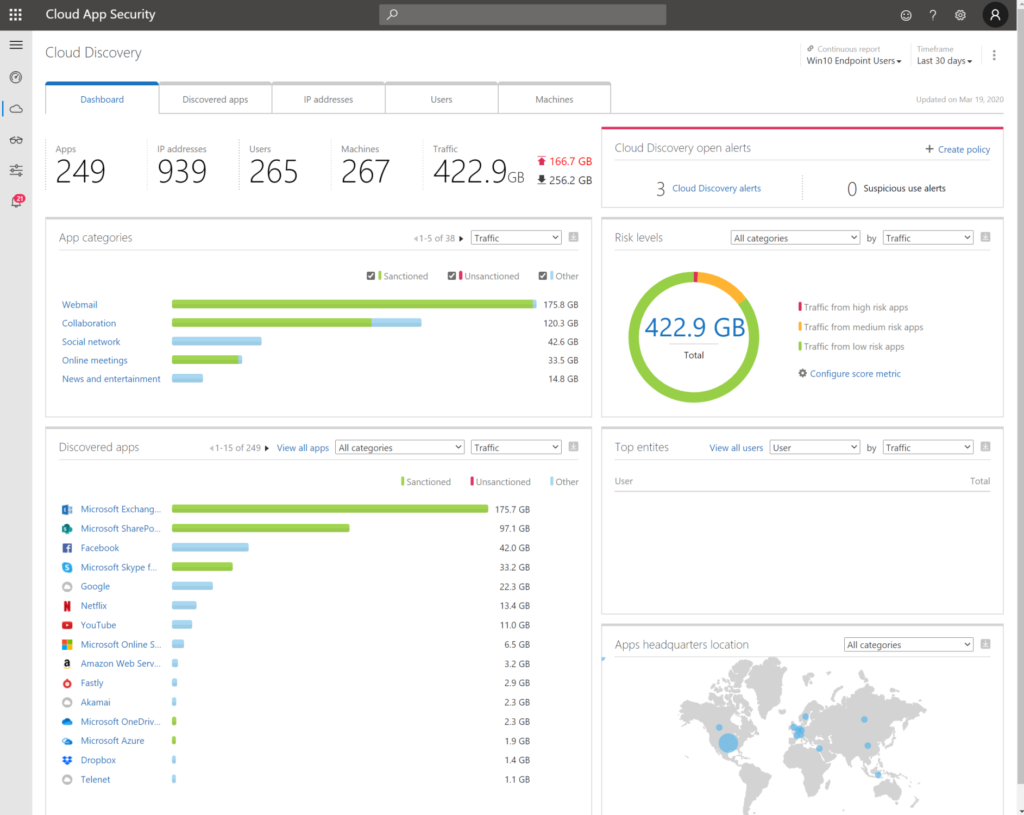
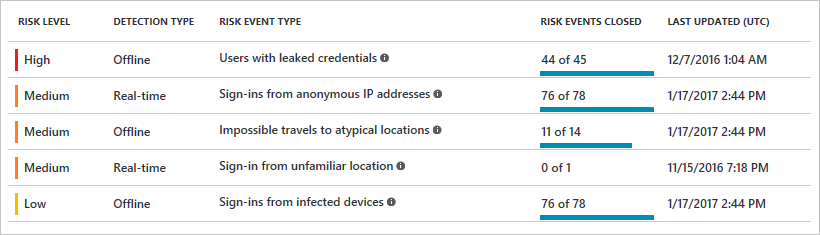
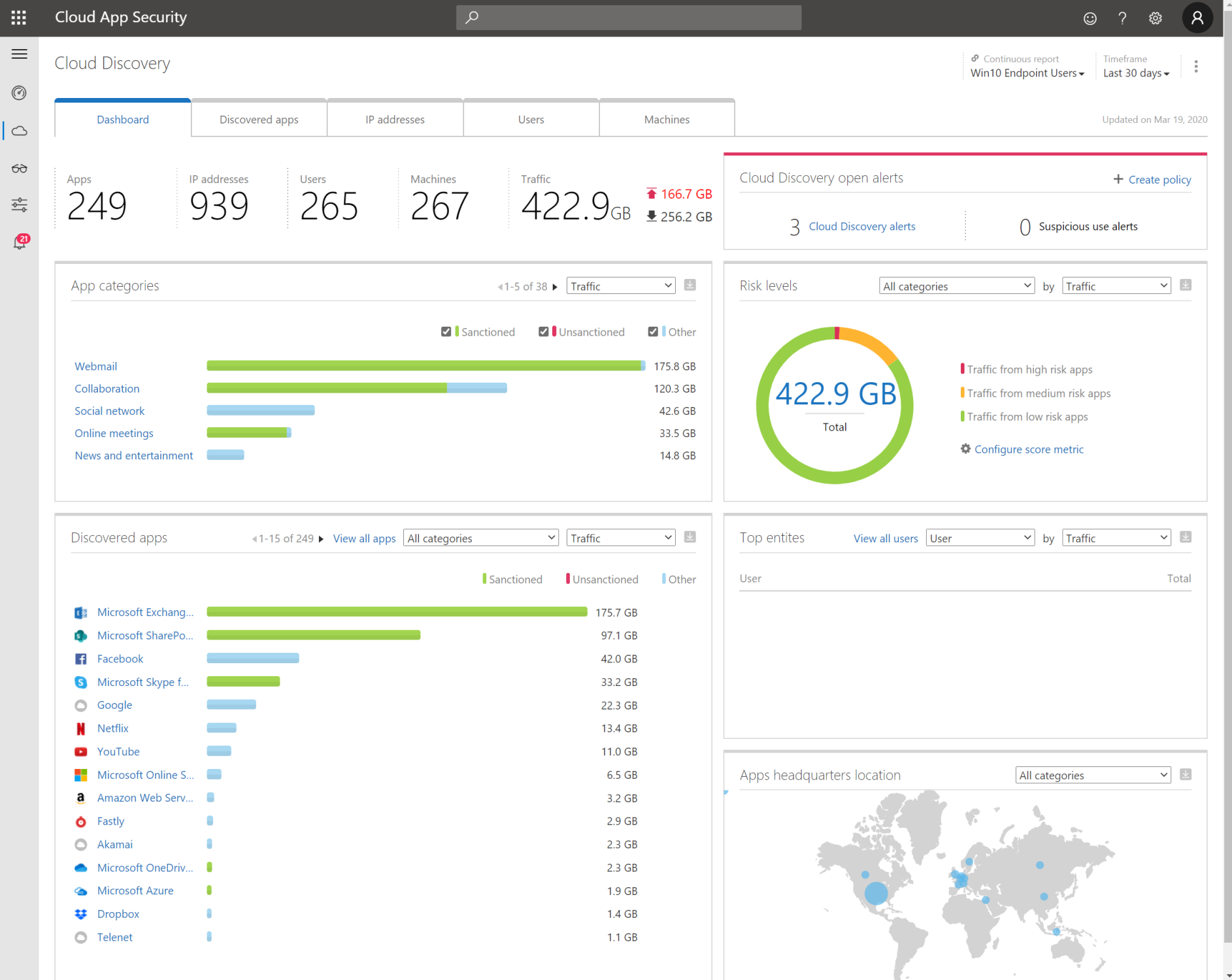
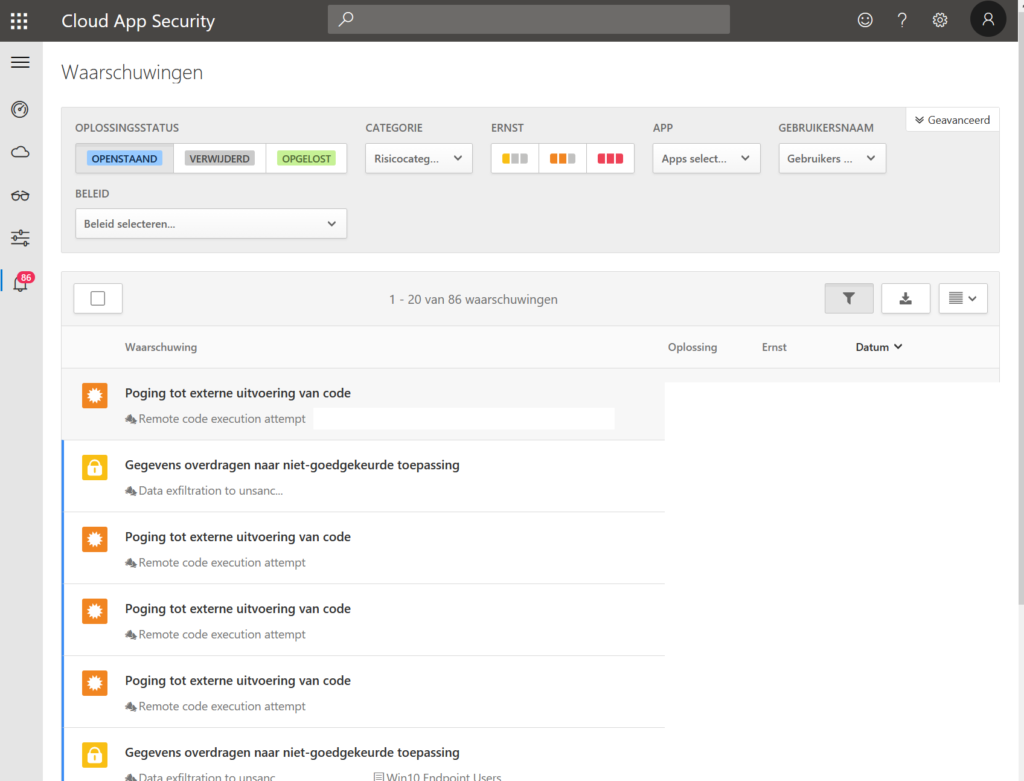
