Protect apps with Microsoft Cloud App Security Conditional Access App Control
A lot of companies are struggling with data leakage when it comes to their exchange online environment. Easy fix! Enable: Microsoft Cloud App Security Conditional Access App Control! First, check the 7 seconds demo. It explains the unnecessary words!
Scenario:
- You have all your devices enabled in Microsoft’s endpoint manager aka Intune
- You are able to have an inventory and control of your hardware assets (CIS Control 1)
- You are using Office 365 or Microsoft 365.
- You don’t want users to download their e-mail attachments on a non-company owned device. (other scenario’s possible!)
Protect apps with Microsoft Cloud App Security Conditional Access App Control
It sounds so complex and i strongly believe this is making the implementations way to complex. So now the 2 Practical steps for the configuration.
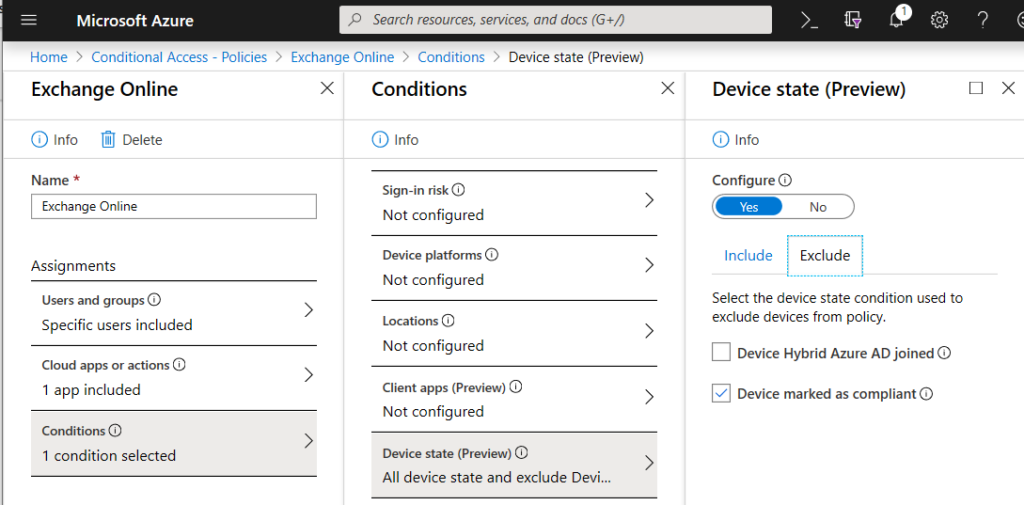
Step 1: Choose the cloud application – select the condition!
- Select cloud apps or actions: Microsoft Exchange
- Select a condition – IF your device is marked as compliant. Based on a intune policy that is able to CHECK if the device is compliant. Users are able to just go their way on Exchange Online.
