The Power of Proactive Threat Hunting [1/10]
At Wortell, we believe digital transformation only succeeds when security is embedded at the core. Technology should empower organizations to grow, collaborate, and innovate — but always with resilience and control.
That’s why our mission “We Empower People” is focused on enabling organizations to work securely and fearlessly. Our vision is centered around empowering organizations to grow, collaborate, and innovate and protected against modern threats.
We help them adopt Microsoft Cloud technologies in a way that’s measurable, sustainable, and protected against modern threats.
But today’s security landscape demands more than implementation. It demands constant vigilance, real-time visibility, and the ability to act decisively the moment something seems off.
To meet this challenge, we built our Managed Extended Detection & Response (MxDR) service. It combines the power of Microsoft’s native security tools with our own automation platform, Vidara. Together, they form a complete, intelligent security operations approach — one that scales across hybrid environments and adapts to evolving risks.
This article marks the start of a ten-week series in which I’ll explore how MxDR works, why it matters, and how it supports organizations in becoming more secure and resilient.
Each week, I’ll focus on one key theme. We begin with perhaps the most critical concept in modern detection: proactive threat hunting. – Can’t wait to hear what you’re thinking now. Feel free to reply in the comment!
Our Security Vision: https://www.wortell.nl/en/products/visie-managed-security
The Case for Threat Hunting
Modern cyberattacks don’t always announce themselves. In many cases, attackers enter a network quietly and stay hidden for weeks or months. They move laterally, gain access to privileged systems, and build persistence — often without triggering any traditional alerts.
The real question for organizations today is not whether a breach will occur, but whether it will be detected before it becomes damaging.
This is where proactive threat hunting plays its role. It’s a discipline that goes beyond dashboards and alerts. It’s about assuming compromise may already exist and asking the right questions:
• Where could someone hide in our environment?
• What behaviors are unusual but not yet flagged?
• What’s the difference between a system acting strange and a system being compromised?
Proactive threat hunting is built on the belief that some threats won’t reveal themselves unless someone actively looks for them. It requires experience, pattern recognition, and a deep understanding of the systems being protected.
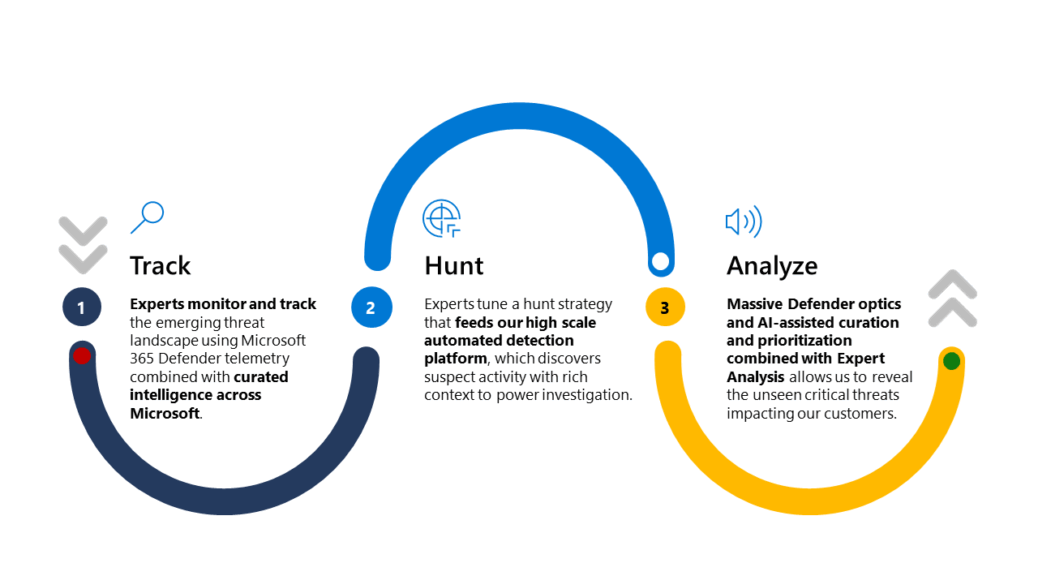
How We Hunt at Wortell
Wortell’s approach to threat hunting is deliberate, structured, and continuous. We combine Microsoft’s security ecosystem — including Microsoft Sentinel, Defender for Endpoint, and Defender for Identity — with our own advanced analytics and detection framework.
The foundation of this approach is our Vidara platform.
Vidara ingests real-time telemetry from the Microsoft stack, enriches it with threat intelligence, and applies contextual logic to spot early-stage anomalies. It connects behaviors across systems, identities, and endpoints, and helps our analysts prioritize what to investigate.
But automation is only part of the equation.
Our security team, operating from our Security Operation Center, uses Vidara as a lens to investigate weak signals, strange sequences of behavior, or subtle deviations from established patterns. The combination of human insight and machine learning leads to high-confidence findings — even when the signs of attack are barely visible.
To support this, we also deploy deception techniques. One example is our use of HoneyNet, a honeypot system that simulates vulnerable assets. If an attacker engages with it, it confirms their presence, reveals their tactics, and buys time to respond.
This method allows us to detect lateral movement, identity abuse, or command-and-control activity long before the attacker reaches their intended target.
Why It Matters
Proactive threat hunting changes the rhythm of cybersecurity. Instead of reacting to incidents after damage has begun, organizations can take control earlier — reducing the cost, complexity, and risk of response.
It also creates clarity. By continuously scanning for hidden threats, it provides assurance that the environment is not only monitored but actively challenged and tested.
Finally, it raises the standard. With a threat hunting mindset, organizations move from passive monitoring to active defense. It’s a strategic shift that requires investment, but the return — in peace of mind and operational resilience — is measurable.
Conclusion
Proactive threat hunting isn’t a feature or a tactic. It’s a mindset — one that aligns with the reality of today’s threat landscape.
At Wortell, we’ve made it a foundational part of our MxDR service. Supported by Microsoft’s security technologies and enhanced by Vidara, it enables us to detect threats early, respond faster, and reduce uncertainty for our customers.
In the next article, I’ll explore how rapid response transforms detection into decisive action — and how timing makes all the difference when an incident occurs.
Stay tuned.