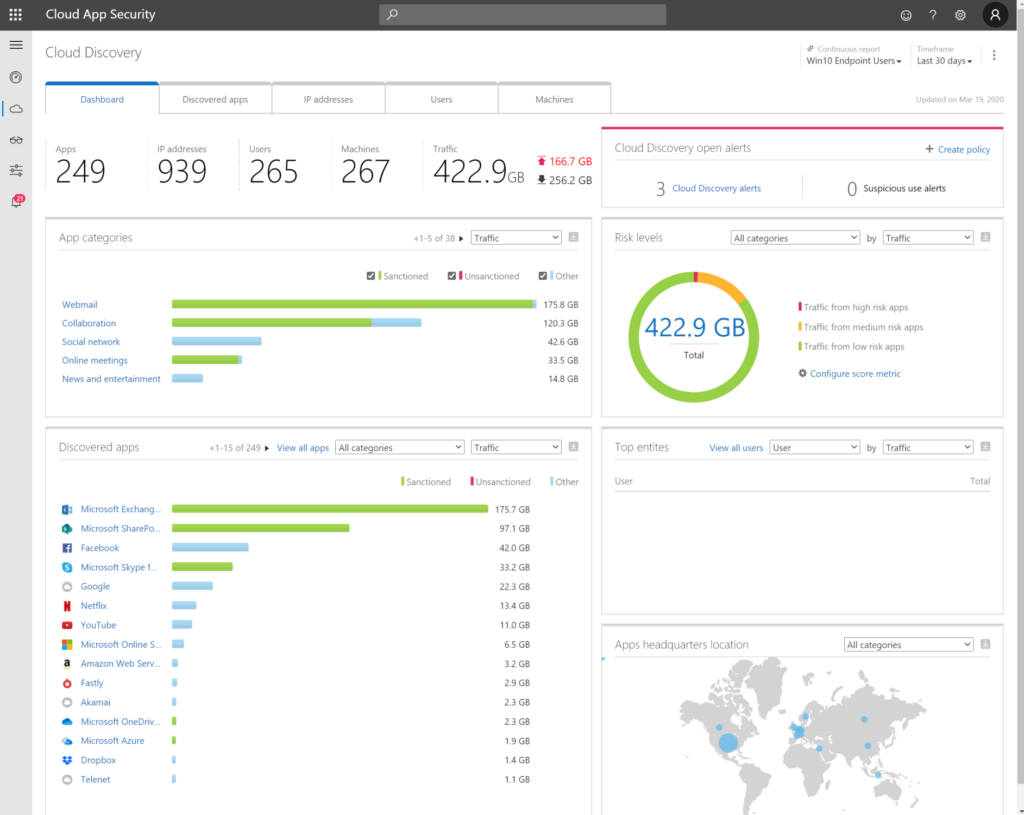
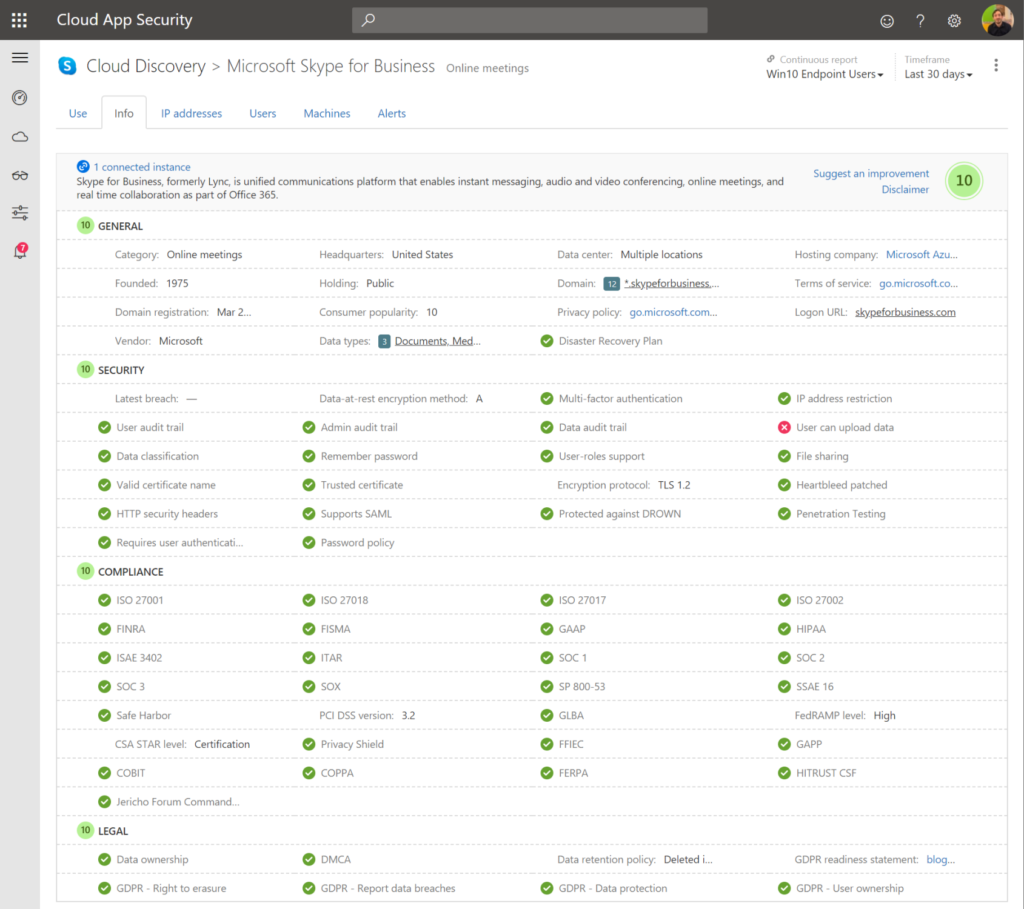
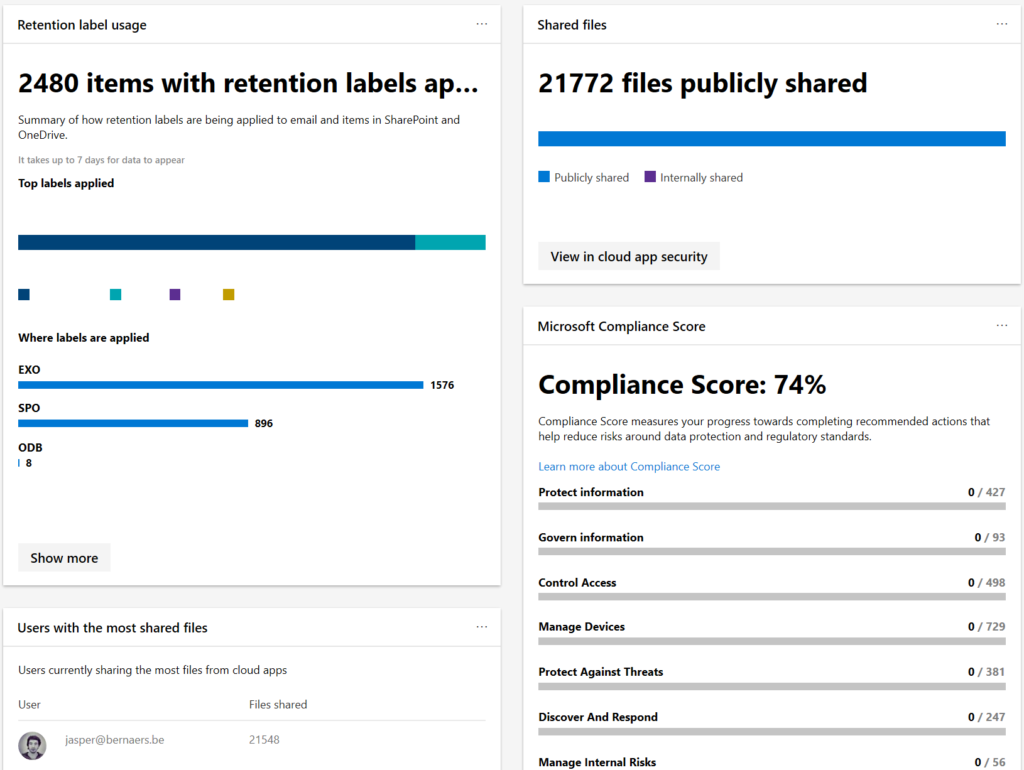
5. Knowing the risks with Cloud App Security
You’ve covered your identity, your Windows 10 devices. You’ve covered your non-trusted devices and your mobile devices. If there is something slipping in between activation or something is missing. I suggest to use Cloud App Security to see data exfiltration, etc..