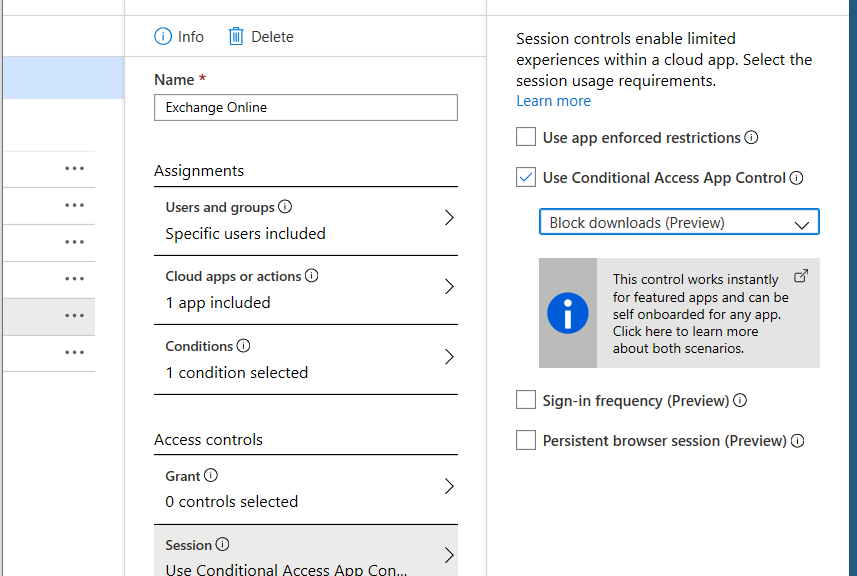
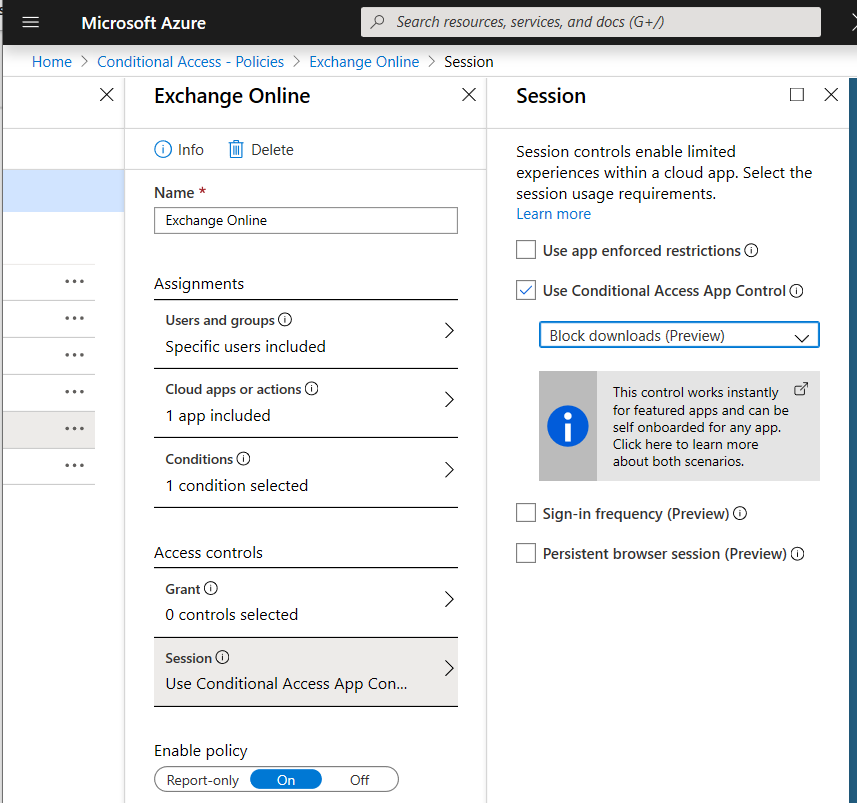
Step 2: select the Access Controls
- IF not they are not able to download attachments to their environment. Block downloads. That’s it!
By natively integrating with Azure AD, any app that is configured with SAML or Open ID Connect can be self-onboarded.
In addition, the following apps are featured by Cloud App Security and are already onboarded and ready to use in any tenant: More apps: Here
- Exchange Online
- OneDrive for Business
- Power BI
- SharePoint Online
- Microsoft Teams
Conclusions
- It’s not because you block attachment downloads in Exchange or OneDrive from non-company owned devices that your organization is good to go! This practical example shows the flexibility to get conditions in your organizations which can prevent leakage of data in e-mail systems.
- Blocking exchange download could shift that your organization will become aware they are still sending crucial information by mail which should be found in Microsoft Teams or SharePoint Online.
- Microsoft Information protection could play a big role in this configuration but this enablement can be a first step in security maturity growth.
- More options? YES: Notification when someone is downloading +10 documents, leaked credentials, impossible travel, File shared with unauthorized domain, New risky app, …