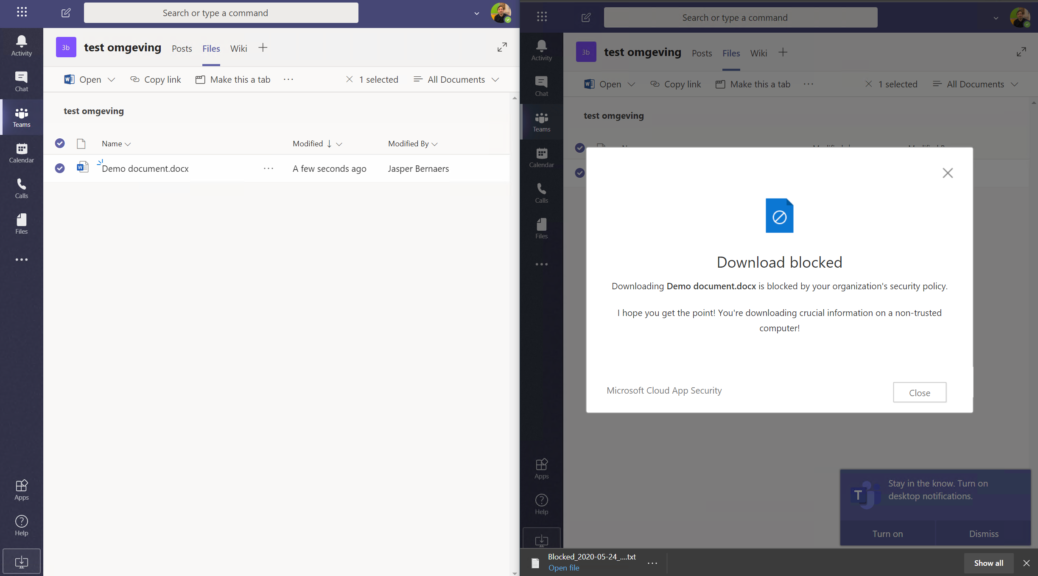
- As you can see in your Cloud App Security portal the ‘possibility’ to understand the block download policy is there.

- You can dig deeper to understand what happened. In the demo movie on the top I’ve showed left a trusted environment, on the right a non-trusted ‘personal computer’.

- You can go further with automation from here. But I will not go deeper into this in this article. Because I believe that if you have these 5 steps you have already achieved somethings.
Next steps?
- Identity protection(1) – automated remediation and creation of service-desk ticket to respond to your risky users.
- Compliance policies(2) – to not let devices slip under the fingers of IT-departments. You need a process to be sure all devices are passing the same process. And are totally blocked if not.
- Block downloads on non-trusted devices. (3) Go further, this implementation above is a great opportunity because of the easiness of implementation. Information protection is next. Because people can exfiltrate data when e-mailing, syncing, copying on their corp device, and their home device. And that’s a thing that should not be possible, anymore.
- Automate actions with CASB. Label your exfiltration expert. And create processes IF there is something wrong. The right people in the chain of command are informed.

- Next improvement is a future blog! Thanks for reading.